This section allows you to view all posts made by this member. Note that you can only see posts made in areas you currently have access to.
#1
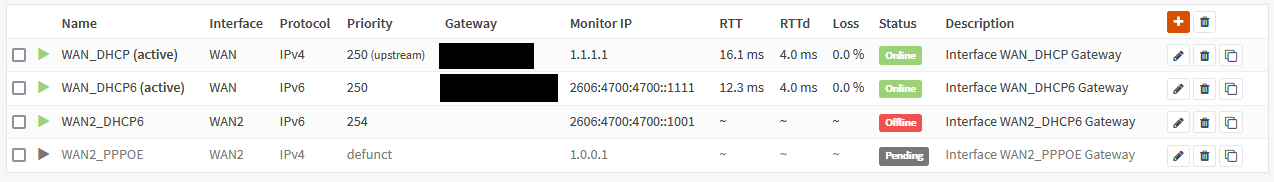
21.7 Legacy Series / [SOLVED] Multi-WAN - IPv4 Gateway disabled when down
January 07, 2022, 05:16:23 PM #2
21.7 Legacy Series / Re: IPv6 - Block traffic between local interfaces
October 21, 2021, 05:09:31 PMQuote from: IsaacFL on October 21, 2021, 04:57:20 PM
You could also create an Alias for your Top Level ipv6 prefix. (ie aaaa:bbbb:cccc:dd00::/56).
Then you have a rule that passes the local traffic that you want and anther a rule that blocks the Total Prefix.
Then after that rule that passes any. That way you don't have any unused prefixes being routed out the WAN also.
That's a good solution for a network with a static prefix. But in my test setup i only have a dynamic prefix.
#3
21.7 Legacy Series / Re: IPv6 - Block traffic between local interfaces
October 21, 2021, 04:42:32 PMQuote from: pmhausen on October 21, 2021, 04:08:19 PM
You can use such a group object and "invert destination" for a pass rule to avoid the explicit block rules.
Quote from: IsaacFL on October 21, 2021, 04:38:29 PM
The approach I use, is to create a Firewall Group called LocalGroup with all of my local interfaces added. This gives you an alias of "LocalGroup Net" that you can use to allow local traffic or block local traffic. This is especially useful if you have dynamic prefix as it gets updated automatically.
Here is a short summary what i did:
- Create a Firewall Group with both interfaces
- Create in the new Firewall Group a rule that passes all traffic, which is not going to the both local interfaces
But when i add an interface now and forget to add to the Group, it will be accessible by the networks in the group.
#4
21.7 Legacy Series / Re: IPv6 - Block traffic between local interfaces
October 21, 2021, 04:07:15 PMQuote from: IsaacFL on October 21, 2021, 03:19:08 PM
You can also create a Firewall Group with your non ipv6 interfaces and then your rule would block the Group Net
Thank you. That is an acceptable way. I would prefer a rule where i can block all other interfaces automatically, without adding them to a Firewall Group, but thats not possible, isn't it?
A rule like "pass anything that does not have a interface as destination that is currently assigned to OPNSense"
#5
21.7 Legacy Series / IPv6 - Block traffic between local interfaces
October 21, 2021, 12:10:43 PM
Hi,
i'm trying to learn IPv6 and have an test setup with two VLANs.
Now i try to block the IPv6-traffic between the interfaces, so only internet access is possible.
In IPv4 i solved this with an rule that passed every traffic that is not going to an private ip address. So the default deny rule blocks the local traffic.
In IPv6 every device gets an public ip address. So if i pass all traffic to 2000::/3 also the traffic between the local interfaces is allowed.
One solution would be to manually block every other IPv6 subnet, but this is much work when it comes to bigger networks and has a high risk of failures.
Has anyone a idea?
Greetings
Jens
i'm trying to learn IPv6 and have an test setup with two VLANs.
Now i try to block the IPv6-traffic between the interfaces, so only internet access is possible.
In IPv4 i solved this with an rule that passed every traffic that is not going to an private ip address. So the default deny rule blocks the local traffic.
