Introduction
In the following I would like to show how I have set up "Selective Routing" via Wireguard. Primarily to access websites with region lock or to hide my real public IP.
For that, I have an Azure VM, which is located in the appropriate country. This VM can also be from another provider.
This manual is basically based on: https://docs.opnsense.org/manual/how-tos/wireguard-selective-routing.html
Tested and working on OPNsense 22.1.2_1
Changelog
Requirements
Configuration: OPNsense
Create Endpoint
Go to: VPN -> Wireguard -> Endpoints -> + (create new)
Create Local Configuration
Click on "Edit" (Pencil) and copy the new generated Public Key to a .txt-File or similar.
Create new Interface
Go to: Interfaces -> Assignments
Go to: Interfaces -> [NEW-WG-INTERFACE]
Create a Gateway
Go to: System -> Gateways -> Single
Create Aliases (Destination URLs, Networks)
Go to: Firewall -> Aliases -> Add (create new alias)
In my case, certain services are loaded from my accessed website via a CDN, which is why I also need to enter all the subnets used by the CDN. If this is not the case for you, you can simply create a URL alias and skip creating a network alias.
URL:
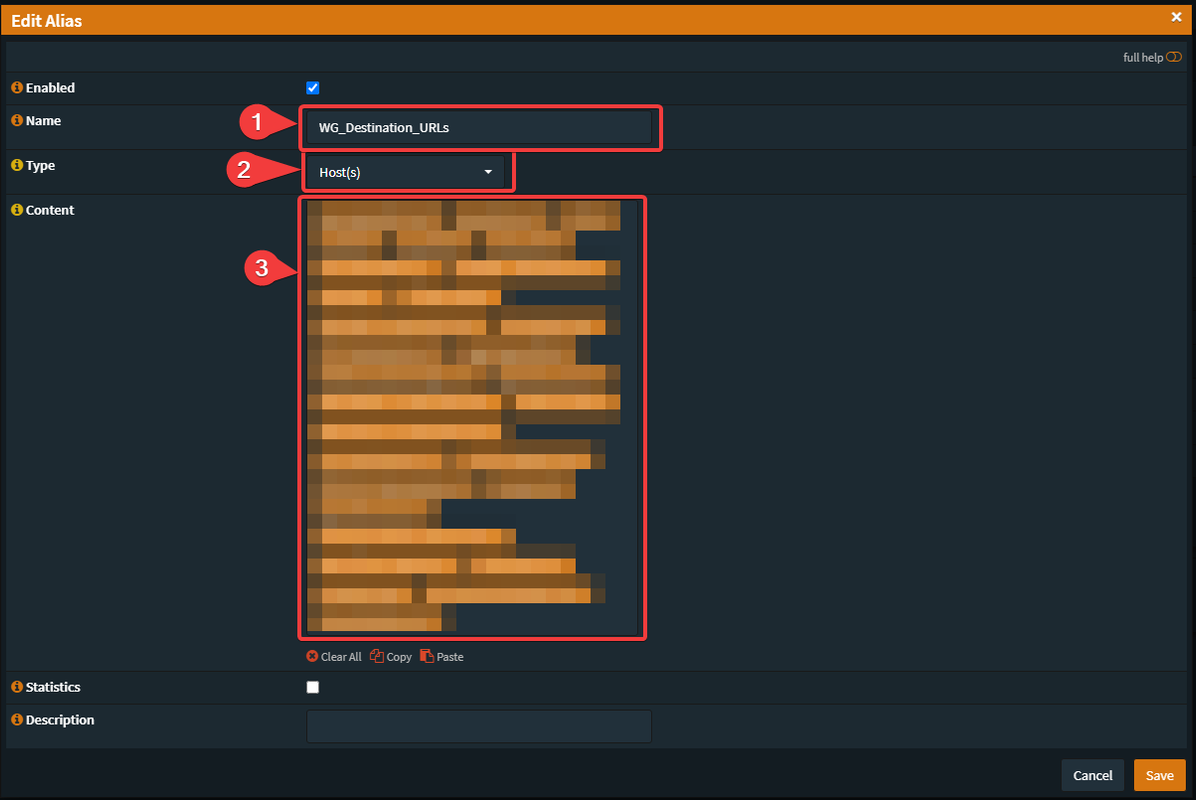
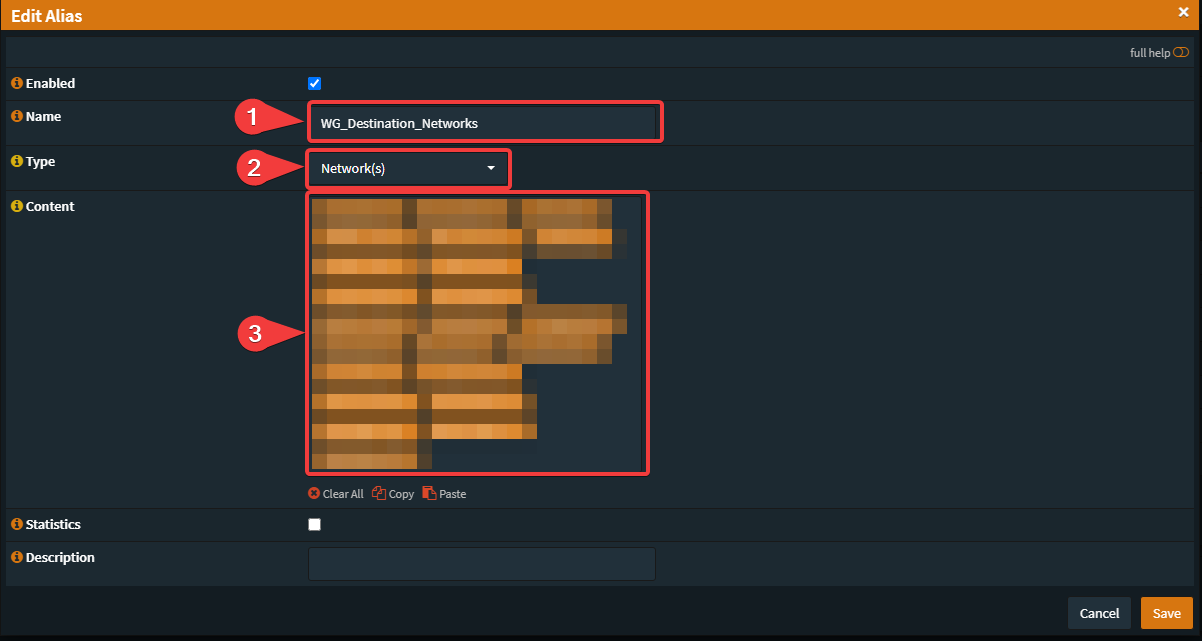
Networks:
Firewall Rules
In my case the complete internal network should run through my wireguard endpoint when accessing my "region block website".
If you don't want to do that over the whole network, you can also create an alias for the affected IPs/hosts and specify them as "source" later. in the Rule-Creation.
Go to: Firewall -> Rules -> [LAN-Interface] -> Add (create new rule)
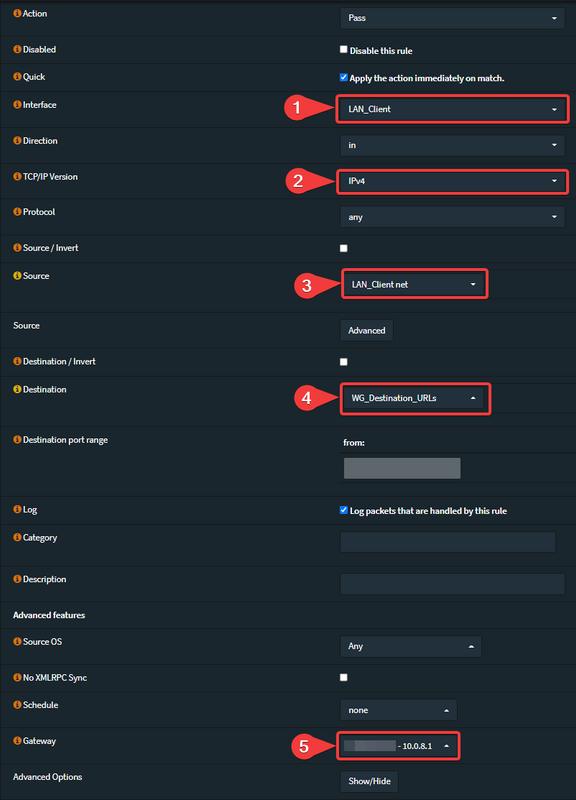
If you have also created a Network-Alias like me, this just created firewall rule needs to be copied and the destination (4) needs to be adjusted to this alias. After that "Save" and "Apply" again.
