Not yet... sorry!
This section allows you to view all posts made by this member. Note that you can only see posts made in areas you currently have access to.
Pages1
#1
Development and Code Review / Re: Open Source DPI Engine - Netify Agent
April 15, 2020, 04:59:01 PM #2
Development and Code Review / Re: Open Source DPI Engine - Netify Agent
February 24, 2020, 05:22:41 PM
Yes, if there's a good level of interest, we would port the Netify FWA app to OPNsense. The first thing we're doing is porting the Netify Console tool (screenshot) to Python.
#3
General Discussion / Re: Netify Network Intelligence on OPNsense - Now Available
February 14, 2020, 09:28:23 PM
I was the one that wasn't very clear! Unfortunately, we don't have any plans for home users today, but we might something in the future.
#4
General Discussion / Re: Netify Network Intelligence on OPNsense - Now Available
February 13, 2020, 04:55:20 PM
Thanks! Unfortunately, we don't have any current plans for the home user. We have certainly discussed it and it's on our wish list. The big hurdle: pushing some of the machine learning features from the cloud to the agent (OPNsense box). That will make it possible to get a nice feature set that wouldn't need to connect to the cloud (except for signature updates).
#5
General Discussion / Netify Network Intelligence on OPNsense - Now Available
February 11, 2020, 11:00:10 PM
Hi OPNsense Community,
We're a Canadian company that has developed two bits of technology that can help with managing networks at the edge of the Internet.
This one is about the second topic - the cloud-based network intelligence and visibility solution. You can find the open source DPI topic here.
What is Netify?
Netify provides full transparency into what's happening on your network.
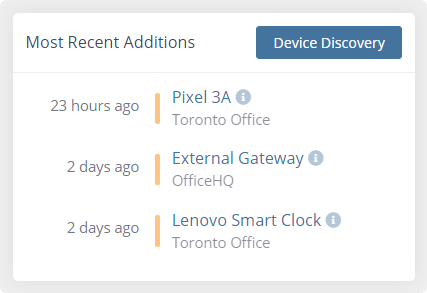
From there, Netify uses its cloud-based network intelligence engine to help you with bandwidth accounting, cybersecurity analysis, compliance, policy enforcement, network troubleshooting, and more. Features include:
Privacy First
Cloud is not for everyone, that's understandable. But it's strange to think that your ISP, DNS provider, Google, Facebook and online marketers may know more than you about the networked devices and traffic patterns inside your organization.
At every step of the Netify development cycle, we have had security and privacy in mind. Deep packet inspection (DPI) sounds intrusive, but it's actually less intrusive when used responsibly. Netify only looks inside the first 5-10 packets of data, not the entire payload. In addition, DPI cannot decrypt your encrypted communications: no SSL interception, no certificate deployment headaches, no breaking end-to-end encryption. It provides a balance that gives you the power to manage your network without compromising encryption and security. We encourage you to learn more about Netify's privacy features and data silos.
In addition, the underlying netifyd deep packet inspection agent is open source (GitLab), so you can see exactly what metadata is being processed. Feel free to poke around and see what happens under the hood.
For large deployments, we also have the option for hosting the infrastructure in a private cloud or data center.
Installation and Configuration
That's enough of the sales pitch. You can find installation and configuration instructions for OPNsense here:
Netify for OPNsense
We have a 7-day no obligation free trial.
Feel free to post comments or questions!
We're a Canadian company that has developed two bits of technology that can help with managing networks at the edge of the Internet.
- An open source deep packet inspection (DPI) engine that is ready to be integrated with the OPNsense firewall, QoS engines and other tidbits.
- A cloud-based network intelligence and visibility solution. The solution provides full transparency into what's happening on your network.
This one is about the second topic - the cloud-based network intelligence and visibility solution. You can find the open source DPI topic here.
What is Netify?
Netify provides full transparency into what's happening on your network.
- Is an employee using VPN or proxies to bypass network policies?
