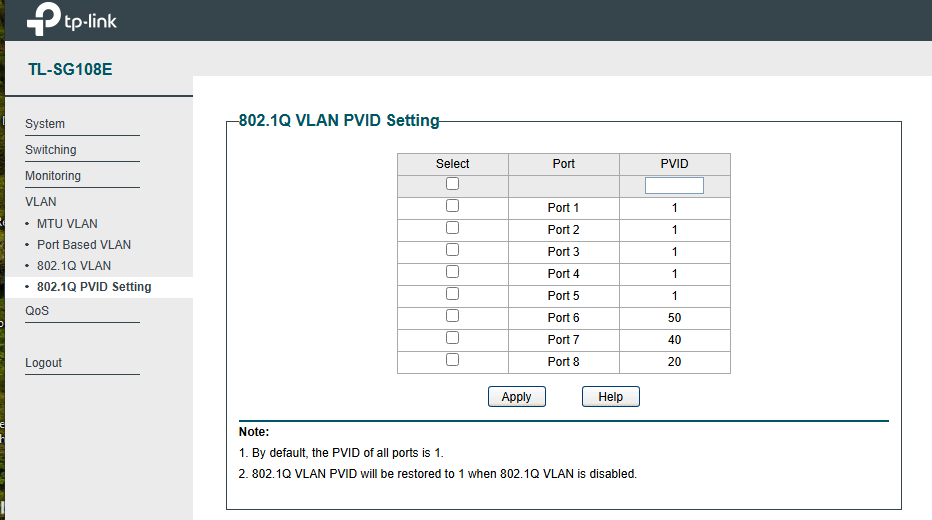
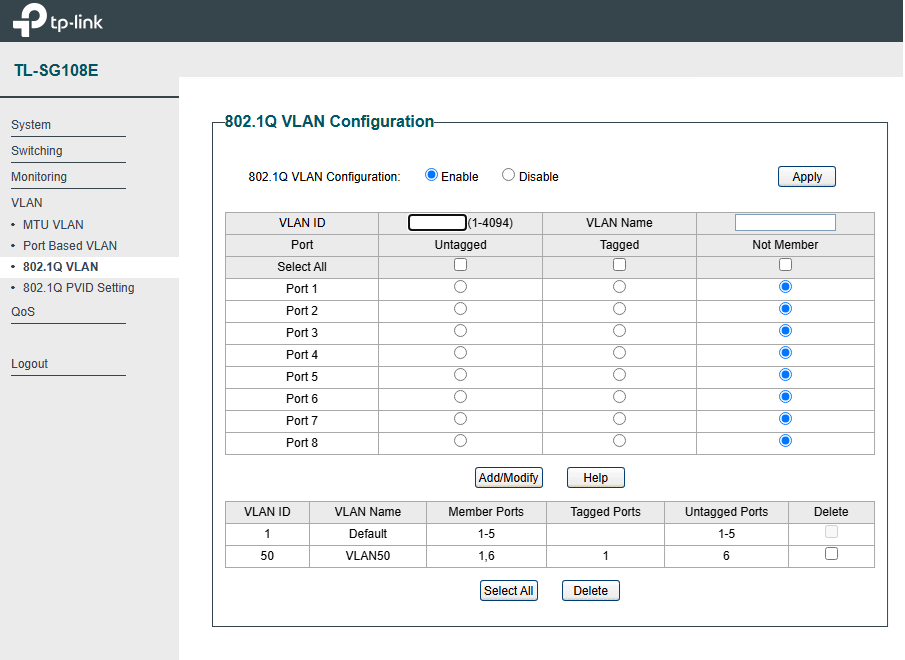
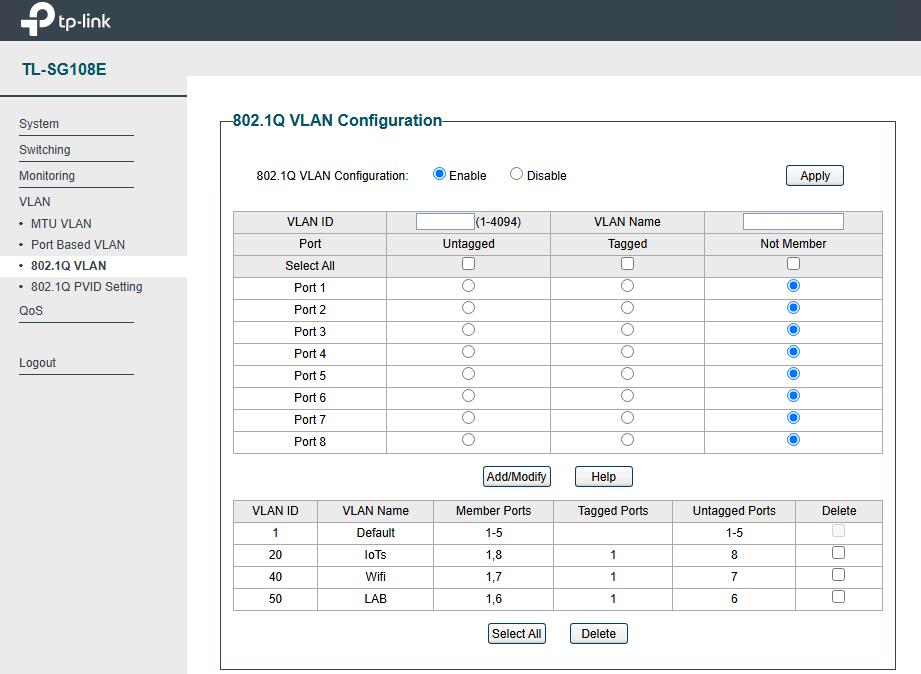
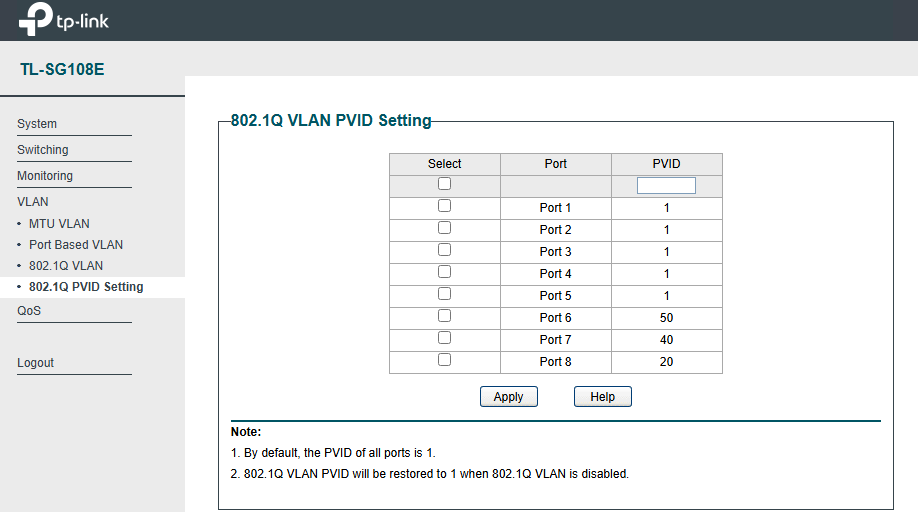
I removed the IP address from the second bridge vmbr1, and it fixed the issue. It seems like the firewall was blocking on-and-off traffic from VLAN 192.168.50.1/24 to 192.168.1./24. When I SSH from VM1 (192.168.50.222) to Proxmox (192.168.1.100) or any VM on the subnet 192.168.1.0/24, it blocks traffic, but not permanently. After a few minutes, it unblocks and then blocks again, causing the issue to be on and off. I don't know the explanation; I guess something has to do with routing, but because of you guys, now I know I don't have to include the IP address in the second bridge.
I have a little knowledge of networking and am planning to prepare for the Network+ certification sometime soon. Is there any OPNsense tutorial or YouTube video that I can learn more about it? I prefer video since I am a visual learner.
Thank you so much for helping. I must say this is one of the best forums that I have ever used. Keep doing the great work. Thanks
I have a little knowledge of networking and am planning to prepare for the Network+ certification sometime soon. Is there any OPNsense tutorial or YouTube video that I can learn more about it? I prefer video since I am a visual learner.
Thank you so much for helping. I must say this is one of the best forums that I have ever used. Keep doing the great work. Thanks

 "
"