NAT Configuration
The NAT is only needed if you also want to access the endpoint host itself!
Go to: Firewall -> NAT -> Outbound
Select "Hybrid NAT..."
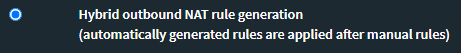
Add a new "Manual rule":
Now we are basically done with the configuration on the OPNsense side. We only have to enter the PublicKey of the Wireguard endpoint later.
Configure: Rocky Linux / Wireguard-Endpoint
At this point you can use any Linux/BSD distribution as long as iptables and wireguard are available for it.
However, only the procedure on RockyLinux is described here.
Installation prerequisites / Wireguard
Install Epel-Release:
Install Wireguard:
Create WireGuard Configuration Directory
Generate WireGuard Private/Public Keys
Change Permissions:
Generate and write a new private and a public key to a file:
Copy the created private key and write it temporary somewhere down:
Create a new Wireguard-Configfile:
Paste the following lines to this file:
Note that on my interface eth0 the gateway is defined. This may be different for you. Change it accordingly in the lines "PreUp" and "PostDown".
Save the File (vi = :wq)
Enable IP-Forwarding
Copy the public key to OPNsense
Copy the created public key and write it temporary somewhere down:
Go back to your OPNsense WebGUI
Go to: VPN -> Wireguard -> Endpoints -> Edit your prevoiusly created config
Start Wireguard on the Endpoint
Go back to your Endpoint and start your Wireguard-Tunnel:
If your tunnel is already running, do:
You can check if the tunnel is up and running:
Create a service
Summary
Now we are ready and you can test/use your configuration.
