Hi all,
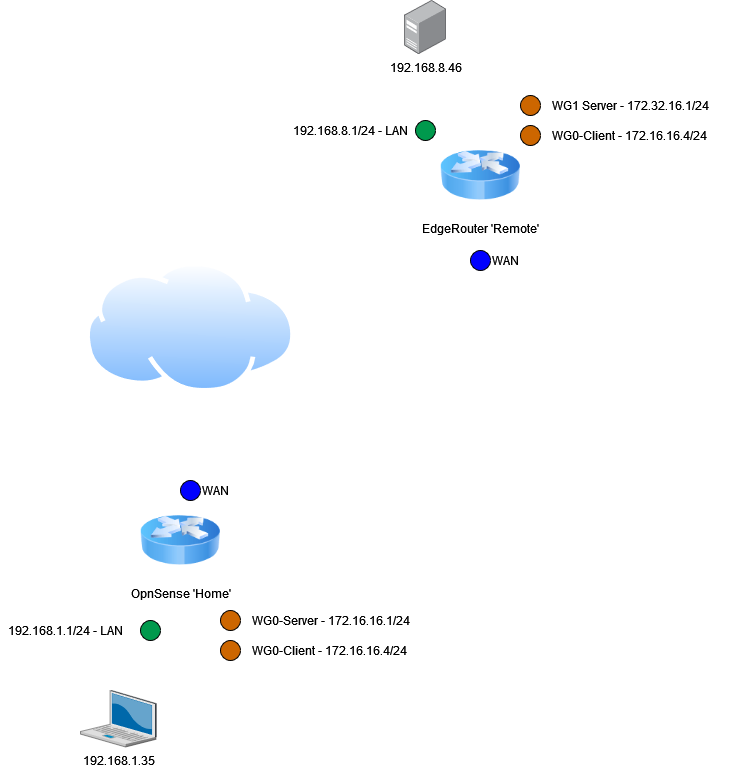
I have a setup with OpnSense at one location 'home' - it has a static WAN IP and runs a WireGuard server. I have a second location 'remote' on an EdgeRouter X. I have set that up with a WireGuard client config that connects to home. That site has firewall rules and routes configured to connect to resources at home from the LAN on remote.
I also setup a WireGuard server on the EdgeRouter for remote access / support if I needed - but that site is about to go behind CG NAT and I won't be able to connect to it anymore.
I am trying to workout what gateway and routes I need to setup on the OpnSense device to permit access from the 'Home' LAN to the resources in the 'Remote' LAN.
ie, load the web interface on 192.168.8.46
When I am on the OpnSense router I can ping the WG client IP 172.16.16.4 - but I can't ping it from any device on the LAN.
(IPs in the image are all made up, but reflect the environment, ie the LAN / WG subnets are all different.
Any advice?
Thanks
I have a setup with OpnSense at one location 'home' - it has a static WAN IP and runs a WireGuard server. I have a second location 'remote' on an EdgeRouter X. I have set that up with a WireGuard client config that connects to home. That site has firewall rules and routes configured to connect to resources at home from the LAN on remote.
I also setup a WireGuard server on the EdgeRouter for remote access / support if I needed - but that site is about to go behind CG NAT and I won't be able to connect to it anymore.
I am trying to workout what gateway and routes I need to setup on the OpnSense device to permit access from the 'Home' LAN to the resources in the 'Remote' LAN.
ie, load the web interface on 192.168.8.46
When I am on the OpnSense router I can ping the WG client IP 172.16.16.4 - but I can't ping it from any device on the LAN.
(IPs in the image are all made up, but reflect the environment, ie the LAN / WG subnets are all different.
Any advice?

Thanks

 "
"