In IPv6 every device gets an public ip address. So if i pass all traffic to 2000::/3 also the traffic between the local interfaces is allowed.
One solution would be to manually block every other IPv6 subnet, but this is much work when it comes to bigger networks and has a high risk of failures.
Has anyone a idea?
Greetings
Jens
#6
21.7 Legacy Series / Re: FreeRadius - error:14094419:SSL routines:ssl3_read_bytes:tlsv1 alert access deni
October 05, 2021, 06:31:49 PMQuote from: chemlud on October 04, 2021, 04:32:36 PM
Wrong forum? ;-)
FreeRadius-Forum or Microsoft?
#7
21.7 Legacy Series / Re: FreeRadius - error:14094419:SSL routines:ssl3_read_bytes:tlsv1 alert access deni
October 04, 2021, 03:43:21 PMQuote from: chemlud on October 01, 2021, 10:54:24 PM
https://forum.opnsense.org/index.php?topic=18235.0
http://lists.freeradius.org/pipermail/freeradius-users/2020-November/099072.html
Thx, that worked. But it should work without modifying the registry. I cannot edit all registries of all clients.
#8
21.7 Legacy Series / Re: FreeRadius - error:14094419:SSL routines:ssl3_read_bytes:tlsv1 alert access deni
October 01, 2021, 10:45:58 PMQuote from: chemlud on October 01, 2021, 10:19:25 PM
So which client is sending this ClientHello with TLS 1.3?
I'm not sure either Windows 10 or the Bintec w2022ac
#9
21.7 Legacy Series / Re: FreeRadius - error:14094419:SSL routines:ssl3_read_bytes:tlsv1 alert access deni
October 01, 2021, 10:00:07 PMQuote from: chemlud on October 01, 2021, 08:57:52 PMCode Select...
(2) eap_peap: (TLS) recv TLS 1.3 Handshake, ClientHello
(2) eap_peap: (TLS) send TLS 1.2 Alert, fatal handshake_failure
(2) eap_peap: ERROR: (TLS) Alert write:fatal:handshake failure
...
Why is a ClientHello for TLS 1.3 answered with TLS 1.2?
Maybe because you setCode Selecttls_max_version = "1.2"
This can't work, imho...
tls_max_version = "1.2" - This is the standard configuration of opnsense
When i set it to tls_max_version = "1.3" the follow warning is in the logs:
Code Select
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
!! FORCING MAXIMUM TLS VERSION TO TLS 1.2 !!
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
!! There is no standard for using this EAP method with TLS 1.3
!! Please set tls_max_version = "1.2"
!! FreeRADIUS only supports TLS 1.3 for special builds of wpa_supplicant and Windows
!! This limitation is likely to change in late 2021.
!! If you are using this version of FreeRADIUS after 2021, you will probably need to upgrade
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!The error is always the same.
#10
21.7 Legacy Series / Re: FreeRadius - error:14094419:SSL routines:ssl3_read_bytes:tlsv1 alert access deni
October 01, 2021, 08:25:42 PM
But now i notice that the error message changed:
First it was (see original post):
Now it is:
First it was (see original post):
Code Select
(12) eap_peap: ERROR: (TLS) Alert read:fatal:access denied
(12) eap_peap: ERROR: (TLS) Error in fragmentation logic - code 1
(12) eap_peap: ERROR: (TLS) Failed reading application data from OpenSSL: error:14094419:SSL routines:ssl3_read_bytes:tlsv1 alert access denied
(12) eap_peap: ERROR: [eaptls process] = fail
(12) eap: ERROR: Failed continuing EAP PEAP (25) session. EAP sub-module failedNow it is:
Code Select
(2) eap: Expiring EAP session with state 0x6988124468ed0b5d
