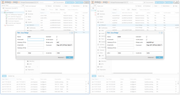
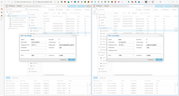
Quote from: meyergru on January 29, 2026, 09:54:46 AMWhat is the question?
If that MTU works for you, you could probably distribute it network-wide with DHCP option 26 and there is also an RA option to send it, but as I said, IDK if those work for most clients.
Hmm, I'm not sure if this is the right way to frame it, but I'm wondering what's the proper way to describe the issue.
cURL will still fail even if the NIC's MTU is set to the proper value, and the only way to get ping to connect reliably is by setting the ICMP packet size in every run of it.
It looks like the problem resides in how the MTU is being handled when going from the LAN interface to the WAN, as even a device being physically the same as the VM (testing from the Proxmox host, that is) will suffer from the same problems that every downstream device has regardless of medium (be it WiFi, Ethernet, a VPN, or a combination of all of them).
From where I'm standing, I'm using two identical installations of the same software and hardware on every part of the chain, yet the issues are only reflected on one of them. I'd like to consider this a reproducible problem that might be a bug, but as you've mentioned, my connection to the outside world through my ISP is hard to come by for better or for worse.
I'd like to find a way to both figure out how and why this problem is happening in the first place and help out debug it in the event the problem is something reproducible.
The first thing I'm imagining as a potential first step is running packet captures simultaneously at every point in the chain, though as I'm not certain what to look for, I'm wondering if doing so could make more noise instead of actually being useful.
TL;DR: I think the problem is more complex than just setting the proper MTU value, and I'd like to know how to properly present my case for a bug report to be able to look into it.

 "
"