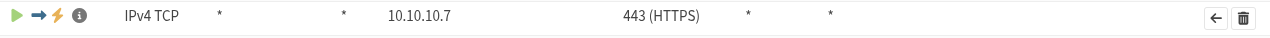
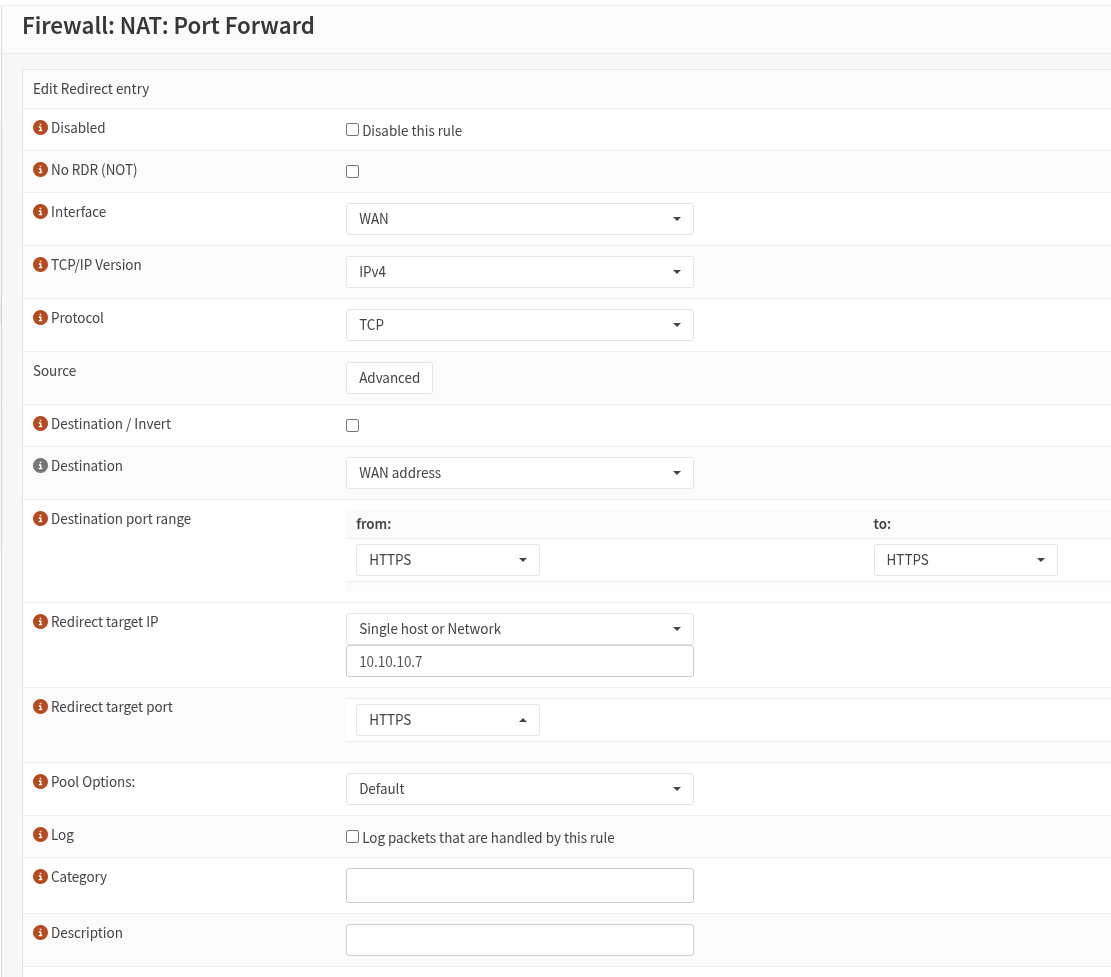
Well, not only was I feeling like an idiot, but it turns out that I was one... My configuration was working just fine, but what wasn't working was the IPv4 path via my work VPN, which I was using to test the home config from an external source. I did some curl/netcat tests from another external source and lo and behold, everything worked as intended.
Thanks for bearing with me in this Patrick and the reminder to just use good ol'
Thanks for bearing with me in this Patrick and the reminder to just use good ol'
Code Select
pfctl to dump the raw pf config. That ended up being a helpful validator, at least for me, that what was configured was actually correct.

 "
"