Thanks for the link. Google can't help when you are missing the right keywords.
This section allows you to view all posts made by this member. Note that you can only see posts made in areas you currently have access to.
#1
Virtual private networks / Re: Tunnel ports from public server through OPNsense to host
September 15, 2021, 11:57:49 AM #2
Virtual private networks / Re: Tunnel ports from public server through OPNsense to host
September 15, 2021, 11:28:44 AM
To be honest I was hoping to get direction to a step by step guide of somebody who's facing same issue. I am not the first one facing this issue.
Like...
1. Install WireGuard / Open VPN
2. Setup WireGuiard / Open VPN like this...
3. Install counterpart on public server
4. Configure counterpart server
5. Establish the tunnel
6. Forward port XYZ like this...
Like...
1. Install WireGuard / Open VPN
2. Setup WireGuiard / Open VPN like this...
3. Install counterpart on public server
4. Configure counterpart server
5. Establish the tunnel
6. Forward port XYZ like this...
#3
Virtual private networks / Re: Tunnel ports from public server through OPNsense to host
September 15, 2021, 10:31:56 AM
So e.g. use OpenVPN (or better Wireguard?) to connect from OPNsense to IONOS server running CentOS?
Can I forward port from IONOS server through the tunnel or do I need to get these somehow from OPNsense?
Can I forward port from IONOS server through the tunnel or do I need to get these somehow from OPNsense?
#4
Virtual private networks / Re: Tunnel ports from public server through OPNsense to host
September 15, 2021, 10:20:57 AM
I have DS-Lite so the IPv4 I am receiving from my ISP is not usable and I won't switch everything to IPv4. Therefore I require an alternative entry point such as a public server with its IPv4 address.
#5
Virtual private networks / Tunnel ports from public server through OPNsense to host
September 15, 2021, 09:59:26 AM
Hello,
Since I changed my ISP, I no longer have direct access to my home network because of IPv6. To solve this problem, I got myself an IONOS VPS-S server with IPv4 address, which I would like to connect to OPNsense and forward needed ports like HTTP to my systems.
I have to admit that I am an absolute beginner when it comes to OPNsense, so please bear with me. The IONOS server with its IPv4 address is in place and the OPNsense firewall is prepared and available on my network. Can someone briefly explain to me the steps needed to set up a tunnel between the two and forward, for example, port 80 from the IONOS server to OPNsense? I have read about autossh from OPNsense to IONOS server, but also wireguard and openvpn.... What is the best and "easiest" way?
Since I changed my ISP, I no longer have direct access to my home network because of IPv6. To solve this problem, I got myself an IONOS VPS-S server with IPv4 address, which I would like to connect to OPNsense and forward needed ports like HTTP to my systems.
I have to admit that I am an absolute beginner when it comes to OPNsense, so please bear with me. The IONOS server with its IPv4 address is in place and the OPNsense firewall is prepared and available on my network. Can someone briefly explain to me the steps needed to set up a tunnel between the two and forward, for example, port 80 from the IONOS server to OPNsense? I have read about autossh from OPNsense to IONOS server, but also wireguard and openvpn.... What is the best and "easiest" way?
#6
General Discussion / Re: Port-Forward on WAN with private IP
March 02, 2021, 10:01:19 PM
I re-created it a couple of times already and thanks to refleciton setting, I find the rule in "FW > Rules > WAN".
#7
General Discussion / Re: Port-Forward on WAN with private IP
March 02, 2021, 09:19:40 PM
8080 is not showing up at all and I already attemped to open 192.168.19.67:8080 to trigger such message.