In the following I would like to show how I have set up "Selective Routing" via Wireguard. Primarily to access websites with region lock or to hide my real public IP.
For that, I have an Azure VM, which is located in the appropriate country. This VM can also be from another provider.
This manual is basically based on: https://docs.opnsense.org/manual/how-tos/wireguard-selective-routing.html
Tested and working on OPNsense 22.1.2_1
Changelog
Quote
17.03.2022:
- Changed the Gateway-Address from local WG-Address to the remote WG-Address (Local WG-Gateway), as described in the official manual.
- Fixed some typos an formatting
Requirements
- Wireguard Plugin installed (on OPNsense)
- Endpoint with fixed, public IP
- Endpoint OS: RockyLinux 8.5
Configuration: OPNsense
Create Endpoint
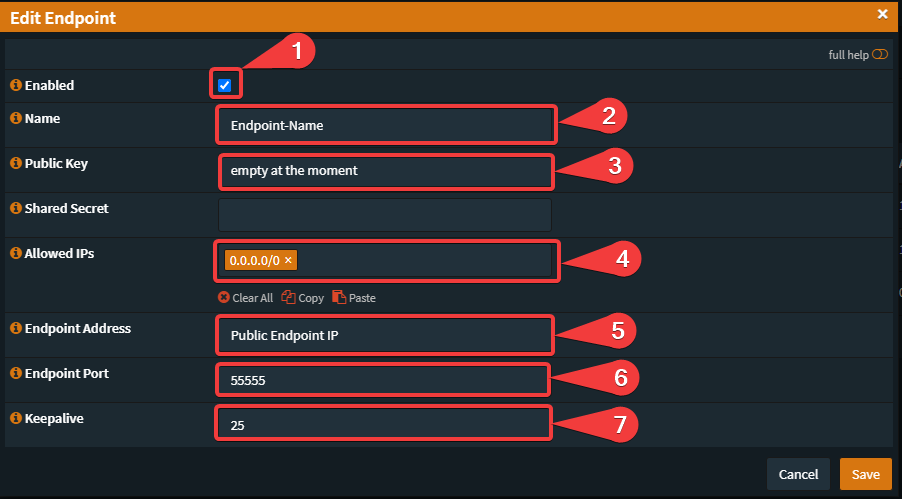
Go to: VPN -> Wireguard -> Endpoints -> + (create new)

- Set "Enable"
- Your prefered Name
- Keep this field empty
- Insert: 0.0.0.0/0 (for IPv6: ::/0
- Insert the Public IP from your Endpoint
- Any Port you want to use
- Since this is supposed to be a persistent connection, set the keepalive to 25
Create Local Configuration

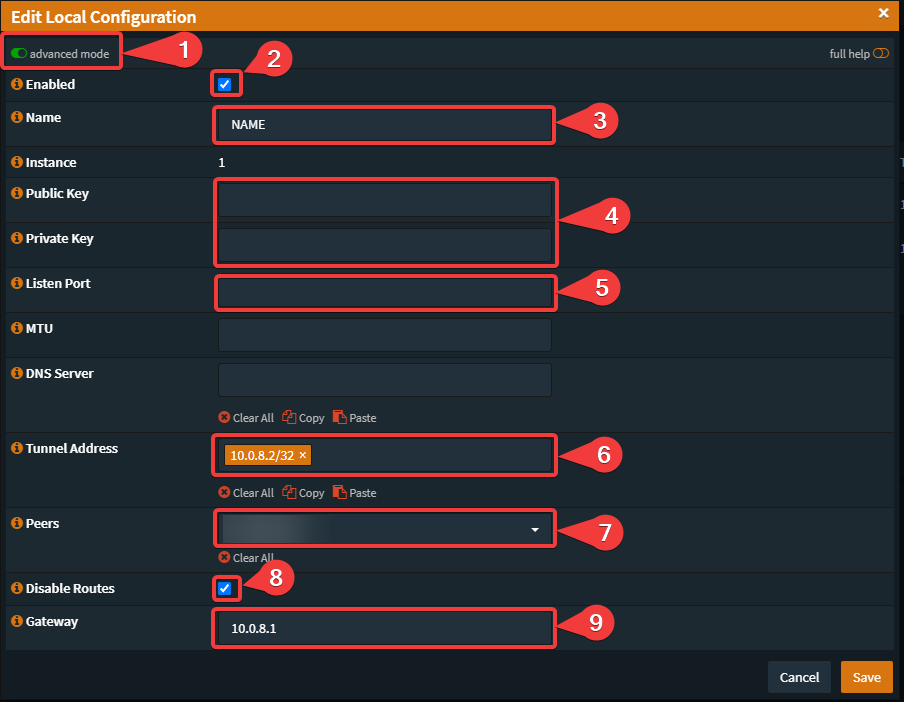
- Enable "advanced mode"
- Set "Enable"
- Your prefered Name
- Keep this fields empty
- In this case we don't need a Listening-Port
- Set the Tunnel Address x.x.x.x/32
- Select the previously created Endpoint
- Select "Disable Routes"
- Choose any Gateway-IP in the same Range as the Tunnel Adress in /24
Click on "Edit" (Pencil) and copy the new generated Public Key to a .txt-File or similar.
