It appears to be fixed in version 25.7.9.
This section allows you to view all posts made by this member. Note that you can only see posts made in areas you currently have access to.
#2
25.7, 25.10 Series / Re: 25.7.8 Unbond DNS block domains
November 30, 2025, 01:47:06 PM
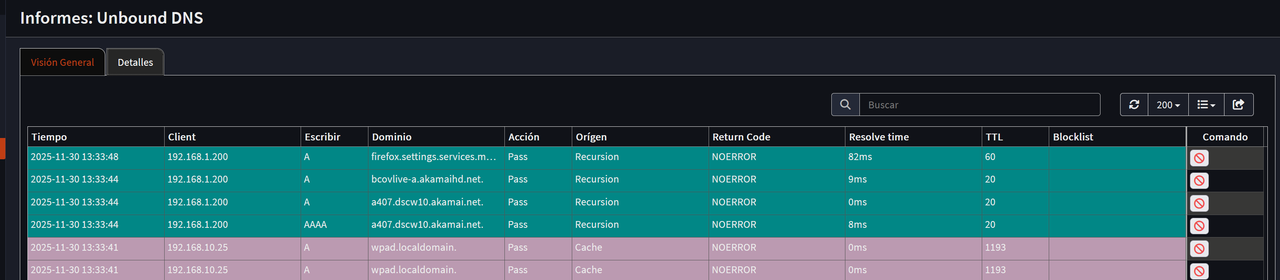
When I block domains in this Unbond DNS report details section or in the previous overview section, both blocked and unblocked domains are no longer saved. Therefore, if there is a domain you blocked a long time ago and later want to unblock, it cannot be found.
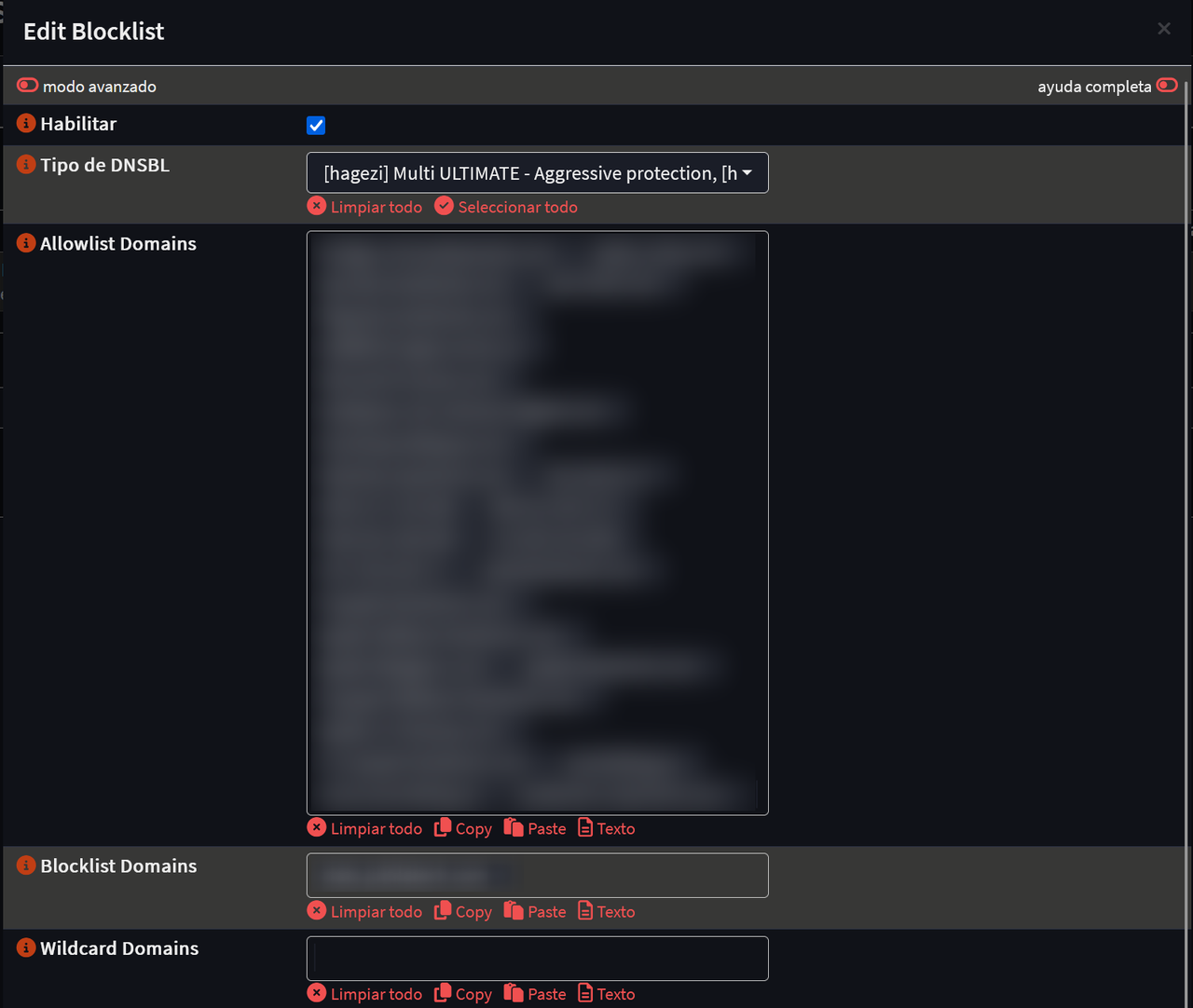


#3
25.7, 25.10 Series / 25.7.8 Unbond DNS block domains
November 28, 2025, 03:31:28 PM
Hello, good afternoon. I've updated to the latest version of OPNSense with the changes to Unbond DNS. I've created two new domain block lists and added the previously unblocked domains to the allowed domain list.