- Are any devices using weak encryption? That needs to be fixed!
- Why is my video conference call so crappy today?
- Are any TVs, printers, or IoT devices connecting to unexpected countries?
- It looks like an old router was hacked, do we have historical forensic data?
- Who is uploading all that data to Instagram? (Karen... it's always Karen)

From there, Netify uses its cloud-based network intelligence engine to help you with bandwidth accounting, cybersecurity analysis, compliance, policy enforcement, network troubleshooting, and more. Features include:
- Device Discovery
- Application Detection
- Protocol Detection
- Risk and Reputation Analysis
- Bandwidth Monitoring
- Hostname Visibility
- Geolocation Information
- Connection Forensics
Privacy First
Cloud is not for everyone, that's understandable. But it's strange to think that your ISP, DNS provider, Google, Facebook and online marketers may know more than you about the networked devices and traffic patterns inside your organization.
At every step of the Netify development cycle, we have had security and privacy in mind. Deep packet inspection (DPI) sounds intrusive, but it's actually less intrusive when used responsibly. Netify only looks inside the first 5-10 packets of data, not the entire payload. In addition, DPI cannot decrypt your encrypted communications: no SSL interception, no certificate deployment headaches, no breaking end-to-end encryption. It provides a balance that gives you the power to manage your network without compromising encryption and security. We encourage you to learn more about Netify's privacy features and data silos.
In addition, the underlying netifyd deep packet inspection agent is open source (GitLab), so you can see exactly what metadata is being processed. Feel free to poke around and see what happens under the hood.
For large deployments, we also have the option for hosting the infrastructure in a private cloud or data center.
Installation and Configuration
That's enough of the sales pitch. You can find installation and configuration instructions for OPNsense here:
Netify for OPNsense
We have a 7-day no obligation free trial.
Feel free to post comments or questions!
#6
Development and Code Review / Open Source DPI Engine - Netify Agent
February 11, 2020, 10:29:27 PM
Hi OPNsense Community,
We're a Canadian company that has developed two bits of technology that can help with managing networks at the edge of the Internet.
This one is about the first topic - the open source DPI engine.
Open Source DPI Engine
We merged the best parts of the open source l7-filter & nDPI projects, and then added our own innovations to create a new deep packet inspection (DPI) engine: netifyd. The engine is able to extract useful metadata from a network conversation:
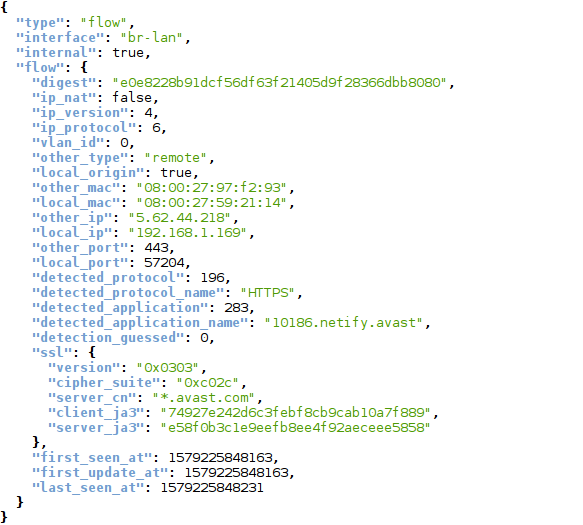
If you are curious, you can see another example of the data stream in our developer documentation - https://www.netify.ai/developer/netify-dpi-engine/netifyd.
So, What's Next?
Okay, that's nice... a stream of network information. So, what's next?
Third party tools in OPNsense can connect to this data stream and do all sorts of different things - firewalling, QoS, reporting, etc. For example, in pfSense (gasp!), a netifyd-based app was created to block applications (e.g. Facebook) and protocols (e.g. BitTorrent). The same feature could be developed for OPNsense of course. Or, the DPI data could be hooked into the QoS engine (even better). In fact, we have another open source package called Netify Firewall Agent that provides the groundwork for making this type of feature.