Create new Interface
Go to: Interfaces -> Assignments
- Assign the new created Wireguard interface
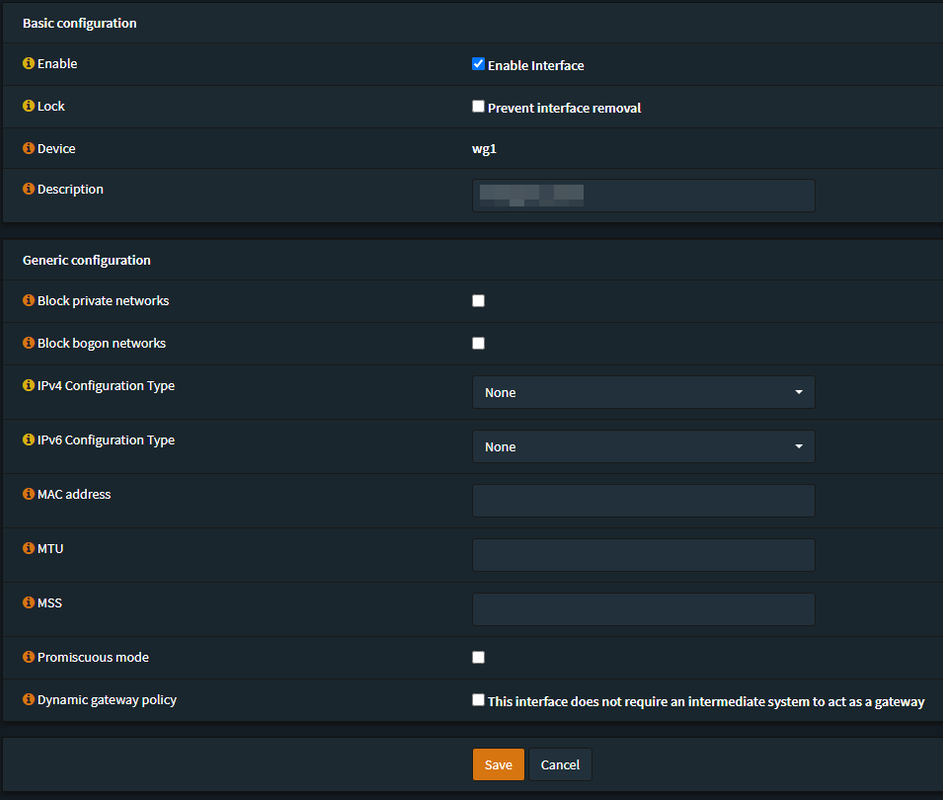
Go to: Interfaces -> [NEW-WG-INTERFACE]
- Set everything as on the screenshot and click on "Save"

- Now restart WireGuard - you can do this from the Dashboard (if you have the services widget) or by turning it off and on under VPN -> WireGuard -> General
Create a Gateway
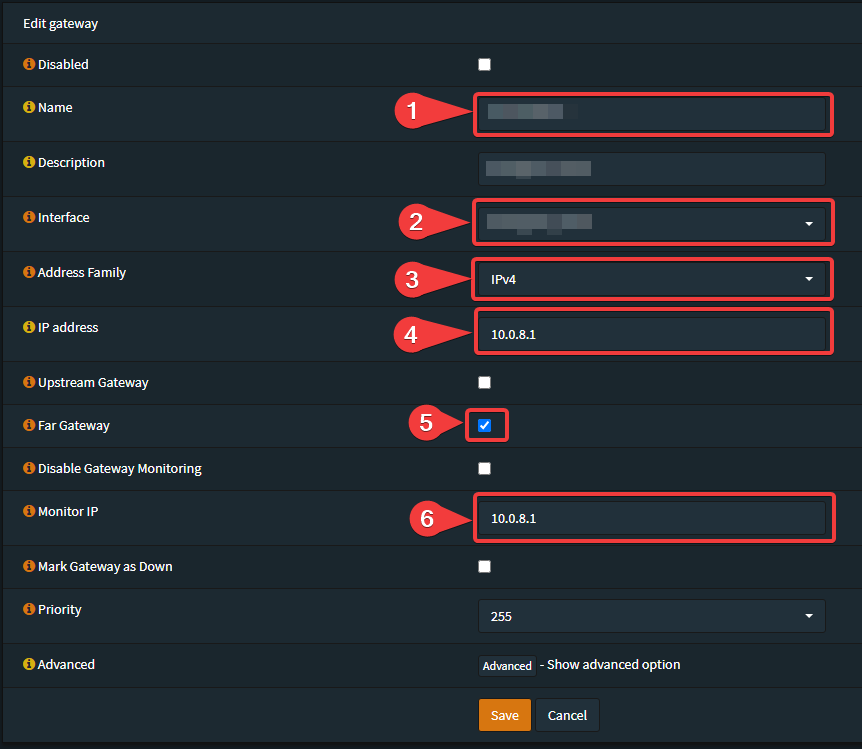
Go to: System -> Gateways -> Single

- Your prefered Name
- Select your [NEW-WG-INTERFACE]
- Select IPv4
- Enter the gateway IP that you configured under the WireGuard local peer configuration
- Select "Far Gateway"
- Enter the Gateway IP from your Local Wireguard Configuration
Create Aliases (Destination URLs, Networks)
Go to: Firewall -> Aliases -> Add (create new alias)
In my case, certain services are loaded from my accessed website via a CDN, which is why I also need to enter all the subnets used by the CDN. If this is not the case for you, you can simply create a URL alias and skip creating a network alias.