Just the WAN IF IP is showing up:
@3 block drop in log inet from 192.168.19.67 to any
[ Evaluations: 319832 Packets: 0 Bytes: 0 States: 0 ]
[ Inserted: uid 0 pid 36645 State Creations: 0 ]
--------------------------------
But 8080 appears on Firewall: Diagnostics: pfInfo -> NAT tab
@0 no nat proto carp all
[ Evaluations: 2210 Packets: 0 Bytes: 0 States: 0 ]
[ Inserted: uid 0 pid 36645 State Creations: 0 ]
@1 nat on hn1 inet proto tcp from (hn1:network:1) to <SVRWEB2:1> port = http -> (hn1) port 1024:65535 round-robin
[ Evaluations: 2210 Packets: 0 Bytes: 0 States: 0 ]
[ Inserted: uid 0 pid 36645 State Creations: 0 ]
@2 nat on lo0 inet proto tcp from (lo0:network:1) to <SVRWEB2:1> port = http -> (lo0) port 1024:65535 round-robin
[ Evaluations: 19 Packets: 0 Bytes: 0 States: 0 ]
[ Inserted: uid 0 pid 36645 State Creations: 0 ]
@3 nat on hn0 inet proto tcp from (hn0:network:1) to <SVRWEB2:1> port = http -> (hn0) port 1024:65535 round-robin
[ Evaluations: 3 Packets: 0 Bytes: 0 States: 0 ]
[ Inserted: uid 0 pid 36645 State Creations: 0 ]
@4 nat on hn0 inet proto tcp from (hn0:network:1) to <SVRWEB2:1> port = http -> (hn0) port 1024:65535 round-robin
[ Evaluations: 0 Packets: 0 Bytes: 0 States: 0 ]
[ Inserted: uid 0 pid 36645 State Creations: 0 ]
@5 nat on hn1 inet proto tcp from (hn1:network:1) to <SVRWEB2:1> port = http -> (hn1) port 1024:65535 round-robin
[ Evaluations: 3 Packets: 0 Bytes: 0 States: 0 ]
[ Inserted: uid 0 pid 36645 State Creations: 0 ]
@6 nat on lo0 inet proto tcp from (lo0:network:1) to <SVRWEB2:1> port = http -> (lo0) port 1024:65535 round-robin
[ Evaluations: 3 Packets: 0 Bytes: 0 States: 0 ]
[ Inserted: uid 0 pid 36645 State Creations: 0 ]
@0 no rdr proto carp all
[ Evaluations: 413640 Packets: 0 Bytes: 0 States: 0 ]
[ Inserted: uid 0 pid 36645 State Creations: 0 ]
@1 no rdr on hn1 proto tcp from any to (hn1:2) port = http
[ Evaluations: 413633 Packets: 0 Bytes: 0 States: 0 ]
[ Inserted: uid 0 pid 36645 State Creations: 0 ]
@2 no rdr on hn1 proto tcp from any to (hn1:2) port = https
[ Evaluations: 14 Packets: 0 Bytes: 0 States: 0 ]
[ Inserted: uid 0 pid 36645 State Creations: 0 ]
@3 rdr log on hn1 inet proto tcp from any to (hn1:1) port = 8080 -> <SVRWEB2> port 80 round-robin
[ Evaluations: 0 Packets: 0 Bytes: 0 States: 0 ]
Just the WAN IF IP is showing up:
@3 block drop in log inet from 192.168.19.67 to any
[ Evaluations: 319832 Packets: 0 Bytes: 0 States: 0 ]
[ Inserted: uid 0 pid 36645 State Creations: 0 ]
--------------------------------
But 8080 appears on Firewall: Diagnostics: pfInfo -> NAT tab
@0 no nat proto carp all
[ Evaluations: 2210 Packets: 0 Bytes: 0 States: 0 ]
