Ah, crap, ok. Thanks.
This section allows you to view all posts made by this member. Note that you can only see posts made in areas you currently have access to.
Pages1
#2
General Discussion / Re: Generate New SSL Cert For OpenVPN via CLI?
July 29, 2019, 09:04:56 PM
I'm using their NAS as a jump box so I'd have to proxy a few connections, is there no way to generate the certs easily?
#3
General Discussion / Generate New SSL Cert For OpenVPN via CLI?
July 28, 2019, 09:53:01 PM
I have OPNsense setup at my parents house and a VPN server setup in case I ever need to get into their network (I live 3 hours away), and apparently my SSL cert expired. I have shell access to OPNsense, so how can I create the necessary files via the cli so i can rsync them back to myself?
#4
18.1 Legacy Series / Re: Can't Resolve Internal FQDNs Over VPN
May 14, 2018, 07:39:57 PM
Everything except for the expected response from dig, this is what it should return. I get this response when I SSH into my server (192.168.1.7) while connected via the VPN at my parents house.
I get this response when just connected via the VPN
Code Select
; <<>> DiG 9.12.1 <<>> opnsense.brandongolway.us
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 8619
;; flags: qr aa rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 1
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 4096
;; QUESTION SECTION:
;opnsense.brandongolway.us. IN A
;; ANSWER SECTION:
opnsense.brandongolway.us. 3600 IN A 192.168.1.1
;; Query time: 0 msec
;; SERVER: 192.168.1.1#53(192.168.1.1)
;; WHEN: Mon May 14 13:33:44 EDT 2018
;; MSG SIZE rcvd: 86I get this response when just connected via the VPN
Code Select
; <<>> DiG 9.12.1 <<>> opnsense.brandongolway.us
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: REFUSED, id: 10872
;; flags: qr rd ad; QUERY: 0, ANSWER: 0, AUTHORITY: 0, ADDITIONAL: 0
;; WARNING: recursion requested but not available
;; Query time: 22 msec
;; SERVER: 192.168.1.1#53(192.168.1.1)
;; WHEN: Mon May 14 14:10:52 EDT 2018
;; MSG SIZE rcvd: 12 #5
18.1 Legacy Series / Can't Resolve Internal FQDNs Over VPN
May 14, 2018, 06:24:20 PM
I have two VPN servers setup: one in my apartment and one in my parent's house, both are running OPNsense.
Each network has it's own domain names and it's own DNS server (unbound), and they are able to resolve IPs for their respective networks. I initially had an issue where both networks were using 192.168.1.0/24 but I changed my parent's network to 192.168.2.0/24, and now have no issues connecting, but can't resolve FQDNs across subnets.
It looks like unbound is blocking recursion even though I'm specifically allowing it and have all the networks in an ACL, so I'm not sure what else could be blocking it.
Here's the unbound config for my apartment's network (192.168.1.0/24)
ACLs
No domain overrides set.
Here's an example of me trying to resolve a FQDN from my apartment's network, while VPN'd in from my parent's network.
What's the issue?
Each network has it's own domain names and it's own DNS server (unbound), and they are able to resolve IPs for their respective networks. I initially had an issue where both networks were using 192.168.1.0/24 but I changed my parent's network to 192.168.2.0/24, and now have no issues connecting, but can't resolve FQDNs across subnets.
It looks like unbound is blocking recursion even though I'm specifically allowing it and have all the networks in an ACL, so I'm not sure what else could be blocking it.