The problem is that when I check the Unbond DNS reports for domain blocks, after unblocking domains using the pencil icon, I can't find where they're registered and I can't block them again because they don't appear in the allowed list.
The problem is that when I check the Unbond DNS reports for domain blocks, after unblocking domains using the pencil icon, I can't find where they're registered and I can't block them again because they don't appear in the allowed list.
#4
General Discussion / Re: CrowdSec
August 29, 2025, 11:55:34 AM
Hello, good morning.
I've had CrowdSec installed for a few weeks now, and I understand that just installing it provides the basic configuration and protection to function properly. Are there any additional settings to improve its performance or security? Thank you very much for the development.
I've had CrowdSec installed for a few weeks now, and I understand that just installing it provides the basic configuration and protection to function properly. Are there any additional settings to improve its performance or security? Thank you very much for the development.
#5
General Discussion / Re: Isolate clients from a network
August 27, 2025, 06:15:54 PMQuote from: patient0 on August 27, 2025, 12:58:02 PMAs mentioned, you can consolitate the first and last rule into the one I wrote (a pass rule with destination everything-except-the-alias-network), but you don't have to. And the DNS would come before your block-the-aliases.I've tested the rules you wrote for me, disabled my rule, and the order is now as follows: Access DNS > Client Isolation > Internet Access
With these three rules, all computers have Internet access, but they also have access to other LANs, and can also communicate with each other via remote desktop (for example).
I'm sure I didn't do the rule correctly. Do you see everything as correct?
#6
General Discussion / Re: Isolate clients from a network
August 27, 2025, 12:06:16 PM #7
General Discussion / Re: Isolate clients from a network
August 27, 2025, 11:47:18 AM
Hello, good morning. Is this DNS access rule you've set up for me to be added after the rule I included in my first post?
This rule is already created, but I named it "alias" because the original name of the alias that blocks access to the three networks is: "Bloqueig_de_MQL5_a_LANs", which is written in Catalan.
Quote from: patient0 on August 26, 2025, 11:21:19 PM# Allow clients to access router for DNS queries
Action: pass
Interface: MQL
Direction: in
Protocol: udp, port 53
Source: MQL net
Destination: MQL address
This rule is already created, but I named it "alias" because the original name of the alias that blocks access to the three networks is: "Bloqueig_de_MQL5_a_LANs", which is written in Catalan.
Quote from: patient0 on August 26, 2025, 11:21:19 PM# Allow access to everything except 192.168.1.0/24 - 192.168.2.0/24 - 192.168.18.0/24 from the MQL network:
Action: pass
Interface: MQL
Direction: in
Protocol: any
Source: MQL net
Destination: ! (not) "aliases"
#8
General Discussion / Re: Isolate clients from a network
August 26, 2025, 10:14:48 AMQuote from: BrandyWine on August 25, 2025, 07:25:04 PMThere's also a "trick" where you use .1q between FW and a large # port switch, where each host is in it's own vlan ID (one switch port per ID), thus the only way two hosts can talk to each other would be to ride .1q to FW and then back to switch, but you would apply FW rules accordingly. Not 100% this would work with OPNsense.I don't think I quite understand what you're referring to, because my knowledge of the vastness of OPNsense is pretty basic. My needs aren't very demanding, so I only have basic security settings, like Unbond DNS Blocklist and CrowdSec (CrowdSec doesn't require any further configuration with the basic installation, right?). Thanks!
Quote from: patient0 on August 25, 2025, 09:35:41 PMWhat about the other questions of mine? As I wrote, your clients won't be able to resolve any DNS request if the DNS is set to a MQL network IP.Yes, OPNsense itself resolves DNS requests. I previously had external DNS servers, but reading posts here on the forum, I found the most private and secure way was the default OPNsense configuration. Thank you for your answers!
https://forum.opnsense.org/index.php?topic=39119.msg191611#msg191611
#9
General Discussion / Re: Isolate clients from a network
August 25, 2025, 07:16:39 PMQuote from: patient0 on August 25, 2025, 05:05:55 PMCan you post the full ruleset for MQL net?This rule prevents access to 192.168.1.0/24 - 192.168.2.0/24 - 192.168.18.0/24 from the MQL network:
Action: Block
Interface: MQL
Direction: in
Protocol: any
Source: MQL net
Destination: "aliases"
And this other rule grants Internet access:
Action: pass
Interface: MQL
Direction: in
Protocol: any
Source: MQL net
Destination: any
I only have these two rules. The others are the ones OPNsense uses by default, plus the ones CrowdSec created, but those are all hidden in the drop-down menu.