[ Inserted: uid 0 pid 36645 State Creations: 0 ]
@1 nat on hn1 inet proto tcp from (hn1:network:1) to <SVRWEB2:1> port = http -> (hn1) port 1024:65535 round-robin
[ Evaluations: 2210 Packets: 0 Bytes: 0 States: 0 ]
[ Inserted: uid 0 pid 36645 State Creations: 0 ]
@2 nat on lo0 inet proto tcp from (lo0:network:1) to <SVRWEB2:1> port = http -> (lo0) port 1024:65535 round-robin
[ Evaluations: 19 Packets: 0 Bytes: 0 States: 0 ]
[ Inserted: uid 0 pid 36645 State Creations: 0 ]
@3 nat on hn0 inet proto tcp from (hn0:network:1) to <SVRWEB2:1> port = http -> (hn0) port 1024:65535 round-robin
[ Evaluations: 3 Packets: 0 Bytes: 0 States: 0 ]
[ Inserted: uid 0 pid 36645 State Creations: 0 ]
@4 nat on hn0 inet proto tcp from (hn0:network:1) to <SVRWEB2:1> port = http -> (hn0) port 1024:65535 round-robin
[ Evaluations: 0 Packets: 0 Bytes: 0 States: 0 ]
[ Inserted: uid 0 pid 36645 State Creations: 0 ]
@5 nat on hn1 inet proto tcp from (hn1:network:1) to <SVRWEB2:1> port = http -> (hn1) port 1024:65535 round-robin
[ Evaluations: 3 Packets: 0 Bytes: 0 States: 0 ]
[ Inserted: uid 0 pid 36645 State Creations: 0 ]
@6 nat on lo0 inet proto tcp from (lo0:network:1) to <SVRWEB2:1> port = http -> (lo0) port 1024:65535 round-robin
[ Evaluations: 3 Packets: 0 Bytes: 0 States: 0 ]
[ Inserted: uid 0 pid 36645 State Creations: 0 ]
@0 no rdr proto carp all
[ Evaluations: 413640 Packets: 0 Bytes: 0 States: 0 ]
[ Inserted: uid 0 pid 36645 State Creations: 0 ]
@1 no rdr on hn1 proto tcp from any to (hn1:2) port = http
[ Evaluations: 413633 Packets: 0 Bytes: 0 States: 0 ]
[ Inserted: uid 0 pid 36645 State Creations: 0 ]
@2 no rdr on hn1 proto tcp from any to (hn1:2) port = https
[ Evaluations: 14 Packets: 0 Bytes: 0 States: 0 ]
[ Inserted: uid 0 pid 36645 State Creations: 0 ]
@3 rdr log on hn1 inet proto tcp from any to (hn1:1) port = 8080 -> <SVRWEB2> port 80 round-robin
[ Evaluations: 0 Packets: 0 Bytes: 0 States: 0 ]
#8
General Discussion / Re: Port-Forward on WAN with private IP
March 02, 2021, 04:03:19 PM
Not sure if that string will help?!
@0 scrub on lo0 all fragment reassemble
[ Evaluations: 1051590 Packets: 64 Bytes: 0 States: 0 ]
[ Inserted: uid 0 pid 36645 State Creations: 0 ]
@1 scrub on hn1 all fragment reassemble
[ Evaluations: 1051517 Packets: 545136 Bytes: 19245212 States: 0 ]
[ Inserted: uid 0 pid 36645 State Creations: 0 ]
@2 scrub on hn0 all fragment reassemble
[ Evaluations: 506377 Packets: 506334 Bytes: 0 States: 0 ]
[ Inserted: uid 0 pid 36645 State Creations: 0 ]
@0 block drop in log on ! hn1 inet from 192.168.20.0/24 to any
[ Evaluations: 381920 Packets: 0 Bytes: 0 States: 0 ]
