Monit is a software that can check your filesystems, disks, processes, system and many more.
It runs on the firewall host and sends messages or executes actions on various events.
With the os-monit plugin you can configure the Monit daemon.
Installation
To use Monit install the os-monit plugin first. It installs the monit package as a dependency.
After the installation has finished reload the GUI and navigate to Services->Monit->Settings.
Configuration
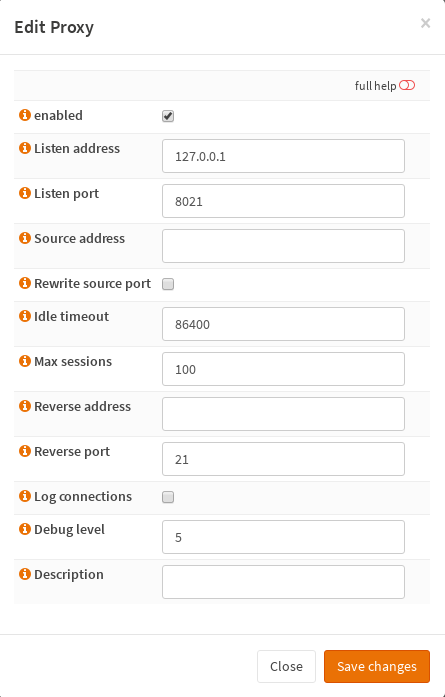
The first step is to check if the plugin installer has imported your System->Notification settings correctly. Then have a look at the other tabs. To help you get acquainted the installer has added some standard entries.
The order to configure a monitoring is to create Service Tests first, then Services to check and in the end Alerts.
Let's start with the Service Test Settings. A test contains a condition and an action. It can be assigned to one or more services. The Monit documentation shows possible tests. You can simply adopt it by omitting the IF and THEN statements.
The next step is to configure service checks. Depending on the service type we need to set a path or start/stop scripts etc. and assign tests we have defined before. You can assign the same tests to different service checks.
At the Alert Settings tab you can configure to whom sent alerts to on which events and to whom not.
Furthermore you can format the mail text. E.g. Subject: $SERVICE failed on $HOST at $DATE
Status
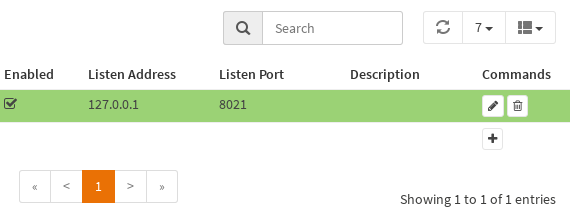
After starting Moint you can view detailed status information on the Services->Monit->Status page.
Examples
FTP Proxy
Check FTP proxy and restart it. If it doesn't run after 5 restarts don't check it again.
Tests
Name: RestartLimit5
Condition: 5 restarts within 5 cycles
Action: Unmonitor
Name: FTPProxy8021
Condition: failed host 127.0.0.1 port 8021 type tcp
Action: Restart
Service
Name: FTPProxy8021
Type: Process
PID File: /var/run/osftpproxy.127_0_0_1_8021.pid
Start: /usr/local/sbin/configctl ftpproxy start 127_0_0_1_8021
Stop: /usr/local/sbin/configctl ftpproxy start 127_0_0_1_8021
Tests: FTPProxy8021, RestartLimit5
HPE ProLiant DL380 G7 via IPMI
Check HPE ProLiant DL380 G7 hardware via IPMI.
Install ipmitool, load the ipmi kernel driver and create a check script.
create a script /usr/local/bin/CheckIPMI.sh
Make it executable.
Tests
Name: ExecStatus
Condition: status notequal 0
Action: Alert
Service
Name: IPMI
Type: Custom
Path: /usr/local/bin/CheckIPMI.sh
Tests: ExecStatus
It runs on the firewall host and sends messages or executes actions on various events.
With the os-monit plugin you can configure the Monit daemon.
Installation
To use Monit install the os-monit plugin first. It installs the monit package as a dependency.
After the installation has finished reload the GUI and navigate to Services->Monit->Settings.
Configuration
The first step is to check if the plugin installer has imported your System->Notification settings correctly. Then have a look at the other tabs. To help you get acquainted the installer has added some standard entries.
The order to configure a monitoring is to create Service Tests first, then Services to check and in the end Alerts.
Let's start with the Service Test Settings. A test contains a condition and an action. It can be assigned to one or more services. The Monit documentation shows possible tests. You can simply adopt it by omitting the IF and THEN statements.