Here's the unbound config for my apartment's network (192.168.1.0/24)
Code Select
##########################
# Unbound Configuration
##########################
##
# Server configuration
##
server:
chroot: /var/unbound
username: unbound
directory: /var/unbound
pidfile: /var/run/unbound.pid
use-syslog: yes
port: 53
verbosity: 3
hide-identity: no
hide-version: no
harden-referral-path: no
do-ip4: yes
do-ip6: yes
do-udp: yes
do-tcp: yes
do-daemonize: yes
module-config: "validator iterator"
cache-max-ttl: 86400
cache-min-ttl: 0
harden-dnssec-stripped: yes
serve-expired: no
outgoing-num-tcp: 10
incoming-num-tcp: 10
num-queries-per-thread: 4096
outgoing-range: 8192
infra-host-ttl: 900
infra-cache-numhosts: 10000
unwanted-reply-threshold: 0
jostle-timeout: 200
msg-cache-size: 4m
rrset-cache-size: 8m
num-threads: 2
msg-cache-slabs: 4
rrset-cache-slabs: 4
infra-cache-slabs: 4
key-cache-slabs: 4
auto-trust-anchor-file: /var/unbound/root.key
prefetch: no
prefetch-key: no
# Statistics
# Unbound Statistics
statistics-interval: 0
extended-statistics: yes
statistics-cumulative: yes
# Interface IP(s) to bind to
interface: 0.0.0.0
interface: ::0
interface-automatic: yes
# DNS Rebinding
# Access lists
include: /var/unbound/access_lists.conf
# Static host entries
include: /var/unbound/host_entries.conf
# DHCP leases (if configured)
include: /var/unbound/dhcpleases.conf
# Domain overrides
include: /var/unbound/domainoverrides.confACLs
Code Select
access-control: 127.0.0.1/32 allow
access-control: ::1 allow
access-control: 192.168.1.0/24 allow
access-control: 71.172.17.0/24 allow
#Internal
access-control: 10.0.8.0/32 allow_snoop
access-control: 192.168.2.0/24 allow_snoop
No domain overrides set.
Here's an example of me trying to resolve a FQDN from my apartment's network, while VPN'd in from my parent's network.
Code Select
[bran@laptop ~]$ ip a
2: wlp59s0: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc mq state UP group default qlen 1000
link/ether 00:28:f8:54:ad:1c brd ff:ff:ff:ff:ff:ff
inet 192.168.2.203/24 brd 192.168.2.255 scope global dynamic noprefixroute wlp59s0
valid_lft 3297sec preferred_lft 3297sec
inet6 fe80::f4b1:b20f:2d80:1117/64 scope link noprefixroute
valid_lft forever preferred_lft forever
3: tun0: <POINTOPOINT,MULTICAST,NOARP,UP,LOWER_UP> mtu 1500 qdisc fq_codel state UNKNOWN group default qlen 100
link/none
inet 10.0.8.6 peer 10.0.8.5/32 brd 10.0.8.6 scope global noprefixroute tun0
valid_lft forever preferred_lft forever
inet6 fe80::c6a2:c488:c3f0:7fcb/64 scope link stable-privacy
valid_lft forever preferred_lft forever
[bran@laptop ~]$ cat /etc/resolv.conf
# Generated by NetworkManager
search brandongolway.us golway
nameserver 192.168.1.1
nameserver 192.168.2.1
[bran@laptop ~]$ dig @192.168.1.1 opnsense.brandongolway.us
; <<>> DiG 9.12.1 <<>> @192.168.1.1 opnsense.brandongolway.us
; (1 server found)
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: REFUSED, id: 60507
;; flags: qr rd ad; QUERY: 0, ANSWER: 0, AUTHORITY: 0, ADDITIONAL: 0
;; WARNING: recursion requested but not available
;; Query time: 27 msec
;; SERVER: 192.168.1.1#53(192.168.1.1)
;; WHEN: Mon May 14 12:20:40 EDT 2018
;; MSG SIZE rcvd: 12
What's the issue?
#6
18.1 Legacy Series / Re: 2 PS4s, Call of Duty: WWII and OPNsense
February 11, 2018, 03:43:40 AM
It was a comment in the PS4 SubReddit. We still have issues with only one PS4 on, so maybe UPnP is at fault, it does forward two ports automatically.
I'm not used to using OPNsense, and I find the documentation lacking anything regarding the firewall. I'm largely a noob when it comes to firewalls. So I tend to have a lot of issues. Also for some reason I can't see any activity in the live firewall log, yet the state summary shows many active connections from his PS4 to other IPs. His PS4 says that it can't open port 3074...yet I clearly see connections on 3074 on his IP.