[ Inserted: uid 0 pid 36645 State Creations: 0 ]
@1 block drop in log inet from 192.168.20.68 to any
[ Evaluations: 335661 Packets: 0 Bytes: 0 States: 0 ]
[ Inserted: uid 0 pid 36645 State Creations: 0 ]
@2 block drop in log on ! hn0 inet from 192.168.19.0/24 to any
[ Evaluations: 294085 Packets: 0 Bytes: 0 States: 0 ]
[ Inserted: uid 0 pid 36645 State Creations: 0 ]
@3 block drop in log inet from 192.168.19.67 to any
[ Evaluations: 294088 Packets: 0 Bytes: 0 States: 0 ]
[ Inserted: uid 0 pid 36645 State Creations: 0 ]
@0 scrub on lo0 all fragment reassemble
[ Evaluations: 1051590 Packets: 64 Bytes: 0 States: 0 ]
[ Inserted: uid 0 pid 36645 State Creations: 0 ]
@1 scrub on hn1 all fragment reassemble
[ Evaluations: 1051517 Packets: 545136 Bytes: 19245212 States: 0 ]
[ Inserted: uid 0 pid 36645 State Creations: 0 ]
@2 scrub on hn0 all fragment reassemble
[ Evaluations: 506377 Packets: 506334 Bytes: 0 States: 0 ]
[ Inserted: uid 0 pid 36645 State Creations: 0 ]
@0 block drop in log on ! hn1 inet from 192.168.20.0/24 to any
[ Evaluations: 381920 Packets: 0 Bytes: 0 States: 0 ]
[ Inserted: uid 0 pid 36645 State Creations: 0 ]
@1 block drop in log inet from 192.168.20.68 to any
[ Evaluations: 335661 Packets: 0 Bytes: 0 States: 0 ]
[ Inserted: uid 0 pid 36645 State Creations: 0 ]
@2 block drop in log on ! hn0 inet from 192.168.19.0/24 to any
[ Evaluations: 294085 Packets: 0 Bytes: 0 States: 0 ]
[ Inserted: uid 0 pid 36645 State Creations: 0 ]
@3 block drop in log inet from 192.168.19.67 to any
[ Evaluations: 294088 Packets: 0 Bytes: 0 States: 0 ]
[ Inserted: uid 0 pid 36645 State Creations: 0 ]
#9
General Discussion / Re: Port-Forward on WAN with private IP
March 01, 2021, 09:26:00 PM
This is for testing and getting familiar with opnsense. I would like the WAN interface accept requests from a private IP. Technicially speaking this must be feasible.
#10
General Discussion / Re: Port-Forward on WAN with private IP
February 28, 2021, 11:05:17 PM
Sure :-)

#11
General Discussion / Re: Port-Forward on WAN with private IP
February 28, 2021, 01:31:37 AM
Tried already w/o success :-\
#12
General Discussion / Re: Port-Forward on WAN with private IP
February 28, 2021, 12:57:26 AM
I am testing from a host in WAN subnet using a private
IP subnet, different from LAN subnet.
IP subnet, different from LAN subnet.
#13
General Discussion / Port-Forward on WAN with private IP
February 27, 2021, 10:59:08 PM
Dear community,
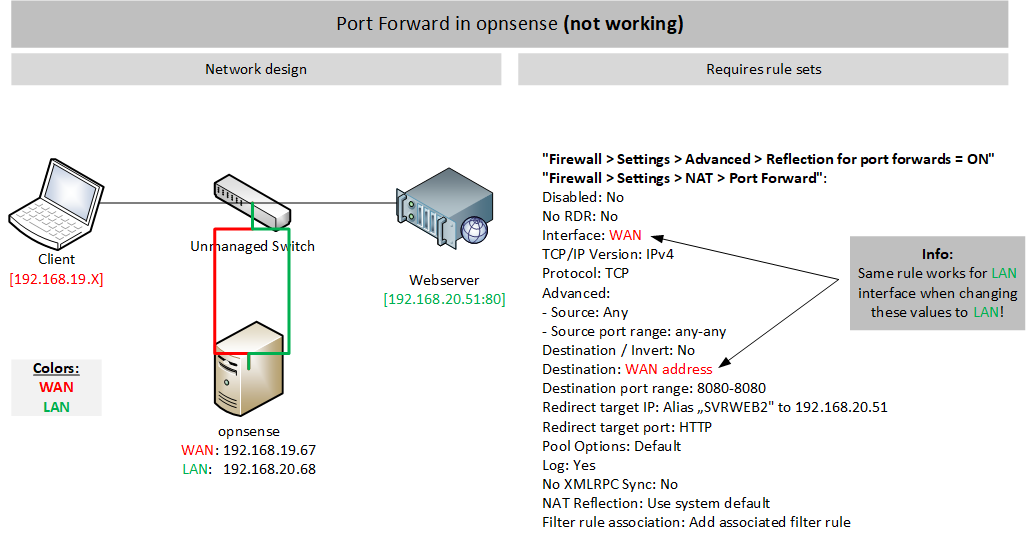
I've been trying getting Port-Foward to work from WAN to LAN using a private IP for WAN interface. Yes, a private IP address for testing!