#10
General Discussion / Isolate clients from a network
August 25, 2025, 01:59:30 PM
Hello, good morning.
I currently have three physically segmented networks: Wi-Fi, LAN, and MQL. All devices within the LAN and Wi-Fi have access to MQL, and I've created a rule for the MQL network to not have access to other networks.
But when I try to create a rule to prevent devices within MQL from communicating with each other within the same network, the devices are unable to access web pages, but they can ping DNS servers and services.
This is the rule, and I have it before the Internet outbound rule. What procedure am I doing wrong?
Action: Block
Interface: MQL
Direction: in
Source: MQL net
Destination: MQL net
I currently have three physically segmented networks: Wi-Fi, LAN, and MQL. All devices within the LAN and Wi-Fi have access to MQL, and I've created a rule for the MQL network to not have access to other networks.
But when I try to create a rule to prevent devices within MQL from communicating with each other within the same network, the devices are unable to access web pages, but they can ping DNS servers and services.
This is the rule, and I have it before the Internet outbound rule. What procedure am I doing wrong?
Action: Block
Interface: MQL
Direction: in
Source: MQL net
Destination: MQL net
#11
General Discussion / Re: Open ports on network interfaces
June 22, 2025, 06:55:33 PMQuote from: cookiemonster on June 22, 2025, 06:50:04 PMUnderstood. But how does the cable (there must be one) from the street connect to the "router + ont Huawei" ?Yes, a fiber optic cable runs from the street to the Huawei router+ont Huawei (it is an all-in-one device), and then I have to run a 15 cm cable from the Huawei router to the OPNsense device.
#12
General Discussion / Re: Open ports on network interfaces
June 22, 2025, 06:46:16 PMQuote from: cookiemonster on June 22, 2025, 06:33:10 PMThat clear now.My ISP provides the fiber optic cable from the street to the router + ont Huawei, then I have to connect from a RJ45 port Huawei to OPNsense.
OPN then on the DMZ is one way of doing things. I think fritboxes force this setup too but I am not certain.
One thing to check however. If your ISP leaves an electrical terminating device on the wall and it is an Ethernet cable from it to the current Huawei, you could in theory plug it instead onto the WAN of your OPN device directly. No Huawei in the chain.
Electrically is the same. The difference is whether your ISP requires authenticating details to establish a connection and those are hard set on the Huawei.
If that is the case and you can get them and transfer them to OPN WAN settings, you're set.
#13
General Discussion / Re: Open ports on network interfaces
June 22, 2025, 01:40:21 PMQuote from: cookiemonster on June 22, 2025, 12:44:59 AMpesky ISP updates. I'm glad you got to the bottom of it.
Out of interest though. You say your ISP gives you a device running OPNSense as your ONT. Are you sure about that?
My ISP provided me with a very basic Huawei router which is an all in one, ONT + Router, and I had to activate the DMZ and then put another device for the OPNsense. Tomorrow I will contact my ISP to see if they can provide me with a dedicated ONT, or provide me with the communication data between OLT and ONT and buy a configurable ONT myself.
#14
General Discussion / Re: Open ports on network interfaces
June 21, 2025, 12:56:36 PM
@viragomann @cookiemonster
I was able to fix the problem. The problem was that the ISP router had a factory reset for some reason, and the DMZ had disappeared. Once activated, everything worked, although in opnsense the internal IP address provided by the ISP router still appears. I will have to look for a universal ONT to solve this "problem". Thank you very much for your patience with your troubleshooting ideas.
I was able to fix the problem. The problem was that the ISP router had a factory reset for some reason, and the DMZ had disappeared. Once activated, everything worked, although in opnsense the internal IP address provided by the ISP router still appears. I will have to look for a universal ONT to solve this "problem". Thank you very much for your patience with your troubleshooting ideas.
#15
General Discussion / Re: Open ports on network interfaces
June 19, 2025, 07:44:49 PMQuote from: viragomann on June 19, 2025, 07:28:33 PMYes, but your public IP is assigned to the ONT, while OPNsense behind it has a private IP as your screenshots show.The router/ONT It has a specific configuration to put it in bridge mode which is how it currently is, and all traffic is redirected to opnsense. It will be a year or so now that it has been running like this.
So your ONT is a router in fact.
This is an essential information.
So first of all you have to forward the traffic on the outer router (ONT) to OPNsense. Have you even done this?

 "
"