URL:

- Your prefered Name
- Select "Host(s)"
- Enter every single used Hostname/FQDN, because OPNsense isn't supporting Wildcard.
(e.g. www.google.com, google.com)
Networks:

- Your prefered Name
- Select "Network(s)"
- Enter every used subnet
Firewall Rules
In my case the complete internal network should run through my wireguard endpoint when accessing my "region block website".
If you don't want to do that over the whole network, you can also create an alias for the affected IPs/hosts and specify them as "source" later. in the Rule-Creation.
Go to: Firewall -> Rules -> [LAN-Interface] -> Add (create new rule)

- Select your LAN-Interface
- Select "IPv4"
- Select your LAN-Network (net) or your defined IPs/Hosts-Alias
- Select your defined URL-Alias
- Select your defined Gateway
If you have also created a Network-Alias like me, this just created firewall rule needs to be copied and the destination (4) needs to be adjusted to this alias. After that "Save" and "Apply" again.
NAT Configuration
The NAT is only needed if you also want to access the endpoint host itself!
Go to: Firewall -> NAT -> Outbound
Select "Hybrid NAT..."

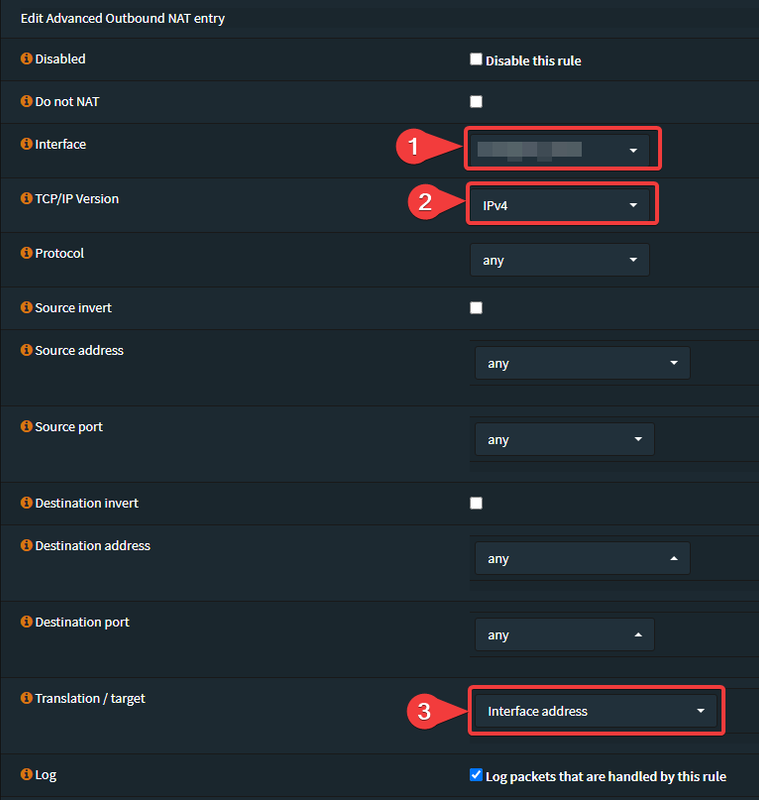
Add a new "Manual rule":

- Select your Wireguard-Interface
- Select "IPv4"
- Set Translation to "Interface address"
Now we are basically done with the configuration on the OPNsense side. We only have to enter the PublicKey of the Wireguard endpoint later.
Configure: Rocky Linux / Wireguard-Endpoint
At this point you can use any Linux/BSD distribution as long as iptables and wireguard are available for it.
However, only the procedure on RockyLinux is described here.
