Hi,
I was able to reproduce the issue. When the firewall comes up and the configured DNS server is not responding, wireguard does some weird stuff like chosing a random port, see images:
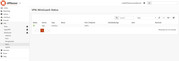
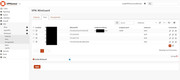
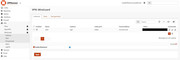
recovery from that state was only possible by fixing the DNS first (obviously) and then either restarting the whole firewall or restating the wireguard instance via the "apply" button. Neither the stale connections nor the restart wireguard cron jobs do work in this case.
I'm sure there is some reason behind this behaviour, however it somewhat degrades the availability of the VPN connections ;-)
best,
Dark-Sider
I was able to reproduce the issue. When the firewall comes up and the configured DNS server is not responding, wireguard does some weird stuff like chosing a random port, see images:



recovery from that state was only possible by fixing the DNS first (obviously) and then either restarting the whole firewall or restating the wireguard instance via the "apply" button. Neither the stale connections nor the restart wireguard cron jobs do work in this case.
I'm sure there is some reason behind this behaviour, however it somewhat degrades the availability of the VPN connections ;-)
best,
Dark-Sider

 "
"
