Hi, thanks for your reply! I really appreciate your help.
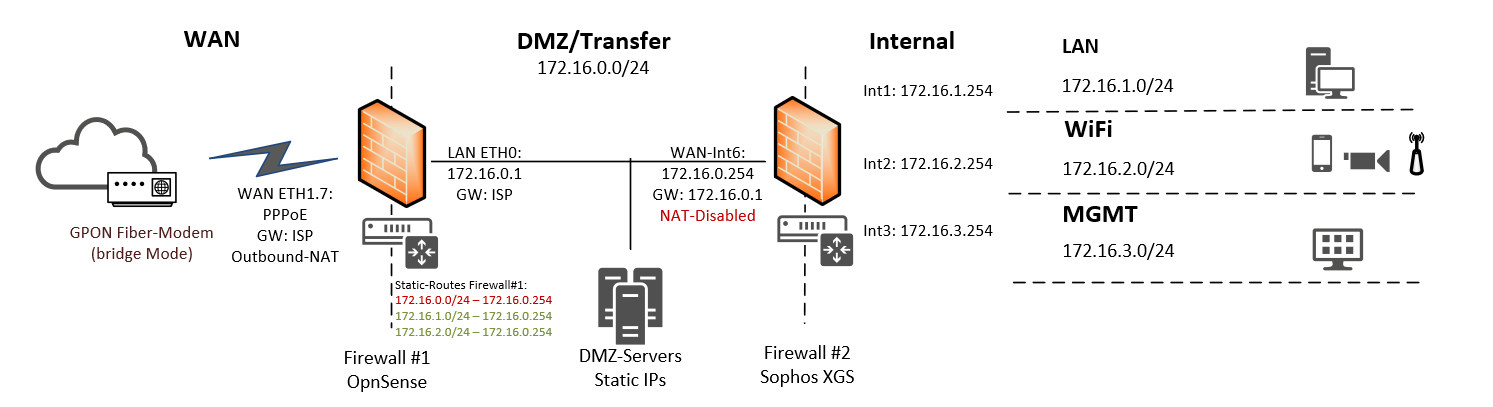
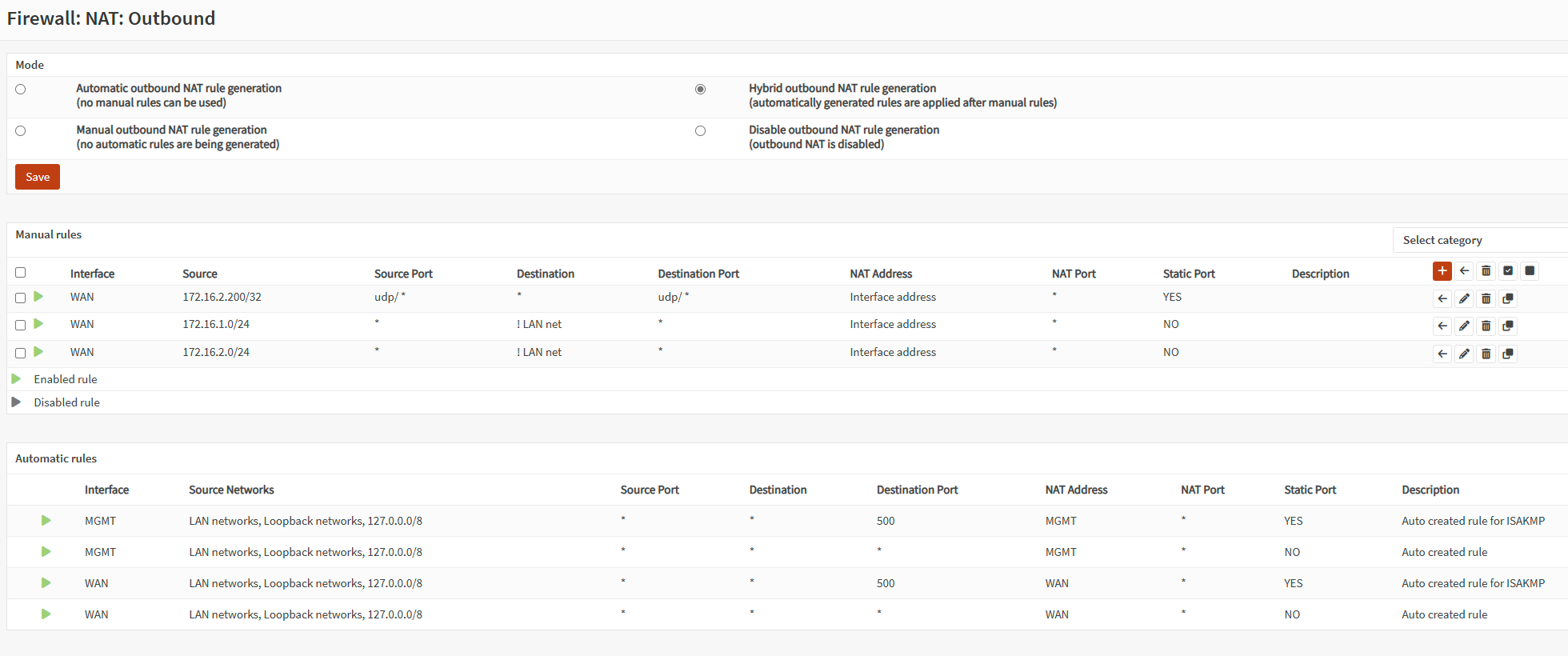
