Hi All. I am totally new to network and switching/routing. I have a background in virtualization but want
to learn about networks and maybe look into vSphere NSX later.
I have deployed a virtual OpnSense device on one of the ESXi hosts in my homelab, and wanted to look into basic routing between vlans as the first task.
Virtual opnsense device:
OPNsense 22.7.11_1-amd64
FreeBSD 13.1-RELEASE-p5
OpenSSL 1.1.1s 1 Nov 2022
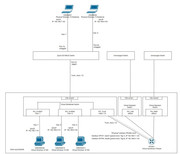
Four "physical" interfaces (they are virtual in the ESXi, but for opnsense they are physical):
1 LAN(lan) vmx2
2 TRUNK(opt1) vmx3
3 WAN(wan) vmx1
4 Unconfigured and not connected.
I first deployed and configured the virtual firewall with WAN and LAN. Everything went smooth. I have LAN and WAN connectivity.
I have patched the firewall so internet connectivity is OK.
After that I configured interface 2 as a Trunk with two virtual interfaces/vlans. vlan 7 (vlan tag 7), and vlan 8 (vlan tag 8 ).
OPT07 (Parent: vmx3, Tag7): IP address: 192.168.7.1 /24
OPT08 (Parent: vmx3, Tag8): IP address: 192.168.8.1 /24
On the ESXi host I configured a virtual distributed switch with a trunk-portgroup and connected it to the virtual firewall interface 2.
I applied any/any rules on the physical interfaces and on the two virtual interfaces. (just to get basic connectivity working, I will look into modifyoing the rules later)
I configured DHCPv4 service on the two virtual interfaces.
OPT07: Range: 192.168.7.100 - 192.168.7.150
OPT08: Range: 192.168.8.100 - 192.168.8.150
(The automatically generated firewall rules were created on the virtual interfaces)
I deployed three virtual windows 10 machines, connected to the same virtual switch, but to portgroups with untagged ports. one in vlan7 and two in vlan 8.
The virtual switch is connect to a zyxel GS1900-E24 managed switch where the port is configured as a tagged trunk port.
I have connected two physical windows 10 machines the zyxel switch in two access ports, one with vlan7 and one with vlan8.
So far so good. All five windows 10 machines gets a DHCP address for the opnsense firewall.
WINNB001: 192.168.7.102
WINNB002: 192.168.8.103
WINWS0009: 192.168.7.101
WINWS0010: 192.168.8.101
WINWS0011: 192.168.8.102
The two clients in vlan7 can ping each other, and they can ping the firewall on 192.168.7.1
The three clients in vlan8 can ping each other, and they can ping the firewall on 192.168.8.1
So now I have two isolated networks, and I would like to do routing between them in the firewall.
How do I do that? I guess I have to configure gateways and routes?
Sorry for the long post, and for asking something that might have a very basic answer. :)
BR and thanks in advance
SorenV
to learn about networks and maybe look into vSphere NSX later.
I have deployed a virtual OpnSense device on one of the ESXi hosts in my homelab, and wanted to look into basic routing between vlans as the first task.
Virtual opnsense device:
OPNsense 22.7.11_1-amd64
FreeBSD 13.1-RELEASE-p5
OpenSSL 1.1.1s 1 Nov 2022

Four "physical" interfaces (they are virtual in the ESXi, but for opnsense they are physical):
1 LAN(lan) vmx2
2 TRUNK(opt1) vmx3
3 WAN(wan) vmx1
4 Unconfigured and not connected.
I first deployed and configured the virtual firewall with WAN and LAN. Everything went smooth. I have LAN and WAN connectivity.
I have patched the firewall so internet connectivity is OK.
After that I configured interface 2 as a Trunk with two virtual interfaces/vlans. vlan 7 (vlan tag 7), and vlan 8 (vlan tag 8 ).
OPT07 (Parent: vmx3, Tag7): IP address: 192.168.7.1 /24
OPT08 (Parent: vmx3, Tag8): IP address: 192.168.8.1 /24
On the ESXi host I configured a virtual distributed switch with a trunk-portgroup and connected it to the virtual firewall interface 2.
I applied any/any rules on the physical interfaces and on the two virtual interfaces. (just to get basic connectivity working, I will look into modifyoing the rules later)
I configured DHCPv4 service on the two virtual interfaces.
OPT07: Range: 192.168.7.100 - 192.168.7.150
OPT08: Range: 192.168.8.100 - 192.168.8.150
(The automatically generated firewall rules were created on the virtual interfaces)
I deployed three virtual windows 10 machines, connected to the same virtual switch, but to portgroups with untagged ports. one in vlan7 and two in vlan 8.
The virtual switch is connect to a zyxel GS1900-E24 managed switch where the port is configured as a tagged trunk port.
I have connected two physical windows 10 machines the zyxel switch in two access ports, one with vlan7 and one with vlan8.
So far so good. All five windows 10 machines gets a DHCP address for the opnsense firewall.
WINNB001: 192.168.7.102
WINNB002: 192.168.8.103
WINWS0009: 192.168.7.101
WINWS0010: 192.168.8.101
WINWS0011: 192.168.8.102
The two clients in vlan7 can ping each other, and they can ping the firewall on 192.168.7.1
The three clients in vlan8 can ping each other, and they can ping the firewall on 192.168.8.1
So now I have two isolated networks, and I would like to do routing between them in the firewall.
How do I do that? I guess I have to configure gateways and routes?
Sorry for the long post, and for asking something that might have a very basic answer. :)
BR and thanks in advance
SorenV

 "
"
