It was a long time ago, just in case you are still looking for an answer, it worked for me. The only difference is that I don't have that "octoprint" in the path to reach my server.
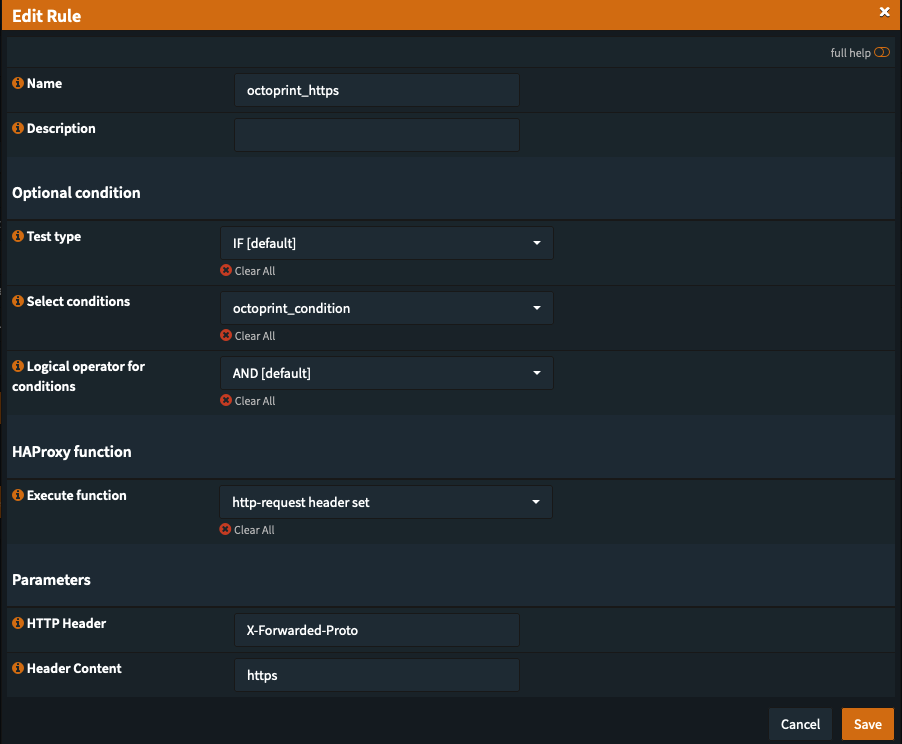
The only "line" from your config I implemented was this.
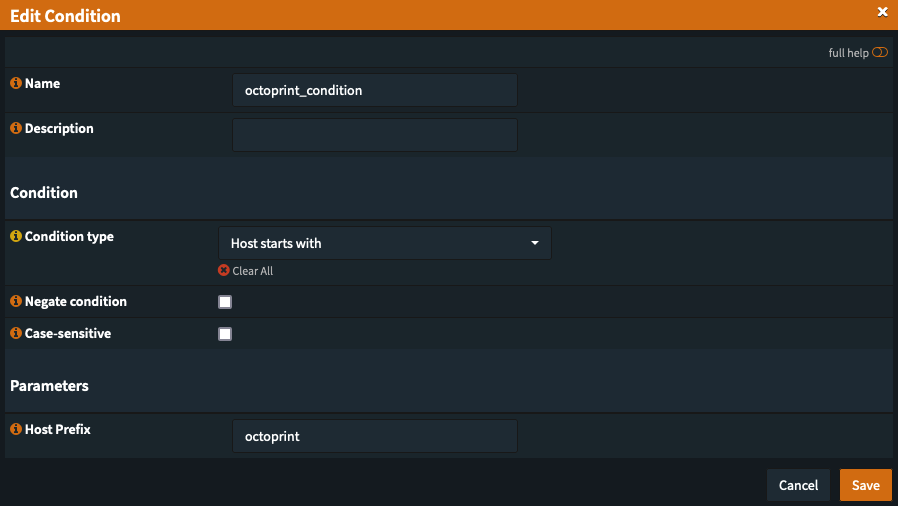
And I did it in the form of a "rule".
The condition is just a host prefix check.
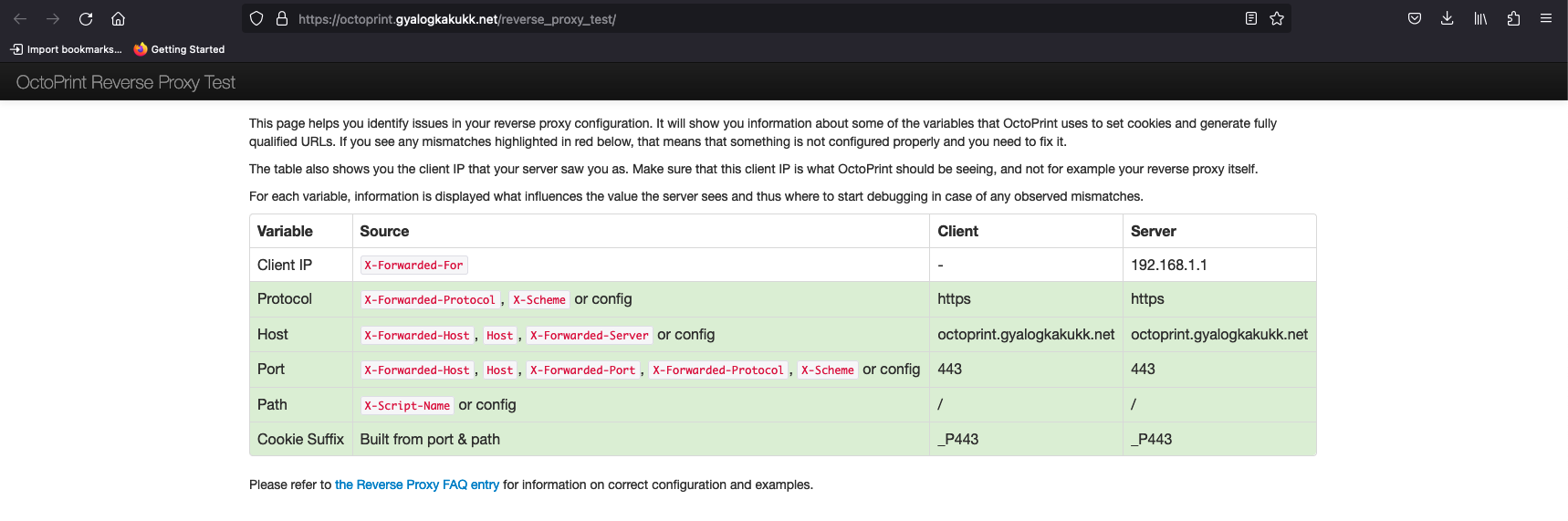
And now the OctoPrint reverse proxy check passes.
The only "line" from your config I implemented was this.
Code Select
http-request set-header X-Forwarded-Proto https if { ssl_fc }And I did it in the form of a "rule".

The condition is just a host prefix check.

And now the OctoPrint reverse proxy check passes.


 "
"
