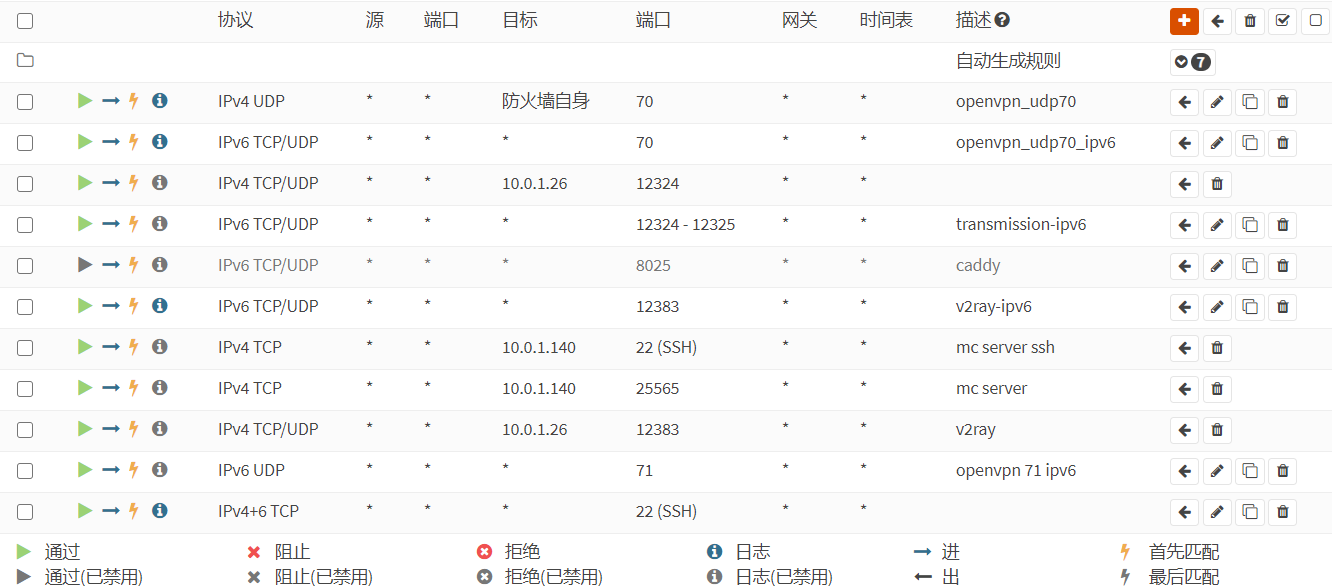
请各位注意,这种方法有个致命的问题,如果tun2socks不能在网络服务启动之前启动,那么网络服务启动时会找不到这个接口,导致接口重新分配,并且断网
所以没做好开机自启的,使用中千万不要重启
所以没做好开机自启的,使用中千万不要重启
This section allows you to view all posts made by this member. Note that you can only see posts made in areas you currently have access to.
Show posts Menu
#!/bin/sh
#
# $FreeBSD$
#
# PROVIDE: mosdns
# REQUIRE: LOGIN FILESYSTEMS
# KEYWORD: shutdown
. /etc/rc.subr
name="mosdns"
desc="mosdns daemon"
rcvar="mosdns_enable"
command="/usr/sbin/daemon"
pidfile="/var/run/${name}.pid"
procname="/usr/local/mosdns-freebsd-amd64/mosdns"
command_args="-f -p ${pidfile} -u root ${procname} -dir2exe -c config.yaml "
load_rc_config $name
run_rc_command "$1"
tun2socks -device tun://mytun2socks0 -loglevel info -proxy socks5://127.0.0.1:1081 -stats 0.0.0.0:9000 -udp-timeout 120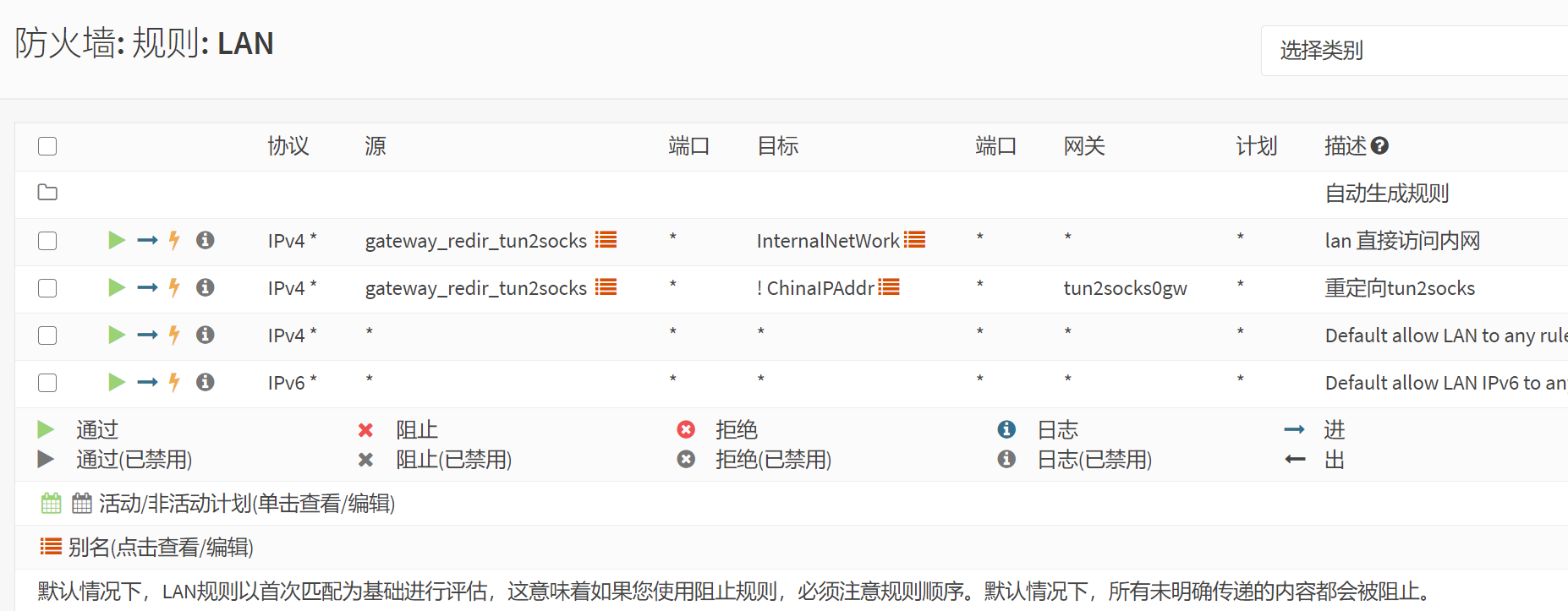
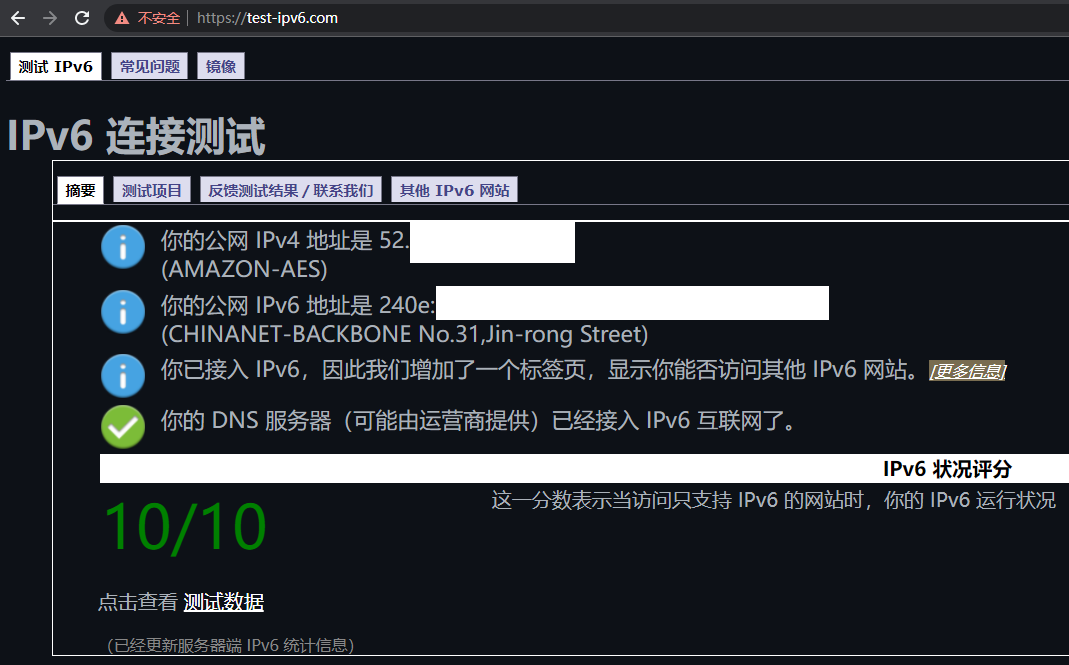

Internet6:
Destination Gateway Flags Netif Expire
default fe80::a19:a6ff:fe3f:53f2%pppoe0 UG pppoe0
::1 link#8 UH lo0
240e:xa0:xxxx:xxxx::/64 link#12 U pppoe0
