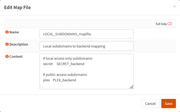
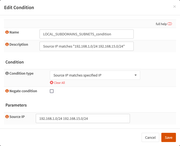
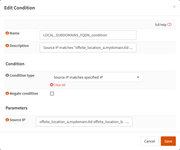
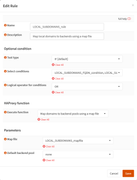
This post is dedicated to the moderators of this forum.
Sadly we are unable to directly see who they are so I have to create this topic.
It has come to my attention that this subforum is beeing used by many (mostly new) users to create topics about issues they are facing with OPNsense.
From the name of this subforum I had the assumption that it is solely dedicated to sharing tutorials / workarounds on how to achieve certain setups / configure plugins and so on.
However scrolling trough the list of topics makes me wanna cry because there are a lot of totally unrelated topics.
It would be nice if the moderators would step in there and delete such posts or move them to the corresponding subforums.
An alternative solution could be to not publish / keep hidden all new post of this subforum until a moderator approves them. And if the topic is not a tutorial or FAQ then either delete them with a notice to the poster or move them to the corresponding subforum.
Kind Regards
TheHellSite
Sadly we are unable to directly see who they are so I have to create this topic.
It has come to my attention that this subforum is beeing used by many (mostly new) users to create topics about issues they are facing with OPNsense.
From the name of this subforum I had the assumption that it is solely dedicated to sharing tutorials / workarounds on how to achieve certain setups / configure plugins and so on.
However scrolling trough the list of topics makes me wanna cry because there are a lot of totally unrelated topics.
It would be nice if the moderators would step in there and delete such posts or move them to the corresponding subforums.
An alternative solution could be to not publish / keep hidden all new post of this subforum until a moderator approves them. And if the topic is not a tutorial or FAQ then either delete them with a notice to the poster or move them to the corresponding subforum.
Kind Regards
TheHellSite

 "
"