(2) eap: Finished EAP session with state 0x6988124468ed0b5d
(2) eap: Previous EAP request found for state 0x6988124468ed0b5d, released from the list
(2) eap: Peer sent packet with method EAP PEAP (25)
(2) eap: Calling submodule eap_peap to process data
(2) eap_peap: (TLS) EAP Peer says that the final record size will be 162 bytes
(2) eap_peap: (TLS) EAP Got all data (162 bytes)
(2) eap_peap: (TLS) Handshake state - before SSL initialization
(2) eap_peap: (TLS) Handshake state - Server before SSL initialization
(2) eap_peap: (TLS) Handshake state - Server before SSL initialization
(2) eap_peap: (TLS) recv TLS 1.3 Handshake, ClientHello
(2) eap_peap: (TLS) send TLS 1.2 Alert, fatal handshake_failure
(2) eap_peap: ERROR: (TLS) Alert write:fatal:handshake failure
(2) eap_peap: ERROR: (TLS) Server : Error in error
(2) eap_peap: ERROR: (TLS) Failed reading from OpenSSL: error:1417A0C1:SSL routines:tls_post_process_client_hello:no shared cipher
(2) eap_peap: ERROR: (TLS) System call (I/O) error (-1)
(2) eap_peap: ERROR: (TLS) EAP Receive handshake failed during operation
(2) eap_peap: ERROR: [eaptls process] = fail
(2) eap: ERROR: Failed continuing EAP PEAP (25) session. EAP sub-module failed
#11
21.7 Legacy Series / Re: FreeRadius - error:14094419:SSL routines:ssl3_read_bytes:tlsv1 alert access deni
October 01, 2021, 08:22:32 PMQuote from: KHE on October 01, 2021, 07:17:26 PM
Hi,
I saw the following in your log:Code Selecttls-config tls-common {
... <snip> ...
cipher_list = "DEFAULT"
cipher_server_preference = no
ecdh_curve = "prime256v1"
tls_max_version = "1.2"
tls_min_version = "1.0"
... <snip> ...
}
tls: In order to use TLS 1.0 and/or TLS 1.1, you likely need to set: cipher_list = "DEFAULT@SECLEVEL=1"
Your cipher_list is set to "DEFAULT" not to "DEFAULT@SECLEVEL=1"
KH
I've tried it also with cipher_list = "DEFAULT@SECLEVEL=1". Exactly the same problem.
#12
21.7 Legacy Series / Re: FreeRadius - error:14094419:SSL routines:ssl3_read_bytes:tlsv1 alert access deni
October 01, 2021, 06:15:54 PM
I tried a few things over the day, but nothing worked. Maybe my log helps?
Code Select
Starting - reading configuration files ...
####READING files#####
main {
security {
allow_core_dumps = no
}
name = "radiusd"
prefix = "/usr/local"
localstatedir = "/var"
logdir = "/var/log"
run_dir = "/var/run/radiusd"
}
main {
name = "radiusd"
prefix = "/usr/local"
localstatedir = "/var"
sbindir = "/usr/local/sbin"
logdir = "/var/log"
run_dir = "/var/run/radiusd"
libdir = "/usr/local/lib/freeradius-3*"
radacctdir = "/var/log/radacct"
hostname_lookups = no
max_request_time = 30
cleanup_delay = 5
max_requests = 16384
postauth_client_lost = no
pidfile = "/var/run/radiusd/radiusd.pid"
checkrad = "/usr/local/sbin/checkrad"
debug_level = 0
proxy_requests = yes
log {
stripped_names = no
auth = yes
auth_badpass = yes
auth_goodpass = yes
colourise = yes
msg_denied = "You are already logged in - access denied"
}
resources {
}
security {
max_attributes = 200
reject_delay = 1.000000
status_server = yes
}
}
radiusd: #### Loading Realms and Home Servers ####
proxy server {
retry_delay = 5
retry_count = 3
default_fallback = no
dead_time = 120
wake_all_if_all_dead = no
}
home_server localhost {
ipaddr = ####IP-Address####
port = 1812
type = "auth"
secret = <<< secret >>>
response_window = 20.000000
response_timeouts = 1
max_outstanding = 65536