How can I put his PS4 in the DMZ (outside of/not blocked by the firewall)? His friend told him to do that and I told him the risks involved and he was like "I don't care, do it!". His internal IP is 192.168.1.244 and OPNsense is 192.168.1.1
I'm not used to using OPNsense, and I find the documentation lacking anything regarding the firewall. I'm largely a noob when it comes to firewalls. So I tend to have a lot of issues. Also for some reason I can't see any activity in the live firewall log, yet the state summary shows many active connections from his PS4 to other IPs. His PS4 says that it can't open port 3074...yet I clearly see connections on 3074 on his IP.
How can I put his PS4 in the DMZ (outside of/not blocked by the firewall)? His friend told him to do that and I told him the risks involved and he was like "I don't care, do it!". His internal IP is 192.168.1.244 and OPNsense is 192.168.1.1
#7
18.1 Legacy Series / Re: 2 PS4s, Call of Duty: WWII and OPNsense
February 10, 2018, 09:40:34 PM
I tried it with just pure UPnP first and it didn't work, after time spent googling I found a Network Engineer state that the way he got it to work was to forward the "party" ports to the specific internal IPs (since they use a range of 3 ports now), and let UPnP handle everything. That is how I have it setup, UPnP forwards the ports (different ones to different IPs, I watched the UPnP connection status), yet WWII still bitches about NAT type 2 or 3, and in turn, my clueless roommate starts bitching about the NAT types, which really mean nothing to us in the IT field.
#8
18.1 Legacy Series / 2 PS4s, Call of Duty: WWII and OPNsense
February 06, 2018, 03:01:41 PM
Hey,
So I know this is a long standing issue with *sense routers, I had the issue with pfSense for months and couldn't figure it out. I always had NAT type 2 or type 3. I ended up buying Asus' $400 GT-AC5300 "Gaming" router which has great hardware (4 core ARM processor clocked at ~1.5 GHz, 2 GB RAM, 8 NICs [2 support bonding], 8 antennas for MIMO AC) but the interface is an abomination and it doesn't support Merlin :( Everything has the word "game" attached to it for no other reason than for calling it a "gaming router", like the malware and parental filtering was called "Game Protection" or something stupid. I instantly had an NAT type 1/ open NAT in CoD WWII as soon as I set it up, the problem was that it made everything else a pain in the ass for me (running my webserver, using a VPN, etc...).
So after about 3-4 months of using that I got pissed and switched the GT-AC5300 to Access Point mode to disable all of it's unnecessary functions (love that it has this option), and put OPNsense 18.1 as my router. I installed the UPnP packages and it forwarded the ports...but of course it showed up as NAT type 2 and my roommate immediately started bitching because we can no longer connect to other people or invite them, yet we can play in public non-invite games, usually without issue.
I believe the issue is, as I saw someone else state on here, is the fact that I have two PS4s trying to use the same ports at the same time, I believe he can connect to his friends without issue when he's just playing, but as soon as I join sh!t hits the fan.
This seems to be resolvable since the Asus router is able to fix it, but I'm not a network guru, just a sysadmin so any help is appreciated.
So I know this is a long standing issue with *sense routers, I had the issue with pfSense for months and couldn't figure it out. I always had NAT type 2 or type 3. I ended up buying Asus' $400 GT-AC5300 "Gaming" router which has great hardware (4 core ARM processor clocked at ~1.5 GHz, 2 GB RAM, 8 NICs [2 support bonding], 8 antennas for MIMO AC) but the interface is an abomination and it doesn't support Merlin :( Everything has the word "game" attached to it for no other reason than for calling it a "gaming router", like the malware and parental filtering was called "Game Protection" or something stupid. I instantly had an NAT type 1/ open NAT in CoD WWII as soon as I set it up, the problem was that it made everything else a pain in the ass for me (running my webserver, using a VPN, etc...).
So after about 3-4 months of using that I got pissed and switched the GT-AC5300 to Access Point mode to disable all of it's unnecessary functions (love that it has this option), and put OPNsense 18.1 as my router. I installed the UPnP packages and it forwarded the ports...but of course it showed up as NAT type 2 and my roommate immediately started bitching because we can no longer connect to other people or invite them, yet we can play in public non-invite games, usually without issue.
