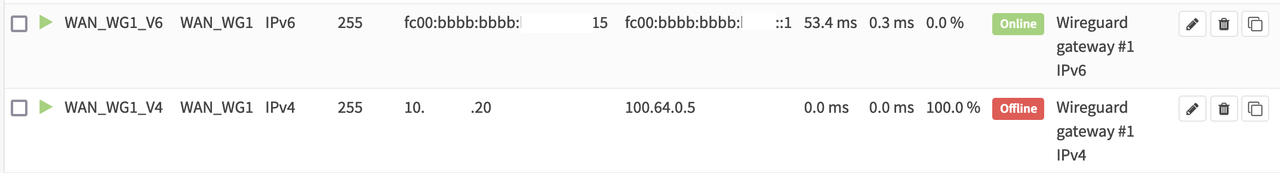
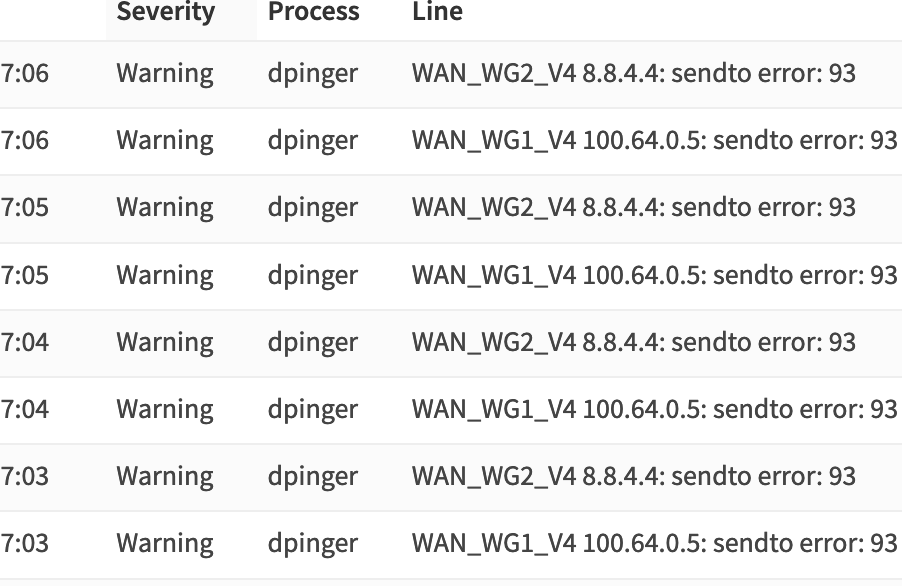
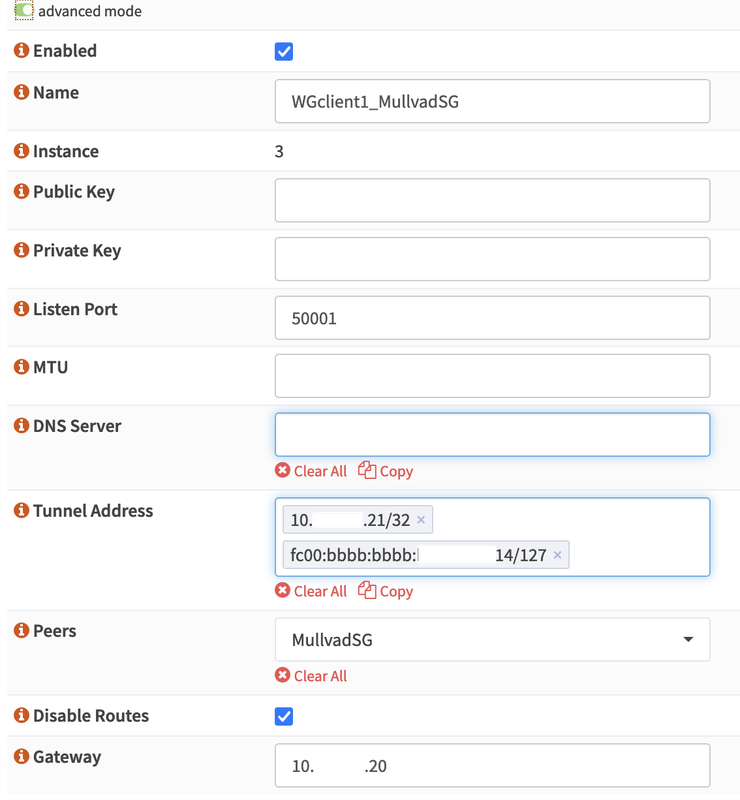
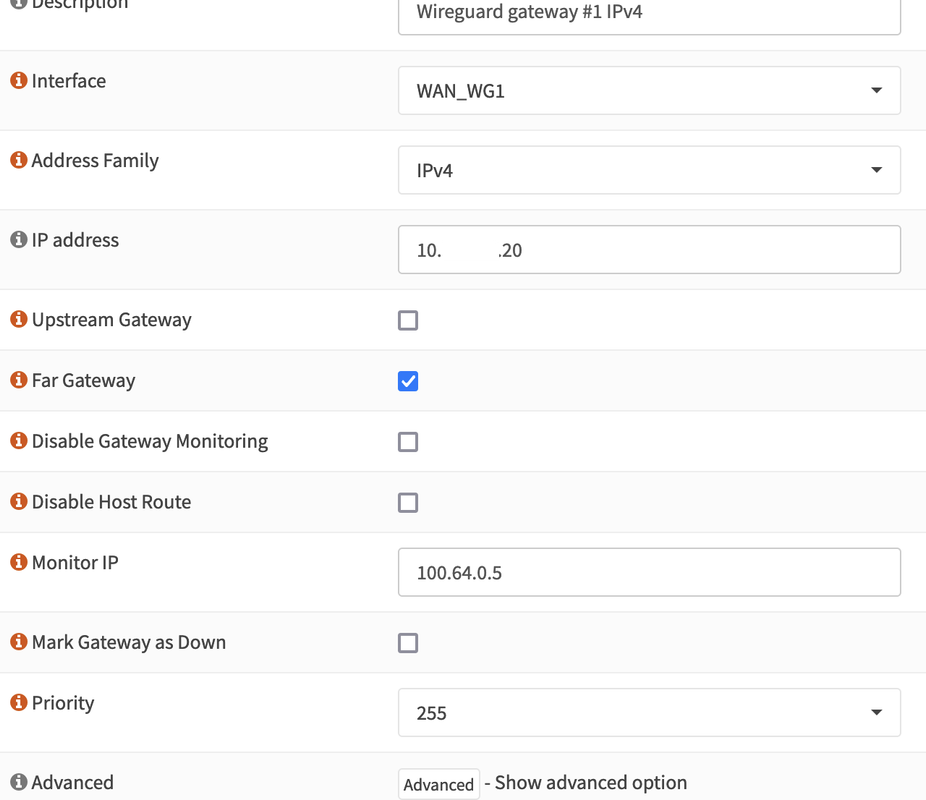
I just noticed a weird problem, none of the .mil domains can be resolved within the my home network managed by Opnsense running Unbound as forwarder. Examples: www.navy.mil, www.af.mil, etc ....
Quick googling points to some DNSSEC issue with these US military domains. However unchecking the box "Enable DNSSEC support" doesn't change anything for me.
I'm using DNS over TLS with Google dns servers. Tried switching to Cloudflare or Quad9. Tried enabling all of them. Still doesn't work. I also made sure the setting "Use system nameservers" is NOT selected to make DoT work. I'm also using OISD blocklist, but i doubt that is the culprit.
If i use my phone with cellular connection or connect to Mullvad VPN service directly from my laptop, i can query these domains (with dig command) and visit them normally.
Anyone having this weird issue here?
Quick googling points to some DNSSEC issue with these US military domains. However unchecking the box "Enable DNSSEC support" doesn't change anything for me.
I'm using DNS over TLS with Google dns servers. Tried switching to Cloudflare or Quad9. Tried enabling all of them. Still doesn't work. I also made sure the setting "Use system nameservers" is NOT selected to make DoT work. I'm also using OISD blocklist, but i doubt that is the culprit.
If i use my phone with cellular connection or connect to Mullvad VPN service directly from my laptop, i can query these domains (with dig command) and visit them normally.
Anyone having this weird issue here?

 "
"