QuoteHowever, in this very setup you're doomed without NAT.I do not understand why this setup is doomed without NAT. Everything behind the edge router (and including the edge router) is a private network. This is a normal setup for an internal firewall, and best practice in an corporate environment.
Here is an example that I found:

As shown in the image, I am trying to implement the internal firewall. In such a scenario there is no need to have NAT, for systems in the internal or EDMZ network to access systems in the DMZ network.
QuoteCreate a transfer network and proper routing on the edge routerAs I stated in the original post, when the OPNsense firewall is disabled, systems on both sides of OPNsense can access each other. This means that the routing is working.
The problem I am trying to resolve while removing double NAT.
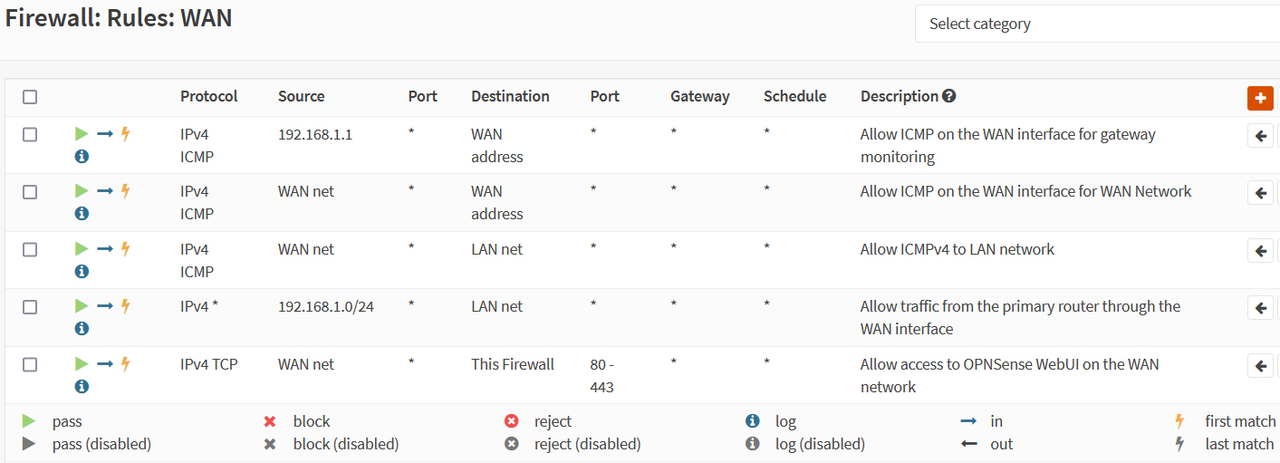
When the firewall is enabled and NAT is disabled, systems on the WAN side of OPNsense can access the LAN side systems, but not the other way round (these are still all internal private systems on my network). This means that OPNsense is either blocking the traffic or mis-routing in this configuration.
What could be causing this issue?

 "
"