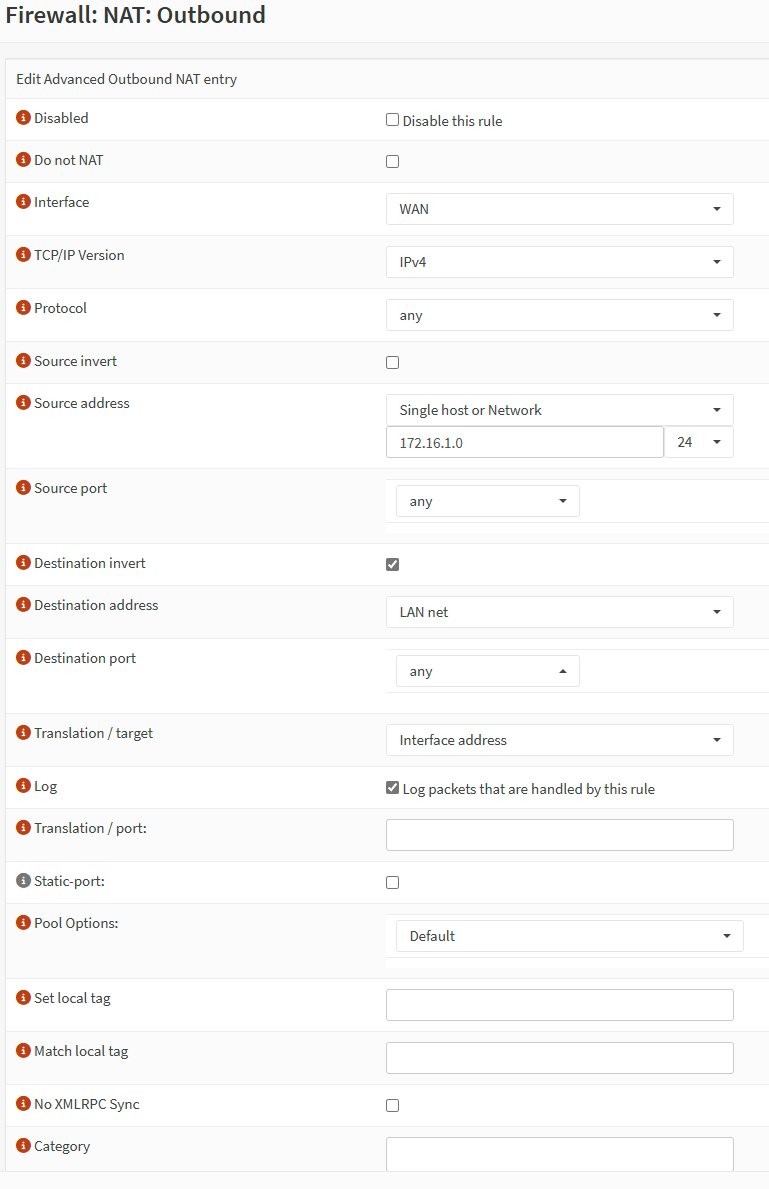
I have made screenshots for the Outbound NAT Config and a NAT Rule in detail:
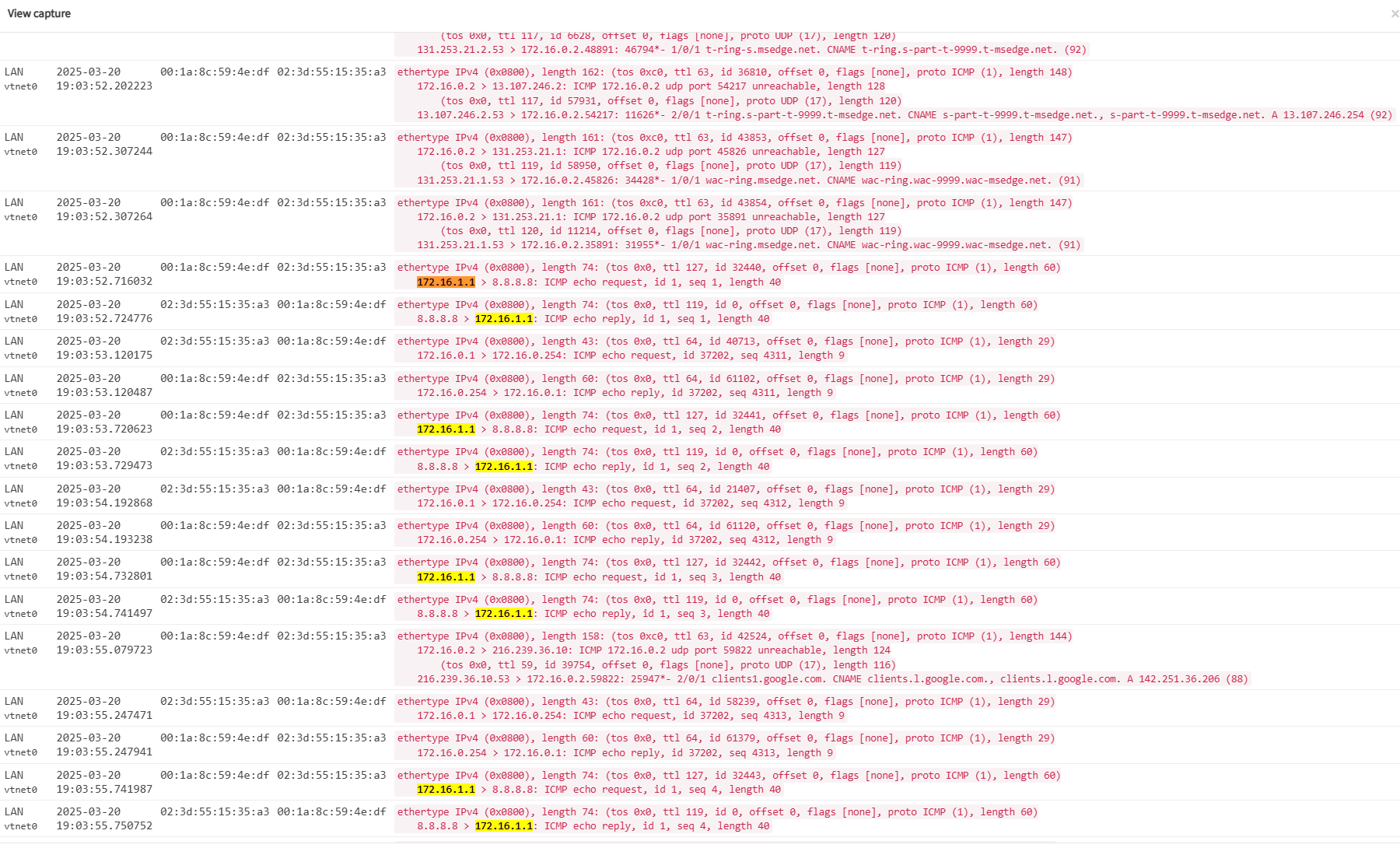
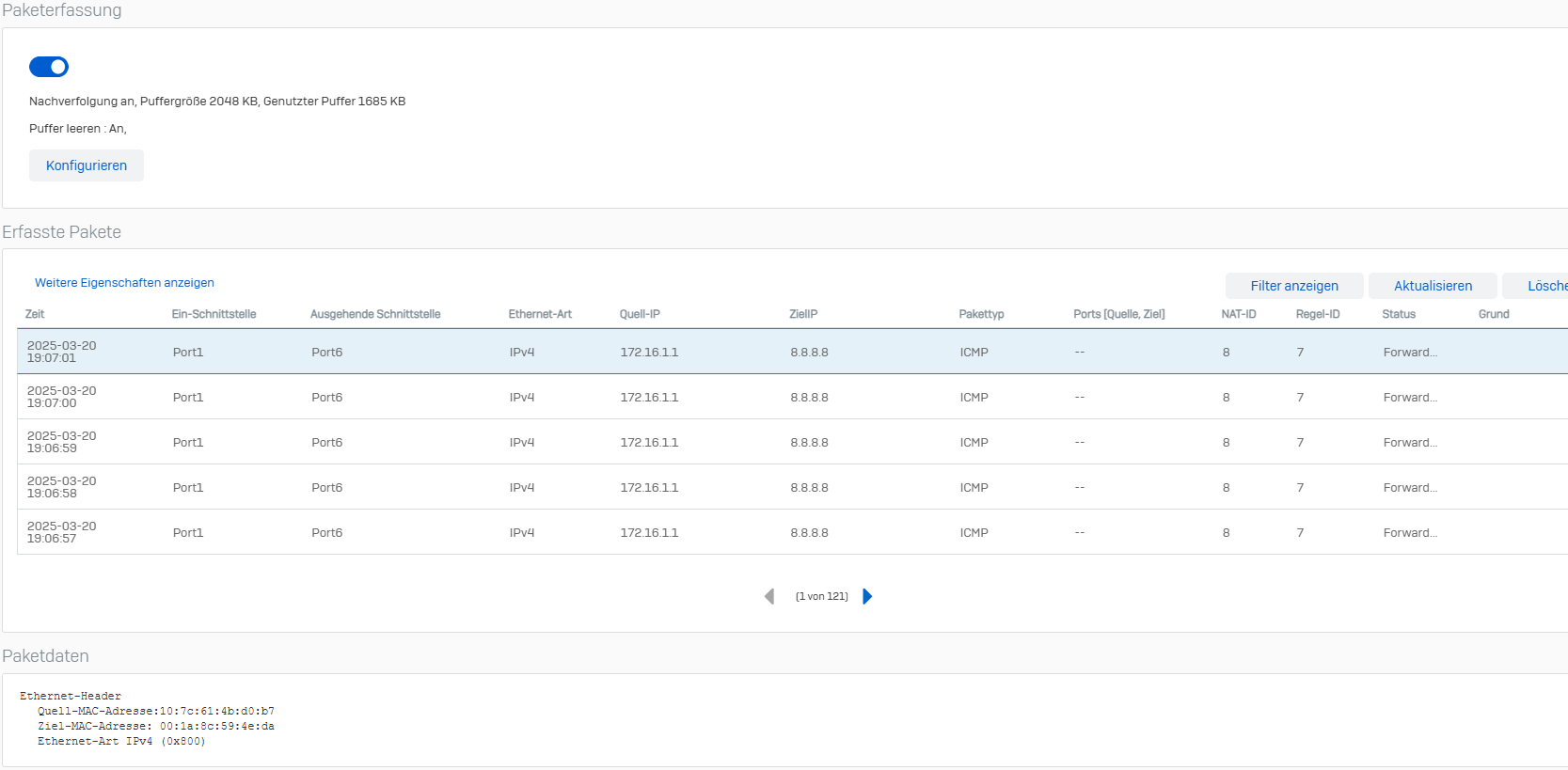
Then I've started a ping from my workstation 172.16.1.1 to 8.8.8.8 and filtered ICMP for the packet captures. Please find the results enclosed.
