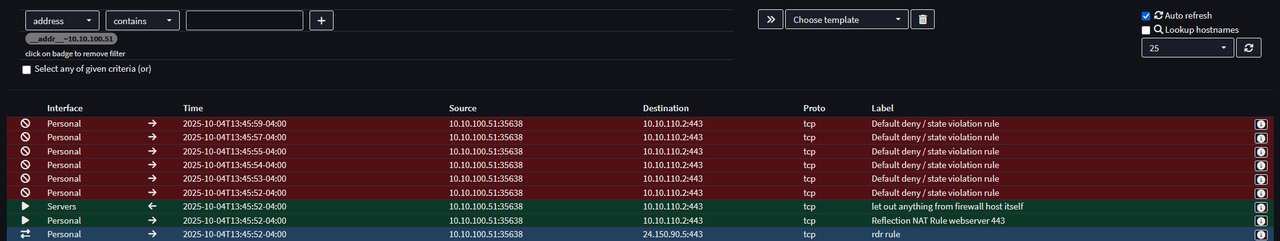
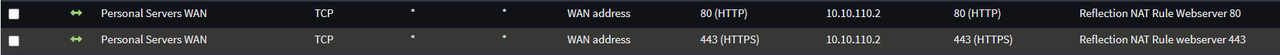
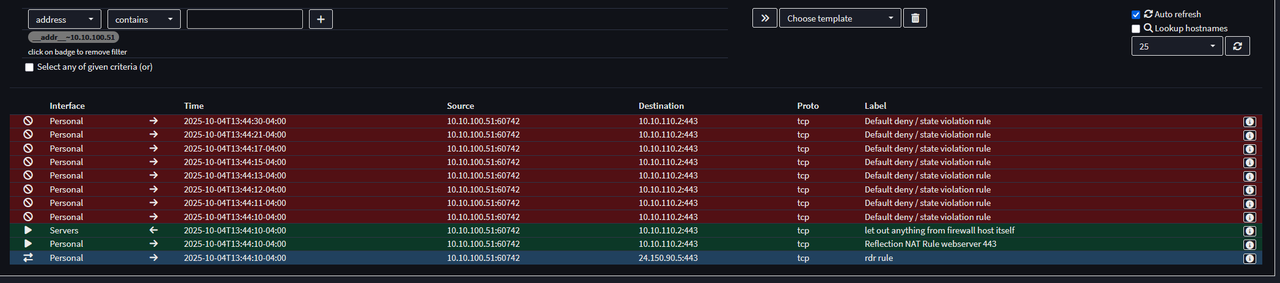
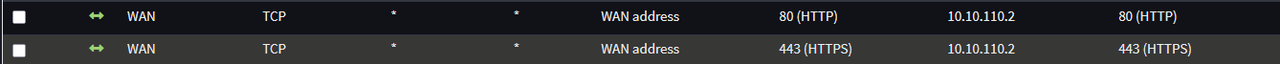
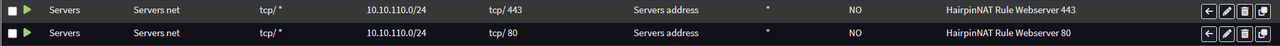
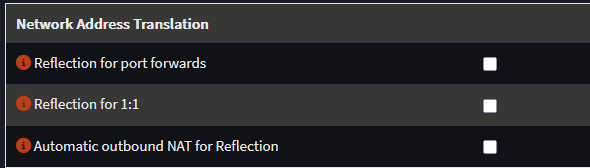
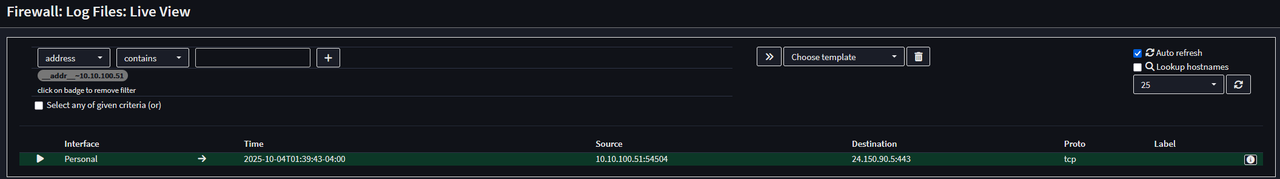
Quote from: Patrick M. Hausen on October 06, 2025, 08:13:47 PMIf the client and the server share a network why do you want the client traffic to go through OPNsense in the first place?
Optimally I don't want them to, and I would even prefer to have two instances of Caddy on the separate networks to remove the need for the current setup. In the past when I wanted to do that it wasn't possible due to my domain registrar, but I think it is possible now that I have switched to one that supports API access. Since that should be possible I'll just solve the problem that way.
I was unaware of how the network connections worked, I did not expect it to change the packets route in the way that it does. Thank you for the information.

 "
"