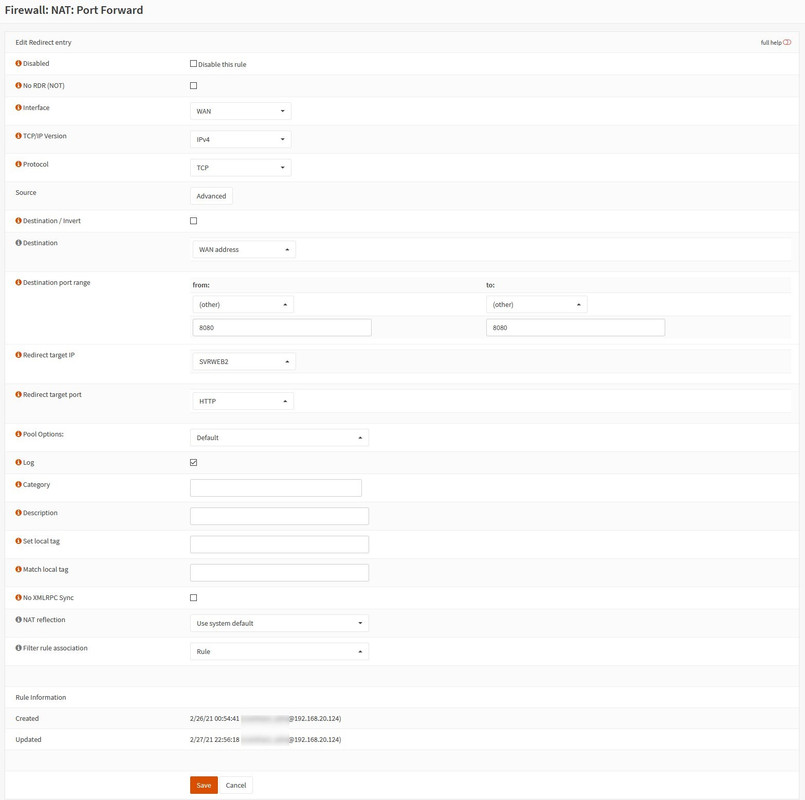
I created a Port Forward rule which seem to be okay. It works when selecting the LAN interface as source interface and destination but it does not work out on WAN interface.
WAN: 192.168.19.67
LAN: 192.168.20.68
What is the special thing about the WAN interface?
I've been trying getting Port-Foward to work from WAN to LAN using a private IP for WAN interface. Yes, a private IP address for testing!
I created a Port Forward rule which seem to be okay. It works when selecting the LAN interface as source interface and destination but it does not work out on WAN interface.
WAN: 192.168.19.67
LAN: 192.168.20.68
- WAN interface does NOT block private networks
- WAN interfaces does NOT block bogon networks
- Reflection for port forwards is ON
What is the special thing about the WAN interface?

#14
German - Deutsch / Re: Port-Forward funktioniert nicht
February 27, 2021, 10:37:38 PM
Wenn es bei Deiner Telefonanlage über das WAN Interface funktioniert, machst Du irgend etwas anders als ich... oder das WAN Interface hat bei Dir eine Public IP, die vielleicht anders gehandhabt wird als meine private IP.
Ich weiß ja nun, dass es nicht an der Regel hakt, sondern am Interface. Denn wenn ich alles auf LAN stelle, funktioniert es... macht aber natürlich keinen Sinn. Also back to the roots... Was mache ich falsch? :-(
Ich weiß ja nun, dass es nicht an der Regel hakt, sondern am Interface. Denn wenn ich alles auf LAN stelle, funktioniert es... macht aber natürlich keinen Sinn. Also back to the roots... Was mache ich falsch? :-(
#15
German - Deutsch / Re: Port-Forward funktioniert nicht
February 26, 2021, 01:59:43 PM
Habe einige Fortschritte gemacht... Ich habe meine NAT-Regel geändert, die nun auf das Interface statt auf die WAN hört... Mit dem LAN Interface funktioniert die Umleitung einwandfrei. Wobei, was ist mit der WAN-Schnittstelle falsch?
Die WAN-Schnittstelle ist nicht so konfiguriert, dass sie private / gefälschte Netzwerke blockiert.
Die WAN-Schnittstelle ist nicht so konfiguriert, dass sie private / gefälschte Netzwerke blockiert.

 "
"