Packet Capture from FW#1 LAN:
Packet Capture FW#2 WAN:
Firewall Live Log:
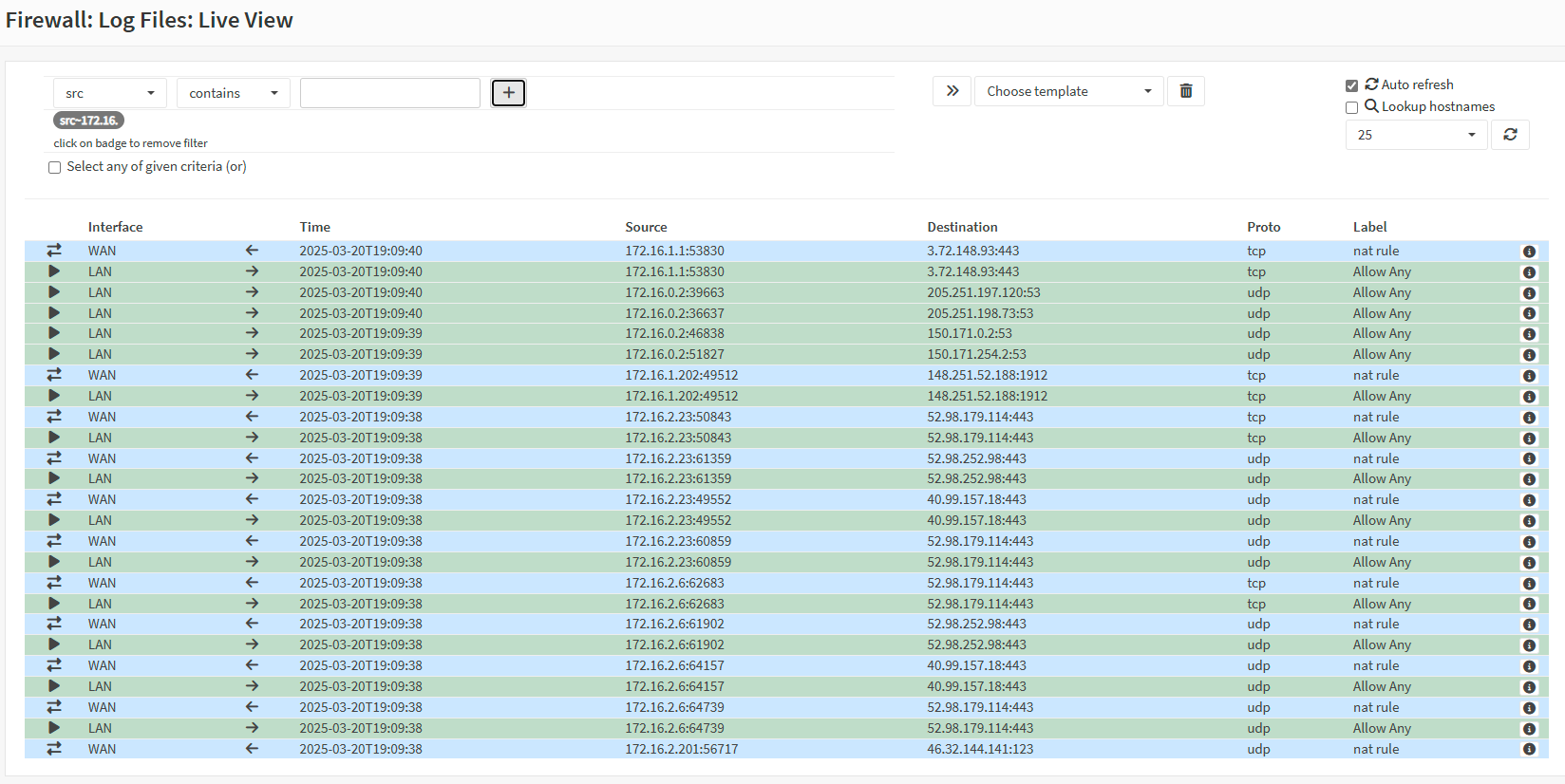
You can see that the traffic arrives without NAT/MASQ from Firewall #2 through the DMZ to Firewall #1.
I have made screenshots for the Outbound NAT Config and a NAT Rule in detail:


Then I've started a ping from my workstation 172.16.1.1 to 8.8.8.8 and filtered ICMP for the packet captures. Please find the results enclosed.
Packet Capture from FW#1 LAN:

Packet Capture FW#2 WAN:

Firewall Live Log:

You can see that the traffic arrives without NAT/MASQ from Firewall #2 through the DMZ to Firewall #1.

 "
"