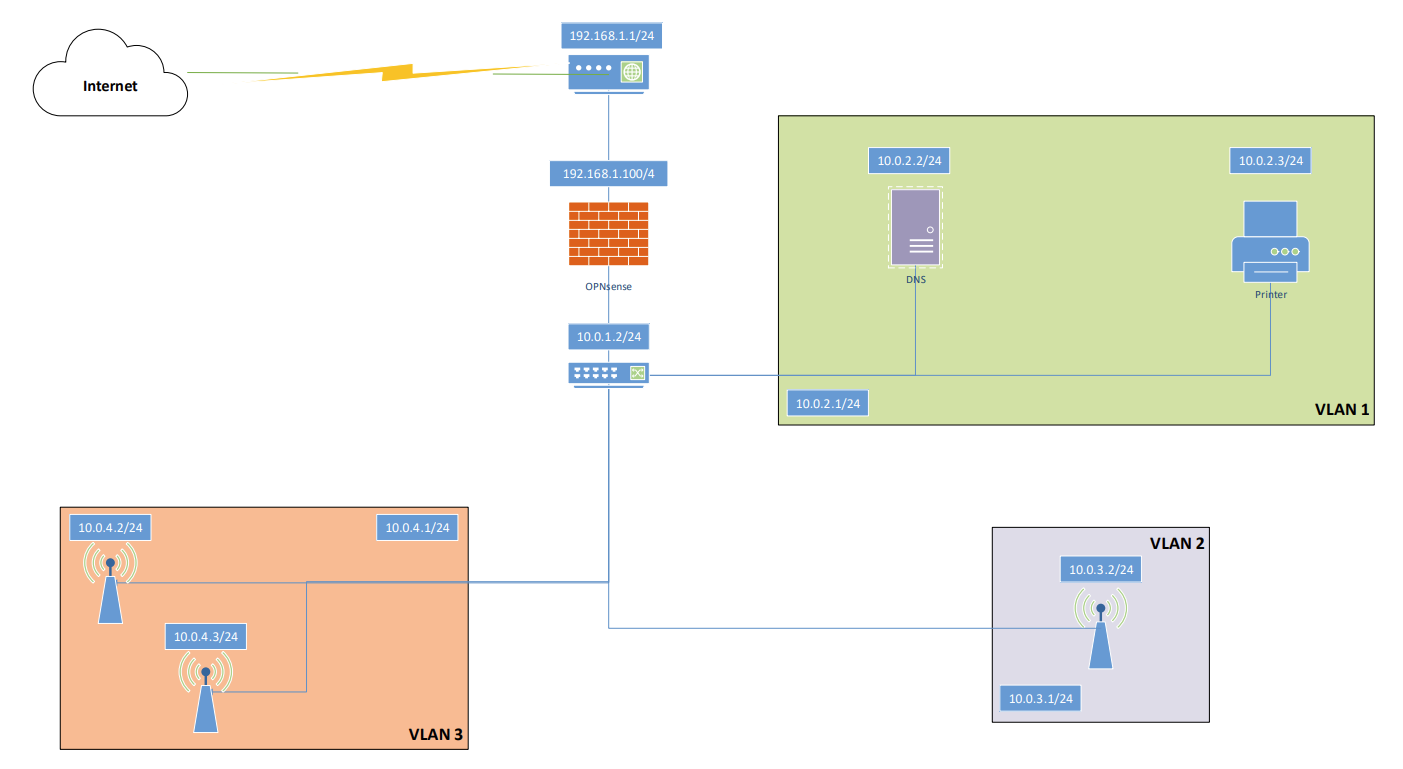
BIG UPDATE :
After adding new NAT rules the connection is working !
THANKS A LOT for you guidance Patrick M. Hausen, I learn a lot today !
And thank you too netnut for you help !
Best regards,
pandaBolide
After adding new NAT rules the connection is working !
THANKS A LOT for you guidance Patrick M. Hausen, I learn a lot today !
And thank you too netnut for you help !
Best regards,
pandaBolide

 "
"