The next step is to configure service checks. Depending on the service type we need to set a path or start/stop scripts etc. and assign tests we have defined before. You can assign the same tests to different service checks.
At the Alert Settings tab you can configure to whom sent alerts to on which events and to whom not.
Furthermore you can format the mail text. E.g. Subject: $SERVICE failed on $HOST at $DATE
NOTE: For cluster setups you can synchronize the configuration to the other node if you check Monit System Monitoring
under System->High Availabilty->Settings. Then go to Firewall->Diagnostics->Filter Reload and click on Force Config Sync.
Status
After starting Moint you can view detailed status information on the Services->Monit->Status page.
System 'firewall.example.com'
status Running
monitoring status Monitored
monitoring mode active
on reboot start
load average [0.59] [0.41] [0.35]
cpu 0.2%us 0.9%sy
memory usage 2.6 GB [8.1%]
swap usage 0 B [0.0%]
uptime 20d 4h 25m
boot time Thu, 18 May 2017 13:27:11
data collected Wed, 07 Jun 2017 17:51:23
Filesystem 'RootFs'
status Does not exist
monitoring status Monitored
monitoring mode active
on reboot start
data collected Wed, 07 Jun 2017 17:51:23
Program 'IPMI'
status Status ok
monitoring status Monitored
monitoring mode active
on reboot start
last exit value 0
last output System Health: OK, Power Meter: 174 Watts, Ambient Temp: 19 degrees C, Fans: 39 percent
data collected Wed, 07 Jun 2017 17:51:23
Examples
FTP Proxy
Check FTP proxy and restart it. If it doesn't run after 5 restarts don't check it again.
Tests
Name: RestartLimit5
Condition: 5 restarts within 5 cycles
Action: Unmonitor
Name: FTPProxy8021
Condition: failed host 127.0.0.1 port 8021 type tcp
Action: Restart
Service
Name: FTPProxy8021
Type: Process
PID File: /var/run/osftpproxy.127_0_0_1_8021.pid
Start: /usr/local/sbin/configctl ftpproxy start 127_0_0_1_8021
Stop: /usr/local/sbin/configctl ftpproxy start 127_0_0_1_8021
Tests: FTPProxy8021, RestartLimit5
HPE ProLiant DL380 G7 via IPMI
Check HPE ProLiant DL380 G7 hardware via IPMI.
Install ipmitool, load the ipmi kernel driver and create a check script.
Code Select
pkg install ipmitool
kldload ipmi
echo 'ipmi_load="YES"' >>/boot/loader.conf.localcreate a script /usr/local/bin/CheckIPMI.sh
Code Select
#!/bin/csh
set Status = 0
set FanCount = 0
set FanSum = 0
foreach Line (`/usr/local/bin/ipmitool sdr list | sed 's/ /\\t/g'`)
set SensorData = `echo $Line | sed 's/\\t/ /g'`
set SensorName = `echo $SensorData | awk -F\| '{print $1}'`
set SensorValue = `echo $SensorData | awk -F\| '{print $2}'`
set SensorStatus = `echo $SensorData | awk -F\| '{print $3}'`
if ( "$SensorStatus" != "ok" && "$SensorValue" != "disabled" ) then
echo "$SensorData"
set Status = 1
endif
if ( "$SensorName" =~ "Power Supply*" ) then
if ( "$SensorValue" == "0 Watts" ) then
echo "$SensorData"
set Status = 1
endif
endif
if ( "$SensorName" == "Power Meter" ) set PowerMeter = "$SensorValue"
if ( "$SensorName" == "Temp 1" ) set AmbientTemp = "$SensorValue"
if ( "$SensorName" =~ "Fan *" ) then
@ FanCount = ( $FanCount + 1 )
set FanValue = `echo $SensorValue | awk '{print $1}' | awk -F. '{print $1}'`
@ FanSum = ( $FanSum + $FanValue )
endif
end
if ( $Status == 0 ) then
@ FanSpeed = ( $FanSum / $FanCount )
echo "System Health: OK, Power Meter: $PowerMeter, Ambient Temp: $AmbientTemp, Fans: $FanSpeed percent"
endif
exit $Status
Make it executable.
Code Select
chmod +x /usr/local/bin/CheckIPMI.shTests
Name: ExecStatus
Condition: status notequal 0
Action: Alert
Service
Name: IPMI
Type: Custom
Path: /usr/local/bin/CheckIPMI.sh
Tests: ExecStatus

 "
"