I believe the issue is, as I saw someone else state on here, is the fact that I have two PS4s trying to use the same ports at the same time, I believe he can connect to his friends without issue when he's just playing, but as soon as I join sh!t hits the fan.
This seems to be resolvable since the Asus router is able to fix it, but I'm not a network guru, just a sysadmin so any help is appreciated.
#9
16.7 Legacy Series / Re: OpenVPN: No DNS resolution Using Internal Resolver
September 09, 2016, 07:25:14 AM
No one can help?
#10
16.7 Legacy Series / [SOLVED] OpenVPN: No DNS resolution Using Internal Resolver
August 30, 2016, 10:38:34 AM
Hey Guys, I setup OpenVPN (for the first time ever) on my router and I can connect just fine, and at first DNS didn't work at all when forcing all resolution queries through the VPN. After some searching I saw that a good way to check it to push a public DNS server out from the VPN server, so I set mine to 8.8.8.8, disconnected, and then reconnected and external DNS resolution worked perfectly (google and other sites).
VPN clients (which are on subnet 10.10.10.0/32) are allowed to contact my main network (192.168.1.0/24) and routing is correct since I can access my internal sites and clients via their IP addresses, but internal DNS resolution doesn't work at all when I push my internal DNS resolver at 192.168.1.1, nor does external DNS resolution (Google, yahoo, etc...). What's wrong here? I don't see any requests blocked by the firewall.
Here's my server config
Client Config
Edit:After some more investigation, it seems that DNS queries are going to 10.10.10.1:53 instead of 192.168.1.1:53, even though I'm forcing 192.168.1.1!
VPN clients (which are on subnet 10.10.10.0/32) are allowed to contact my main network (192.168.1.0/24) and routing is correct since I can access my internal sites and clients via their IP addresses, but internal DNS resolution doesn't work at all when I push my internal DNS resolver at 192.168.1.1, nor does external DNS resolution (Google, yahoo, etc...). What's wrong here? I don't see any requests blocked by the firewall.
Here's my server config
Code Select
dev ovpns1
verb 1
dev-type tun
dev-node /dev/tun1
writepid /var/run/openvpn_server1.pid
#user nobody
#group nobody
script-security 3
daemon
keepalive 10 60
ping-timer-rem
persist-tun
persist-key
proto udp
cipher AES-256-CBC
auth SHA512
up /usr/local/sbin/ovpn-linkup
down /usr/local/sbin/ovpn-linkdown
client-connect /usr/local/sbin/openvpn.attributes.sh
client-disconnect /usr/local/sbin/openvpn.attributes.sh
local [external IP]
tls-server
server 10.10.10.0 255.255.255.0
client-config-dir /var/etc/openvpn-csc/1
client-cert-not-required
username-as-common-name
auth-user-pass-verify "/usr/local/sbin/ovpn_auth_verify user 'Time based One Time Password VPN Access Server' false server1" via-env
tls-verify "/usr/local/sbin/ovpn_auth_verify tls 'SSL+VPN+Server+Certificate' 1"
lport 1194
management /var/etc/openvpn/server1.sock unix
push "route 192.168.1.0 255.255.255.0"
push "dhcp-option DOMAIN mydomain.us"
push "dhcp-option DNS 192.168.1.1"
push "register-dns"
ca /var/etc/openvpn/server1.ca
cert /var/etc/openvpn/server1.cert
key /var/etc/openvpn/server1.key
dh /usr/local/etc/dh-parameters.4096
tls-auth /var/etc/openvpn/server1.tls-auth 0
comp-lzo adaptiveClient Config
Code Select
dev tun
persist-tun
persist-key
cipher AES-256-CBC
auth SHA512
tls-client
client
resolv-retry infinite
remote [external IP] 1194 udp
lport 0
auth-user-pass
ca router-udp-1194-ca.crt
tls-auth router-udp-1194-tls.key 1
ns-cert-type server
comp-lzo adaptiveEdit:After some more investigation, it seems that DNS queries are going to 10.10.10.1:53 instead of 192.168.1.1:53, even though I'm forcing 192.168.1.1!
