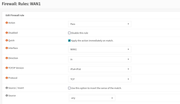
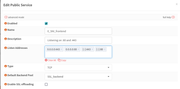
Quote from: TrustedComputer on August 07, 2025, 03:19:21 PM@_Alchemist_ I realize this is 4 years later, and we have instances instead of servers now. But shouldn'tCode Select- Interface WAN2
- Protocol UDP
- Destination WAN1 address
beCode Select- Interface WAN2
- Protocol UDP
- Destination WAN2 address
?
You are correct, that's a typo.

 "
"