zombie_period = 40
status_check = "status-server"
ping_interval = 30
check_interval = 30
check_timeout = 4
num_answers_to_alive = 3
revive_interval = 120
limit {
max_connections = 16
max_requests = 0
lifetime = 0
idle_timeout = 0
}
coa {
irt = 2
mrt = 16
mrc = 5
mrd = 30
}
}
home_server_pool my_auth_failover {
type = fail-over
home_server = localhost
}
realm example.com {
auth_pool = my_auth_failover
}
realm LOCAL {
}
radiusd: #### Loading Clients ####
client WLAN {
ipaddr = ####IP-Address####/24
require_message_authenticator = no
secret = <<< secret >>>
shortname = "WLAN"
limit {
max_connections = 16
lifetime = 0
idle_timeout = 30
}
}
Debugger not attached
# Creating Auth-Type = mschap
# Creating Auth-Type = eap
# Creating Auth-Type = PAP
# Creating Auth-Type = CHAP
# Creating Auth-Type = MS-CHAP
# Creating Auth-Type = digest
radiusd: #### Instantiating modules ####
modules {
# Loaded module rlm_eap
# Loading module "eap" from file /usr/local/etc/raddb/mods-enabled/eap
eap {
default_eap_type = "mschapv2"
timer_expire = 60
ignore_unknown_eap_types = no
cisco_accounting_username_bug = no
max_sessions = 16384
}
# Loaded module rlm_digest
# Loading module "digest" from file /usr/local/etc/raddb/mods-enabled/digest
# Loaded module rlm_utf8
# Loading module "utf8" from file /usr/local/etc/raddb/mods-enabled/utf8
# Loaded module rlm_pap
# Loading module "pap" from file /usr/local/etc/raddb/mods-enabled/pap
pap {
normalise = yes
}
# Loaded module rlm_cache
# Loading module "cache_eap" from file /usr/local/etc/raddb/mods-enabled/cache_eap
cache cache_eap {
driver = "rlm_cache_rbtree"
key = "%{%{control:State}:-%{%{reply:State}:-%{State}}}"
ttl = 15
max_entries = 0
epoch = 0
add_stats = no
}
# Loaded module rlm_attr_filter
# Loading module "attr_filter.post-proxy" from file /usr/local/etc/raddb/mods-enabled/attr_filter
attr_filter attr_filter.post-proxy {
filename = "/usr/local/etc/raddb/mods-config/attr_filter/post-proxy"
key = "%{Realm}"
relaxed = no
}
# Loading module "attr_filter.pre-proxy" from file /usr/local/etc/raddb/mods-enabled/attr_filter
attr_filter attr_filter.pre-proxy {
filename = "/usr/local/etc/raddb/mods-config/attr_filter/pre-proxy"
key = "%{Realm}"
relaxed = no
}
# Loading module "attr_filter.access_reject" from file /usr/local/etc/raddb/mods-enabled/attr_filter
attr_filter attr_filter.access_reject {
filename = "/usr/local/etc/raddb/mods-config/attr_filter/access_reject"
key = "%{User-Name}"
relaxed = no
}
# Loading module "attr_filter.access_challenge" from file /usr/local/etc/raddb/mods-enabled/attr_filter
attr_filter attr_filter.access_challenge {
filename = "/usr/local/etc/raddb/mods-config/attr_filter/access_challenge"
key = "%{User-Name}"
relaxed = no
}
# Loading module "attr_filter.accounting_response" from file /usr/local/etc/raddb/mods-enabled/attr_filter
attr_filter attr_filter.accounting_response {
filename = "/usr/local/etc/raddb/mods-config/attr_filter/accounting_response"
key = "%{User-Name}"
relaxed = no
}
# Loading module "attr_filter.coa" from file /usr/local/etc/raddb/mods-enabled/attr_filter
attr_filter attr_filter.coa {
filename = "/usr/local/etc/raddb/mods-config/attr_filter/coa"
key = "%{User-Name}"
relaxed = no
}
# Loaded module rlm_mschap
# Loading module "mschap" from file /usr/local/etc/raddb/mods-enabled/mschap
mschap {
use_mppe = yes
