Quote from: rudiservo on August 13, 2022, 12:48:44 AMCode Selectpkg remove php74-pecl-mongodb
I also had this problem, but uninstalling the package was the solution. Thank you very much!
This section allows you to view all posts made by this member. Note that you can only see posts made in areas you currently have access to.
Show posts MenuQuote from: rudiservo on August 13, 2022, 12:48:44 AMpkg remove php74-pecl-mongodb
Quote
17.03.2022:
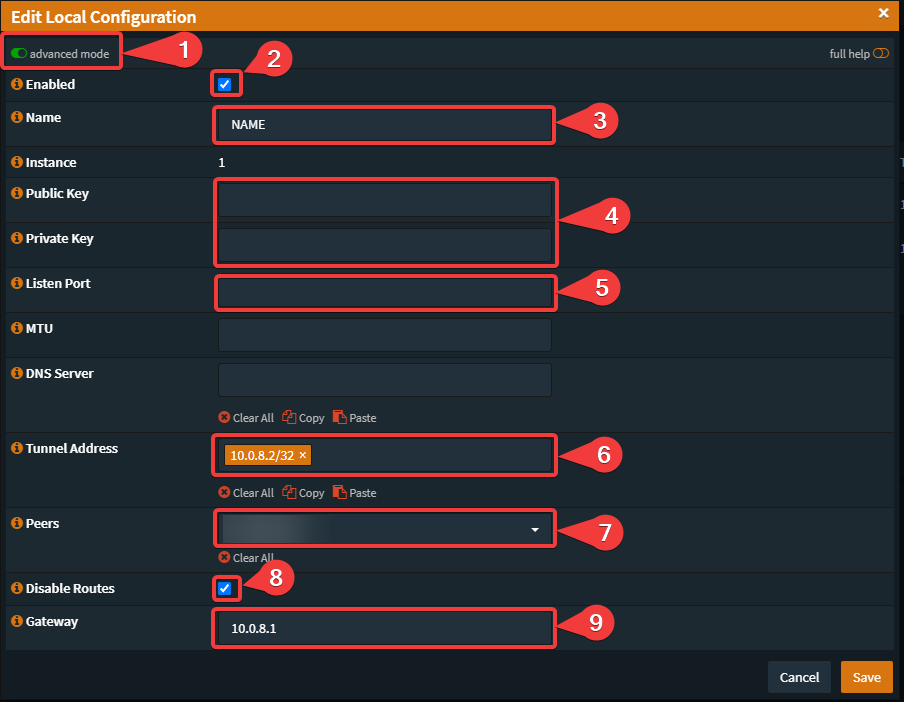
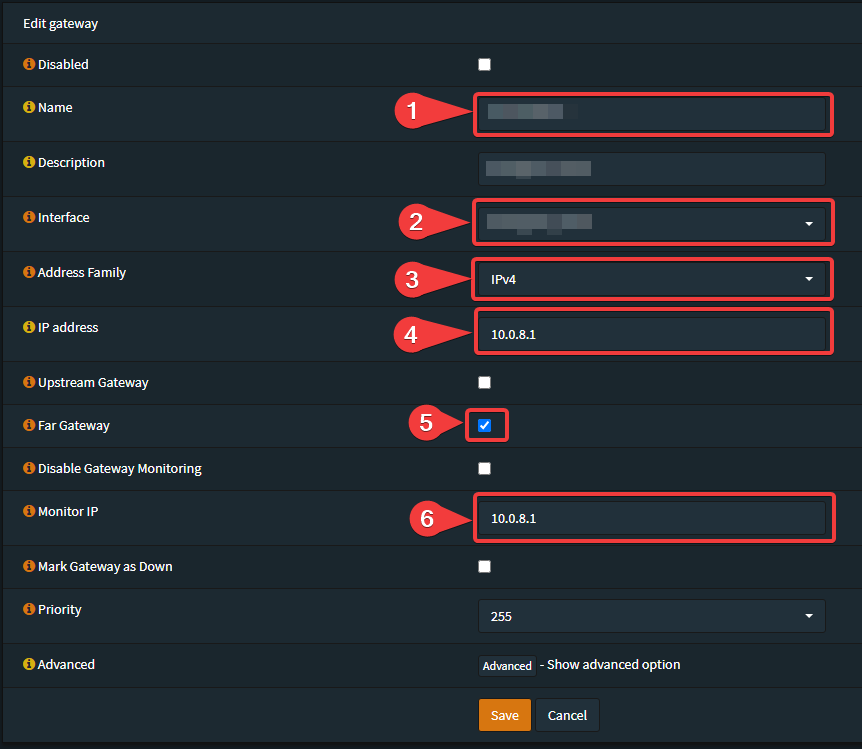
- Changed the Gateway-Address from local WG-Address to the remote WG-Address (Local WG-Gateway), as described in the official manual.
