I am working on setting up a Wireguard server on a small VPS that my OPNsense box on my LAN will connect to so that my reverse proxy and email servers can be accessed without port forwarding and exposing my home IP.
I have the tunnel up and running and I can see the connection from both ends, I can ping the wg opnsense peer from the VPS just fine. I thought I had all the correct rules setup but something is clearly missing as I cannot ping any addresses on my LAN from the VPS.
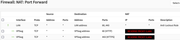
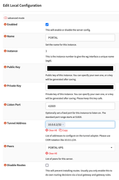
To clarify, I don't want the Wireguard tunnel to have unfettered access to my entire LAN, my goal is for it to be treated as if it were basically a WAN interface. eg. I want to be able to forward only the ports I need, and allow access to only the LAN IP's that need to be accessed. Later on I plan to setup IPS and I would want it running on this interface. This tunnel is only for services exposed to the internet. I already have a separate vpn solution to access my entire LAN remotely if I need to.
Below is all the info on how I set it all up. Since I couldn't find a single guide on doing this specifically with OPNsense I used multiple guides and did my best to fill in the gaps.

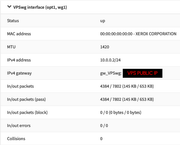



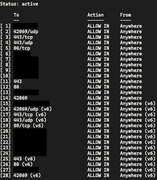
I have the tunnel up and running and I can see the connection from both ends, I can ping the wg opnsense peer from the VPS just fine. I thought I had all the correct rules setup but something is clearly missing as I cannot ping any addresses on my LAN from the VPS.
To clarify, I don't want the Wireguard tunnel to have unfettered access to my entire LAN, my goal is for it to be treated as if it were basically a WAN interface. eg. I want to be able to forward only the ports I need, and allow access to only the LAN IP's that need to be accessed. Later on I plan to setup IPS and I would want it running on this interface. This tunnel is only for services exposed to the internet. I already have a separate vpn solution to access my entire LAN remotely if I need to.
Below is all the info on how I set it all up. Since I couldn't find a single guide on doing this specifically with OPNsense I used multiple guides and did my best to fill in the gaps.
- https://www.youtube.com/watch?v=GXsvIXozECU
- https://docs.opnsense.org/manual/how-tos/wireguard-client.html
- https://github.com/mochman/Bypass_CGNAT/wiki/Digital-Ocean-(Manual-Installation)/










 "
"