require_encryption = no
require_strong = no
with_ntdomain_hack = yes
passchange {
}
allow_retry = yes
winbind_retry_with_normalised_username = no
}
# Loaded module rlm_linelog
# Loading module "linelog" from file /usr/local/etc/raddb/mods-enabled/linelog
linelog {
filename = "/var/log/linelog"
escape_filenames = no
syslog_severity = "info"
permissions = 384
format = "This is a log message for %{User-Name}"
reference = "messages.%{%{reply:Packet-Type}:-default}"
}
# Loading module "log_accounting" from file /usr/local/etc/raddb/mods-enabled/linelog
linelog log_accounting {
filename = "/var/log/linelog-accounting"
escape_filenames = no
syslog_severity = "info"
permissions = 384
format = ""
reference = "Accounting-Request.%{%{Acct-Status-Type}:-unknown}"
}
# Loaded module rlm_detail
# Loading module "detail" from file /usr/local/etc/raddb/mods-enabled/detail
detail {
filename = "/var/log/radacct/%{%{Packet-Src-IP-Address}:-%{Packet-Src-IPv6-Address}}/detail-%Y%m%d"
header = "%t"
permissions = 384
locking = no
escape_filenames = no
log_packet_header = no
}
# Loaded module rlm_radutmp
# Loading module "radutmp" from file /usr/local/etc/raddb/mods-enabled/radutmp
radutmp {
filename = "/var/log/radutmp"
username = "%{User-Name}"
case_sensitive = yes
check_with_nas = yes
permissions = 384
caller_id = yes
}
# Loaded module rlm_unpack
# Loading module "unpack" from file /usr/local/etc/raddb/mods-enabled/unpack
# Loaded module rlm_exec
# Loading module "ntlm_auth" from file /usr/local/etc/raddb/mods-enabled/ntlm_auth
exec ntlm_auth {
wait = yes
program = "/path/to/ntlm_auth --request-nt-key --domain=MYDOMAIN --username=%{mschap:User-Name} --password=%{User-Password}"
shell_escape = yes
}
# Loaded module rlm_totp
# Loading module "totp" from file /usr/local/etc/raddb/mods-enabled/totp.pkgsave
# Loaded module rlm_dynamic_clients
# Loading module "dynamic_clients" from file /usr/local/etc/raddb/mods-enabled/dynamic_clients
# Loading module "echo" from file /usr/local/etc/raddb/mods-enabled/echo
exec echo {
wait = yes
program = "/bin/echo %{User-Name}"
input_pairs = "request"
output_pairs = "reply"
shell_escape = yes
}
# Loading module "exec" from file /usr/local/etc/raddb/mods-enabled/exec
exec {
wait = no
input_pairs = "request"
shell_escape = yes
timeout = 10
}
# Loaded module rlm_unix
# Loading module "unix" from file /usr/local/etc/raddb/mods-enabled/unix
unix {
radwtmp = "/var/log/radwtmp"
}
Creating attribute Unix-Group
# Loaded module rlm_preprocess
# Loading module "preprocess" from file /usr/local/etc/raddb/mods-enabled/preprocess
preprocess {
huntgroups = "/usr/local/etc/raddb/mods-config/preprocess/huntgroups"
hints = "/usr/local/etc/raddb/mods-config/preprocess/hints"
with_ascend_hack = no
ascend_channels_per_line = 23
with_ntdomain_hack = no
with_specialix_jetstream_hack = no
with_cisco_vsa_hack = no
with_alvarion_vsa_hack = no
}
# Loading module "sradutmp" from file /usr/local/etc/raddb/mods-enabled/sradutmp
radutmp sradutmp {
filename = "/var/log/sradutmp"
username = "%{User-Name}"
case_sensitive = yes
check_with_nas = yes
permissions = 420
caller_id = no
}
# Loaded module rlm_soh
# Loading module "soh" from file /usr/local/etc/raddb/mods-enabled/soh
soh {
dhcp = yes
}
# Loaded module rlm_expiration
# Loading module "expiration" from file /usr/local/etc/raddb/mods-enabled/expiration
# Loaded module rlm_logintime
# Loading module "logintime" from file /usr/local/etc/raddb/mods-enabled/logintime
logintime {