- Fixed some typos an formatting
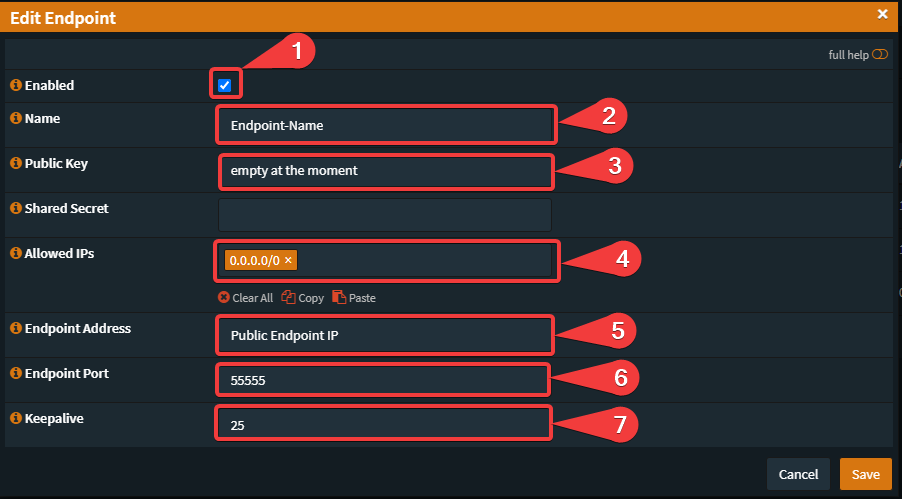
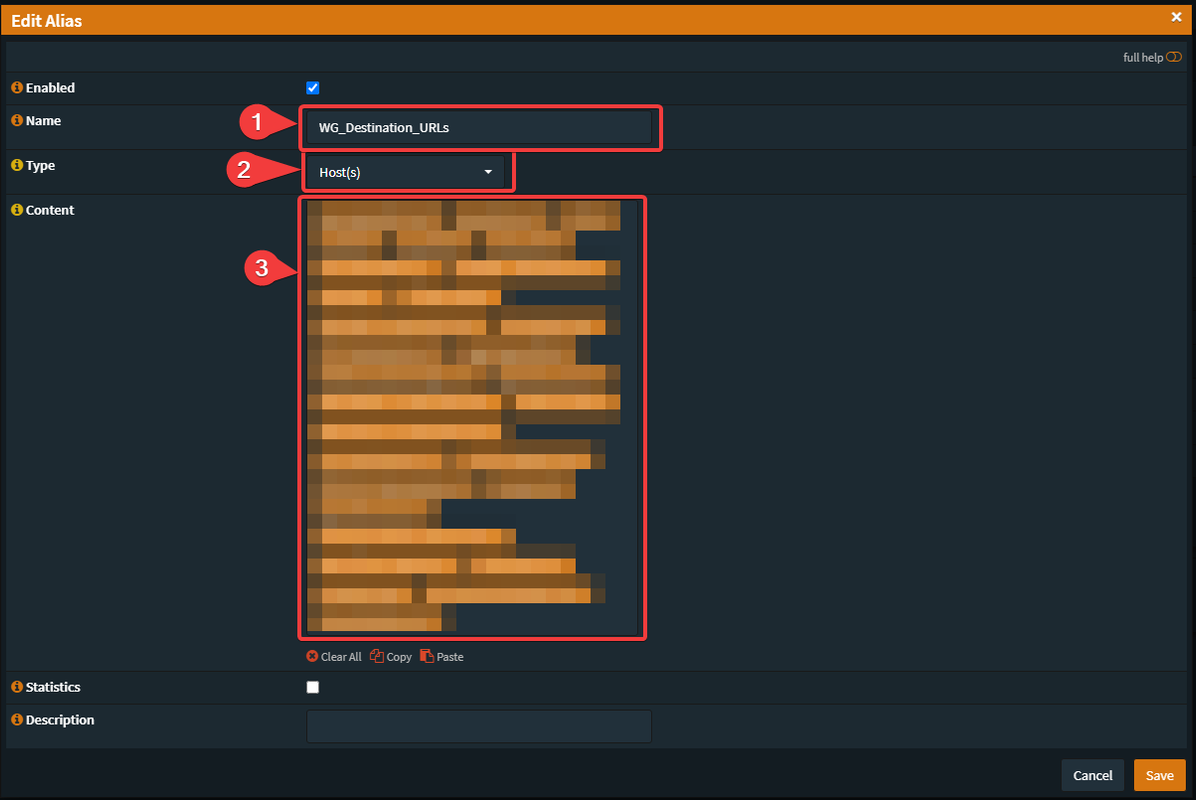
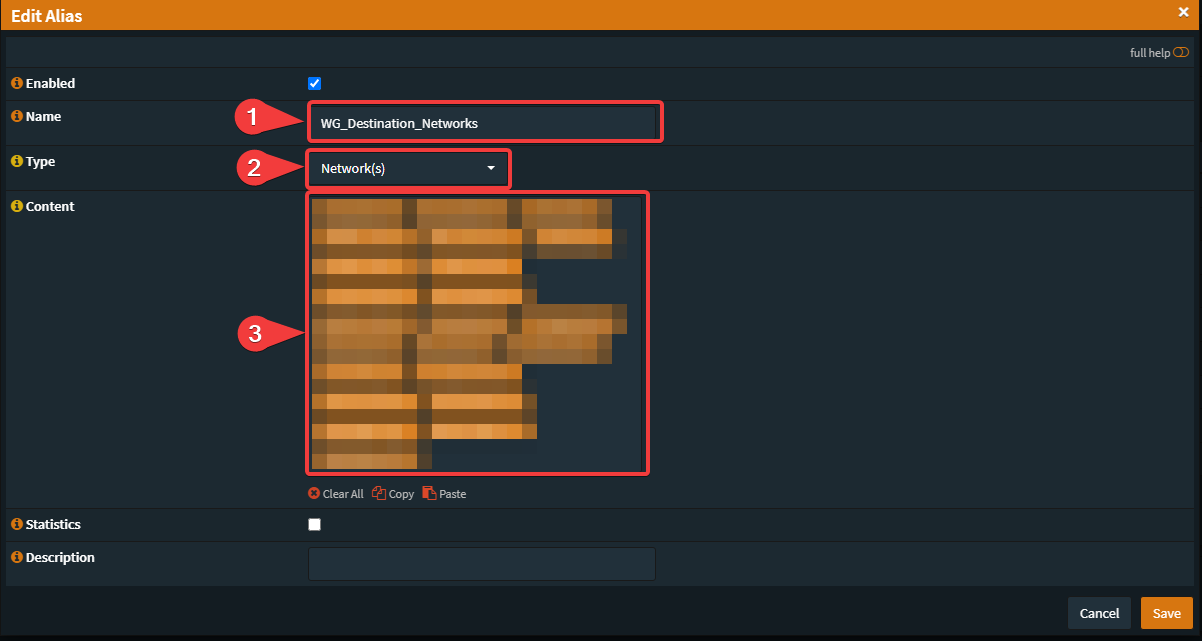
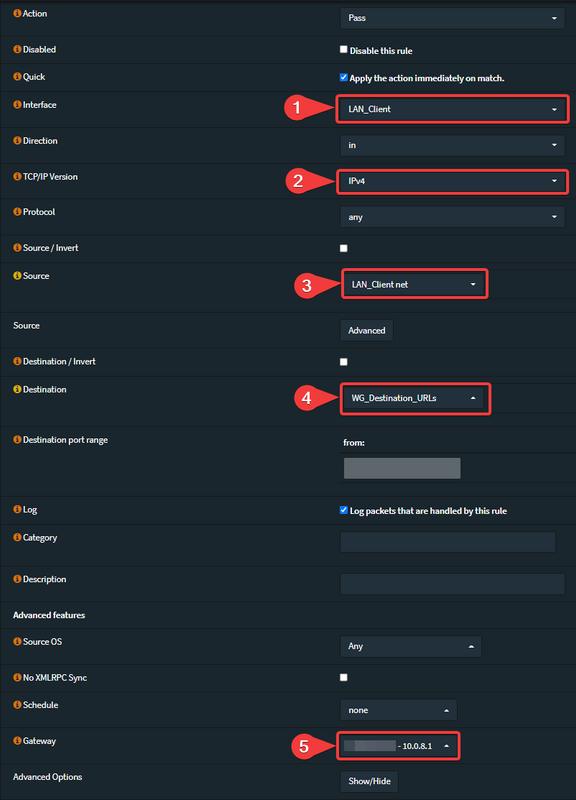
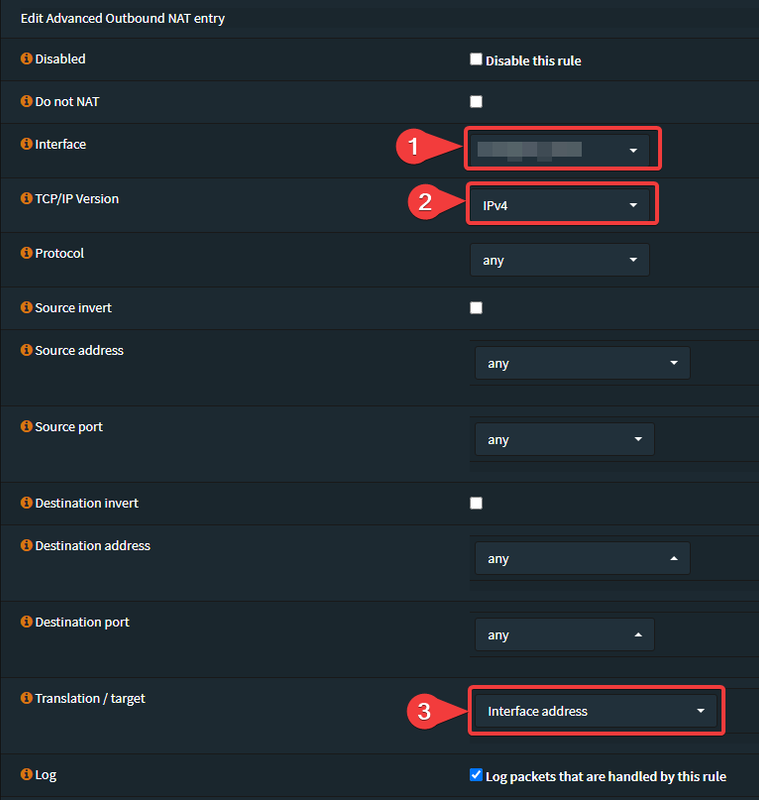
dnf install epel-release -ydnf install kmod-wireguard wireguard-tools -ymkdir /etc/wireguardumask 077wg genkey | tee /etc/wireguard/wireguard.key | wg pubkey > /etc/wireguard/wireguard.pub.keycat /etc/wireguard/wireguard.keyvi /etc/wireguard/wg0.conf[Interface]
ListenPort = 55555
PrivateKey = [PrivateKey from the Endpoint/this Machine]
Address = 10.0.8.1/32
PreUp = iptables -t nat -A POSTROUTING -o eth0 -j MASQUERADE
PreUp = iptables -A FORWARD -p tcp --tcp-flags SYN,RST SYN -j TCPMSS --clamp-mss-to-pmtu
PostDown = iptables -t nat -D POSTROUTING -o eth0 -j MASQUERADE
PostDown = iptables -D FORWARD -p tcp --tcp-flags SYN,RST SYN -j TCPMSS --clamp-mss-to-pmtu
[Peer]
PublicKey = [PublicKey from OPNsense-Wireguard]
AllowedIPs = 10.0.8.2/32echo "net.ipv4.ip_forward = 1" >> /etc/sysctl.confsysctl -pcat /etc/wireguard/wireguard.pub.key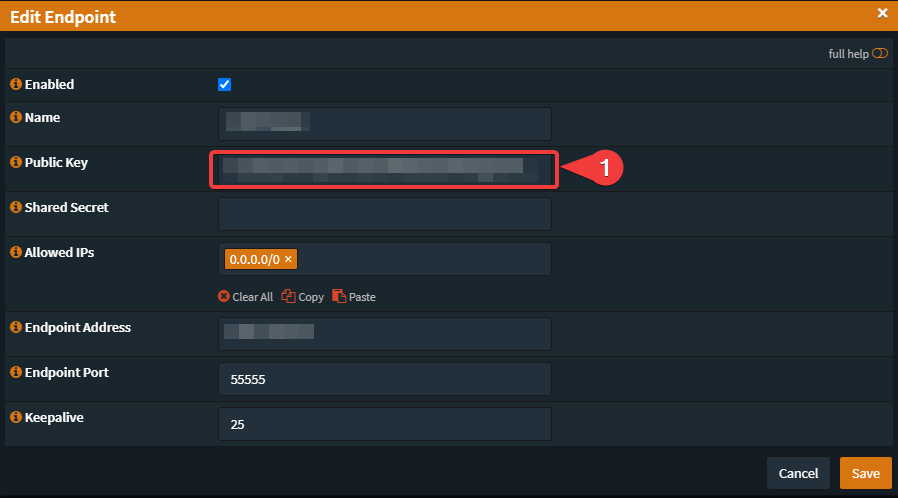
wg-quick up wg0wg-quick down wg0wg-quick up wg0wgsystemctl start wg-quick@wg0systemctl enable wg-quick@wg0