#11
16.7 Legacy Series / Re: Confused About Traffic Shaping
August 20, 2016, 06:49:15 PM
No one can help me with this?
#12
16.7 Legacy Series / Problems With Traffic Shaping
August 12, 2016, 10:54:32 PM
I've read the help section and messed around with it for a few days but it still doesn't seem like I'm getting the results that I want.
I do a lot of torrenting and downloading other large files via Usenet and HTTP, but I also stream a lot of media inside my network and sometimes externally to my friends. I'm also hosting a VM (192.168.1.84) with a Plex server for my friend and ideally I'd like to reserve about 25 Mbps of my upload for her, specifically for Plex, to make sure that she can always stream media from my server to her device smoothly, no matter what I'm doing.
The top priority in my network should be Nvidia's GameStream from my desktop (192.168.1.37) to their GeForce Now streaming service (from their SuperComputers to your Shield, port list) should be given top priority. After that, I would like to give SSH and Web traffic second priority. I host a web server on 192.168.1.16 so that should be given high priority as well. Lastly should be my peer to peer traffic, which would be Usenet and Torrents. Ideally I would like to limit these to about 75% of my total bandwidth, and have them be the lowest priority. I would like Usenet traffic to be a higher priority than Torrent traffic since I use that more often. Torrents should be the lowest priority since I mostly just seed torrents and don't download that often. I have about 100+ torrents currently seeding.
I've set up my Pipes, Queues, and Rules as you see below, and when I'm downloading a few torrents that is only using about 50% of my total bandwidth, web traffic slows to a crawl (about 10-35 Mbps on a 100 Mbps Verizon Fios connection), so that would tell me that I don't have my Traffic Shaping setup correctly. If I pause all the torrents, everything is snappy again!
It's definitely not a problem with performance of my hardware since I'm using an Intel(R) Atom(TM) CPU D2550 @ 1.86GHz (4 cores) with 4 GB of RAM, only 32% of which is utilized and only about 10% of my processor is utilized when all torrents are seeding and about 3 are downloading.
Pipes
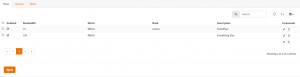
Queues
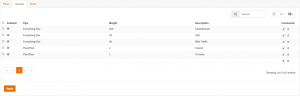
Rules
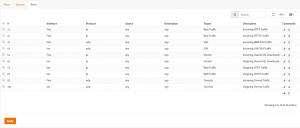
I do a lot of torrenting and downloading other large files via Usenet and HTTP, but I also stream a lot of media inside my network and sometimes externally to my friends. I'm also hosting a VM (192.168.1.84) with a Plex server for my friend and ideally I'd like to reserve about 25 Mbps of my upload for her, specifically for Plex, to make sure that she can always stream media from my server to her device smoothly, no matter what I'm doing.
The top priority in my network should be Nvidia's GameStream from my desktop (192.168.1.37) to their GeForce Now streaming service (from their SuperComputers to your Shield, port list) should be given top priority. After that, I would like to give SSH and Web traffic second priority. I host a web server on 192.168.1.16 so that should be given high priority as well. Lastly should be my peer to peer traffic, which would be Usenet and Torrents. Ideally I would like to limit these to about 75% of my total bandwidth, and have them be the lowest priority. I would like Usenet traffic to be a higher priority than Torrent traffic since I use that more often. Torrents should be the lowest priority since I mostly just seed torrents and don't download that often. I have about 100+ torrents currently seeding.
I've set up my Pipes, Queues, and Rules as you see below, and when I'm downloading a few torrents that is only using about 50% of my total bandwidth, web traffic slows to a crawl (about 10-35 Mbps on a 100 Mbps Verizon Fios connection), so that would tell me that I don't have my Traffic Shaping setup correctly. If I pause all the torrents, everything is snappy again!
It's definitely not a problem with performance of my hardware since I'm using an Intel(R) Atom(TM) CPU D2550 @ 1.86GHz (4 cores) with 4 GB of RAM, only 32% of which is utilized and only about 10% of my processor is utilized when all torrents are seeding and about 3 are downloading.
Pipes

Queues

Rules

Pages1

 "
"