minimum_timeout = 60
}
# Loaded module rlm_passwd
# Loading module "etc_passwd" from file /usr/local/etc/raddb/mods-enabled/passwd
passwd etc_passwd {
filename = "/etc/passwd"
format = "*User-Name:Crypt-Password:"
delimiter = ":"
ignore_nislike = no
ignore_empty = yes
allow_multiple_keys = no
hash_size = 100
}
# Loaded module rlm_files
# Loading module "files" from file /usr/local/etc/raddb/mods-enabled/files
files {
filename = "/usr/local/etc/raddb/mods-config/files/authorize"
acctusersfile = "/usr/local/etc/raddb/mods-config/files/accounting"
preproxy_usersfile = "/usr/local/etc/raddb/mods-config/files/pre-proxy"
}
# Loaded module rlm_replicate
# Loading module "replicate" from file /usr/local/etc/raddb/mods-enabled/replicate
# Loading module "auth_log" from file /usr/local/etc/raddb/mods-enabled/detail.log
detail auth_log {
filename = "/var/log/radacct/%{%{Packet-Src-IP-Address}:-%{Packet-Src-IPv6-Address}}/auth-detail-%Y%m%d"
header = "%t"
permissions = 384
locking = no
escape_filenames = no
log_packet_header = no
}
# Loading module "reply_log" from file /usr/local/etc/raddb/mods-enabled/detail.log
detail reply_log {
filename = "/var/log/radacct/%{%{Packet-Src-IP-Address}:-%{Packet-Src-IPv6-Address}}/reply-detail-%Y%m%d"
header = "%t"
permissions = 384
locking = no
escape_filenames = no
log_packet_header = no
}
# Loading module "pre_proxy_log" from file /usr/local/etc/raddb/mods-enabled/detail.log
detail pre_proxy_log {
filename = "/var/log/radacct/%{%{Packet-Src-IP-Address}:-%{Packet-Src-IPv6-Address}}/pre-proxy-detail-%Y%m%d"
header = "%t"
permissions = 384
locking = no
escape_filenames = no
log_packet_header = no
}
# Loading module "post_proxy_log" from file /usr/local/etc/raddb/mods-enabled/detail.log
detail post_proxy_log {
filename = "/var/log/radacct/%{%{Packet-Src-IP-Address}:-%{Packet-Src-IPv6-Address}}/post-proxy-detail-%Y%m%d"
header = "%t"
permissions = 384
locking = no
escape_filenames = no
log_packet_header = no
}
# Loaded module rlm_chap
# Loading module "chap" from file /usr/local/etc/raddb/mods-enabled/chap
# Loaded module rlm_date
# Loading module "date" from file /usr/local/etc/raddb/mods-enabled/date
date {
format = "%b %e %Y %H:%M:%S %Z"
utc = no
}
# Loading module "wispr2date" from file /usr/local/etc/raddb/mods-enabled/date
date wispr2date {
format = "%Y-%m-%dT%H:%M:%S"
utc = no
}
# Loaded module rlm_counter
# Loading module "daily" from file /usr/local/etc/raddb/mods-enabled/counter
counter daily {
filename = "/usr/local/etc/raddb/db.daily"
key = "User-Name"
reset = "daily"
count_attribute = "Acct-Session-Time"
counter_name = "Daily-Session-Time"
check_name = "Max-Daily-Session"
reply_name = "Session-Timeout"
allowed_service_type = "Framed-User"
cache_size = 5000
}
# Loaded module rlm_realm
# Loading module "IPASS" from file /usr/local/etc/raddb/mods-enabled/realm
realm IPASS {
format = "prefix"
delimiter = "/"
ignore_default = no
ignore_null = no
}
# Loading module "suffix" from file /usr/local/etc/raddb/mods-enabled/realm
realm suffix {
format = "suffix"
delimiter = "@"
ignore_default = no
ignore_null = no
}
# Loading module "bangpath" from file /usr/local/etc/raddb/mods-enabled/realm
realm bangpath {
format = "prefix"
delimiter = "!"