Installation prerequisites / Wireguard
Install Epel-Release:
Code Select
dnf install epel-release -yInstall Wireguard:
Code Select
dnf install kmod-wireguard wireguard-tools -yCreate WireGuard Configuration Directory
Code Select
mkdir /etc/wireguardGenerate WireGuard Private/Public Keys
Change Permissions:
Code Select
umask 077Generate and write a new private and a public key to a file:
Code Select
wg genkey | tee /etc/wireguard/wireguard.key | wg pubkey > /etc/wireguard/wireguard.pub.keyCopy the created private key and write it temporary somewhere down:
Code Select
cat /etc/wireguard/wireguard.keyCreate a new Wireguard-Configfile:
Code Select
vi /etc/wireguard/wg0.confPaste the following lines to this file:
Code Select
[Interface]
ListenPort = 55555
PrivateKey = [PrivateKey from the Endpoint/this Machine]
Address = 10.0.8.1/32
PreUp = iptables -t nat -A POSTROUTING -o eth0 -j MASQUERADE
PreUp = iptables -A FORWARD -p tcp --tcp-flags SYN,RST SYN -j TCPMSS --clamp-mss-to-pmtu
PostDown = iptables -t nat -D POSTROUTING -o eth0 -j MASQUERADE
PostDown = iptables -D FORWARD -p tcp --tcp-flags SYN,RST SYN -j TCPMSS --clamp-mss-to-pmtu
[Peer]
PublicKey = [PublicKey from OPNsense-Wireguard]
AllowedIPs = 10.0.8.2/32Note that on my interface eth0 the gateway is defined. This may be different for you. Change it accordingly in the lines "PreUp" and "PostDown".
Save the File (vi = :wq)
Enable IP-Forwarding
Code Select
echo "net.ipv4.ip_forward = 1" >> /etc/sysctl.confCode Select
sysctl -pCopy the public key to OPNsense
Copy the created public key and write it temporary somewhere down:
Code Select
cat /etc/wireguard/wireguard.pub.keyGo back to your OPNsense WebGUI
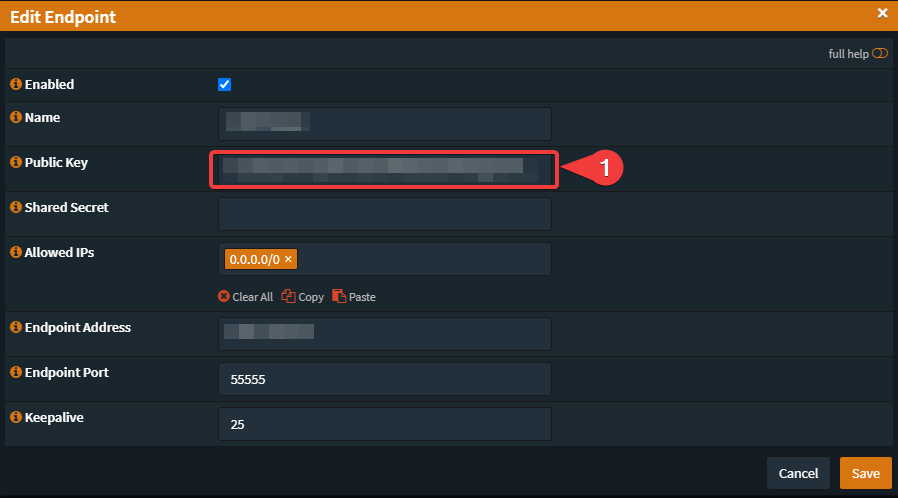
Go to: VPN -> Wireguard -> Endpoints -> Edit your prevoiusly created config

- Paste the public key into the "Public Key"-field
Start Wireguard on the Endpoint
Go back to your Endpoint and start your Wireguard-Tunnel:
Code Select
wg-quick up wg0If your tunnel is already running, do:
Code Select
wg-quick down wg0Code Select
wg-quick up wg0You can check if the tunnel is up and running:
Code Select
wgCreate a service
Code Select
systemctl start wg-quick@wg0Code Select
systemctl enable wg-quick@wg0Summary
Now we are ready and you can test/use your configuration.

 "
"