240e:xa0:xxxx:xxxx:320e:d5ff:fe55:d762 link#12 UHS lo0
240e:ya1:yyyy:yyyy::/64 link#1 U igb0
240e:ya1:yyyy:yyyy:320e:d5ff:fe55:d762 link#1 UHS lo0
fe80::%igb0/64 link#1 U igb0
fe80::320e:d5ff:fe55:d762%igb0 link#1 UHS lo0
fe80::%em0/64 link#6 U em0
fe80::320e:d5ff:fe52:735%em0 link#6 UHS lo0
fe80::%lo0/64 link#8 U lo0
fe80::1%lo0 link#8 UHS lo0
fe80::320e:d5ff:fe55:d762%ovpns1 link#11 UHS lo0
fe80::%pppoe0/64 link#12 U pppoe0
fe80::320e:d5ff:fe55:d762%pppoe0 link#12 UHS lo0
pppoe0: flags=88d1<UP,POINTOPOINT,RUNNING,NOARP,SIMPLEX,MULTICAST> metric 0 mtu 1492
inet6 fe80::320e:d5ff:fe55:d762%pppoe0 prefixlen 64 scopeid 0xc
inet6 240e:xa0:xxxx:xxxx:320e:d5ff:fe55:d762 prefixlen 64 autoconf
inet 180.a.b.c --> 180.a.b.1 netmask 0xffffffff
nd6 options=23<PERFORMNUD,ACCEPT_RTADV,AUTO_LINKLOCAL>
igb0: flags=8843<UP,BROADCAST,RUNNING,SIMPLEX,MULTICAST> metric 0 mtu 1500
options=802028<VLAN_MTU,JUMBO_MTU,WOL_MAGIC>
ether 30:0e:d5:55:d7:62
inet6 fe80::320e:d5ff:fe55:d762%igb0 prefixlen 64 scopeid 0x1
inet6 240e:xa1:yyyy:yyyy:320e:d5ff:fe55:d762 prefixlen 64
inet 10.0.1.1 netmask 0xffffff00 broadcast 10.0.1.255
