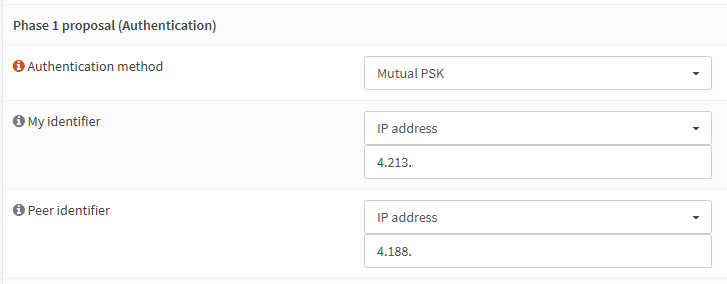
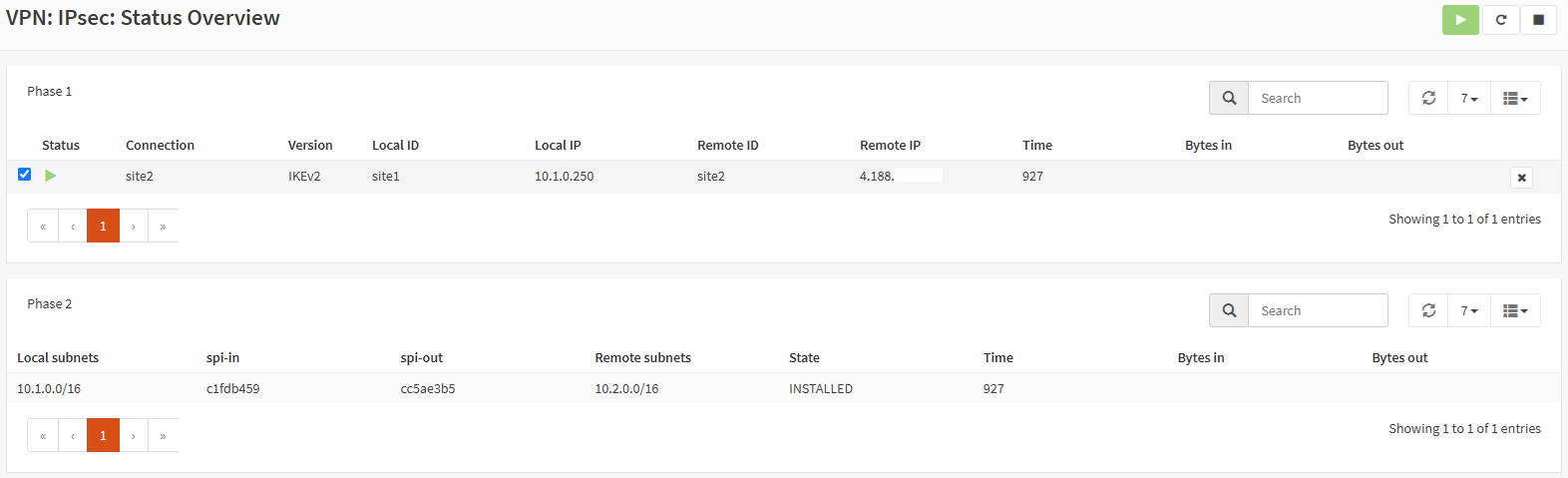
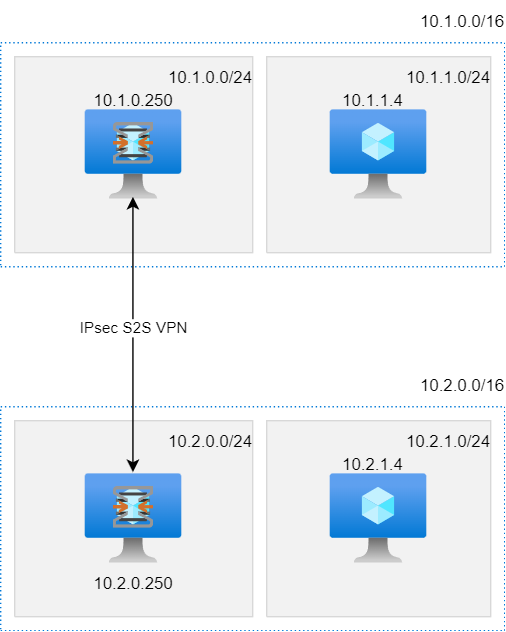
to close out this thread, I have just managed to get this to work.

A NAT rule was needed to get things to work as expected:

Thank you for your help and support

A NAT rule was needed to get things to work as expected:

Thank you for your help and support

 "
"