Please let us know if you are interested in further development. We're happy to kickstart the process if someone is interested in running with it!
Kicking the Tires
If you want to start playing around with the network data flows, you can install netifyd on OPNsense today -- follow the Netify on OPNsense installation documentation. Note: you can skip the "netifyd --enable-sink" step -- that's for enabling the cloud-based Netify product (see other forum thread) and not needed to run the DPI engine. And ditto for skipping provisioning -- it's not needed.
Once netifyd has been started, you can connect to the data stream on the Unix socket: /var/run/netifyd/netifyd.sock. For direct command line interaction hackers, you can view the data stream in your console. First, install the command line jq (JSON processor) tool in OPNsense 19.7.x or 20.1.x with:
You can watch the JSON payloads go by on your terminal using netcat and jq:
It should look something like the screenshot above.
The Future
That's it for now. We'll post updates for the netifyd engine from time to time.
Please only post responses to the open source DPI engine here. Questions/comments about the cloud-based Netify solution should be posted in the other forum thread.
We're a Canadian company that has developed two bits of technology that can help with managing networks at the edge of the Internet.
- An open source deep packet inspection (DPI) engine that is ready to be integrated with the OPNsense firewall, QoS engines and other tidbits.
- A cloud-based network intelligence and visibility solution. The solution provides full transparency into what's happening on your network (screenshots).
This one is about the first topic - the open source DPI engine.
Open Source DPI Engine
We merged the best parts of the open source l7-filter & nDPI projects, and then added our own innovations to create a new deep packet inspection (DPI) engine: netifyd. The engine is able to extract useful metadata from a network conversation:
- Application (e.g. Netflix)
- Protocol (e.g. BitTorrent)
- SSL cipher, SNI, certificate common name
- Hostnames
- Agent strings
- DHCP fingerprints
- Network and packet information
- and more

If you are curious, you can see another example of the data stream in our developer documentation - https://www.netify.ai/developer/netify-dpi-engine/netifyd.
So, What's Next?
Okay, that's nice... a stream of network information. So, what's next?
Third party tools in OPNsense can connect to this data stream and do all sorts of different things - firewalling, QoS, reporting, etc. For example, in pfSense (gasp!), a netifyd-based app was created to block applications (e.g. Facebook) and protocols (e.g. BitTorrent). The same feature could be developed for OPNsense of course. Or, the DPI data could be hooked into the QoS engine (even better). In fact, we have another open source package called Netify Firewall Agent that provides the groundwork for making this type of feature.
Please let us know if you are interested in further development. We're happy to kickstart the process if someone is interested in running with it!
Kicking the Tires
If you want to start playing around with the network data flows, you can install netifyd on OPNsense today -- follow the Netify on OPNsense installation documentation. Note: you can skip the "netifyd --enable-sink" step -- that's for enabling the cloud-based Netify product (see other forum thread) and not needed to run the DPI engine. And ditto for skipping provisioning -- it's not needed.
Once netifyd has been started, you can connect to the data stream on the Unix socket: /var/run/netifyd/netifyd.sock. For direct command line interaction hackers, you can view the data stream in your console. First, install the command line jq (JSON processor) tool in OPNsense 19.7.x or 20.1.x with:
Code Select
pkg add http://pkg.freebsd.org/freebsd:11:x86:64/release_3/All/oniguruma-6.9.0.txz
pkg add http://pkg.freebsd.org/freebsd:11:x86:64/release_3/All/jq-1.6.txz
You can watch the JSON payloads go by on your terminal using netcat and jq:
Code Select
nc -U /var/run/netifyd/netifyd.sock | jq .
It should look something like the screenshot above.
The Future
That's it for now. We'll post updates for the netifyd engine from time to time.
Please only post responses to the open source DPI engine here. Questions/comments about the cloud-based Netify solution should be posted in the other forum thread.
Pages1

 "
"