media: Ethernet autoselect (1000baseT <full-duplex>)
status: active
nd6 options=21<PERFORMNUD,AUTO_LINKLOCAL>
2021-08-30T16:15:33 openvpn[63412] 240e:zzz:zzzz:zzzz:8dae:664f:4e7:609f TLS: Initial packet from [AF_INET6]240e:zzz:zzzz:zzzz:8dae:664f:4e7:609f:62142 (via 240e:xa0:xxxx:yyyy:320e:d5ff:fe55:d762%pppoe0), sid=33962ebb a7001040
2021-08-30T16:15:33 openvpn[63412] 240e:zzz:zzzz:zzzz:8dae:664f:4e7:609f Incoming Control Channel Authentication: Using 160 bit message hash 'SHA1' for HMAC authentication
2021-08-30T16:15:33 openvpn[63412] 240e:zzz:zzzz:zzzz:8dae:664f:4e7:609f Outgoing Control Channel Authentication: Using 160 bit message hash 'SHA1' for HMAC authentication
2021-08-30T16:15:27 openvpn[63412] 240e:zzz:zzzz:zzzz:8dae:664f:4e7:609f SIGUSR1[soft,tls-error] received, client-instance restarting
2021-08-30T16:15:27 openvpn[63412] 240e:zzz:zzzz:zzzz:8dae:664f:4e7:609f TLS Error: TLS handshake failed
2021-08-30T16:15:27 openvpn[63412] 240e:zzz:zzzz:zzzz:8dae:664f:4e7:609f TLS Error: TLS key negotiation failed to occur within 60 seconds (check your network connectivity)