ignore_default = no
ignore_null = no
}
# Loading module "realmpercent" from file /usr/local/etc/raddb/mods-enabled/realm
realm realmpercent {
format = "suffix"
delimiter = "%"
ignore_default = no
ignore_null = no
}
# Loading module "ntdomain" from file /usr/local/etc/raddb/mods-enabled/realm
realm ntdomain {
format = "prefix"
delimiter = "\\"
ignore_default = no
ignore_null = no
}
# Loaded module rlm_always
# Loading module "reject" from file /usr/local/etc/raddb/mods-enabled/always
always reject {
rcode = "reject"
simulcount = 0
mpp = no
}
# Loading module "fail" from file /usr/local/etc/raddb/mods-enabled/always
always fail {
rcode = "fail"
simulcount = 0
mpp = no
}
# Loading module "ok" from file /usr/local/etc/raddb/mods-enabled/always
always ok {
rcode = "ok"
simulcount = 0
mpp = no
}
# Loading module "handled" from file /usr/local/etc/raddb/mods-enabled/always
always handled {
rcode = "handled"
simulcount = 0
mpp = no
}
# Loading module "invalid" from file /usr/local/etc/raddb/mods-enabled/always
always invalid {
rcode = "invalid"
simulcount = 0
mpp = no
}
# Loading module "userlock" from file /usr/local/etc/raddb/mods-enabled/always
always userlock {
rcode = "userlock"
simulcount = 0
mpp = no
}
# Loading module "notfound" from file /usr/local/etc/raddb/mods-enabled/always
always notfound {
rcode = "notfound"
simulcount = 0
mpp = no
}
# Loading module "noop" from file /usr/local/etc/raddb/mods-enabled/always
always noop {
rcode = "noop"
simulcount = 0
mpp = no
}
# Loading module "updated" from file /usr/local/etc/raddb/mods-enabled/always
always updated {
rcode = "updated"
simulcount = 0
mpp = no
}
# Loaded module rlm_expr
# Loading module "expr" from file /usr/local/etc/raddb/mods-enabled/expr
expr {
safe_characters = "@abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ0123456789.-_: /äéöüàâæçèéêëîïôœùûüaÿÄÉÖÜßÀÂÆÇÈÉÊËÎÏÔŒÙÛÜŸ"
}
instantiate {
}
# Instantiating module "eap" from file /usr/local/etc/raddb/mods-enabled/eap
# Linked to sub-module rlm_eap_md5
# Linked to sub-module rlm_eap_gtc
gtc {
challenge = "Password: "
auth_type = "PAP"
}
# Linked to sub-module rlm_eap_tls
tls {
tls = "tls-common"
}
tls-config tls-common {
verify_depth = 0
ca_path = "/usr/local/etc/raddb/certs"
pem_file_type = yes
private_key_file = "/usr/local/etc/raddb/certs/cert_opn.pem"
certificate_file = "/usr/local/etc/raddb/certs/cert_opn.pem"
ca_file = "/usr/local/etc/raddb/certs/ca_opn.pem"
private_key_password = <<< secret >>>
dh_file = "/usr/local/etc/raddb/certs/dh"
fragment_size = 1024
include_length = yes
auto_chain = yes
check_crl = no
check_all_crl = no
ca_path_reload_interval = 0
cipher_list = "DEFAULT"
cipher_server_preference = no
ecdh_curve = "prime256v1"
tls_max_version = "1.2"
tls_min_version = "1.0"
cache {
enable = yes
lifetime = 24
max_entries = 255
}
verify {
skip_if_ocsp_ok = no
}
ocsp {
enable = no
override_cert_url = yes
url = "http://####IP-Address####/ocsp/"
use_nonce = yes
timeout = 0
softfail = no
}
}
tls: In order to use TLS 1.0 and/or TLS 1.1, you likely need to set: cipher_list = "DEFAULT@SECLEVEL=1"
# Linked to sub-module rlm_eap_ttls
ttls {
tls = "tls-common"
default_eap_type = "md5"
copy_request_to_tunnel = no
use_tunneled_reply = no
virtual_server = "inner-tunnel"
include_length = yes
require_client_cert = no
}
tls: Using cached TLS configuration from previous invocation
# Linked to sub-module rlm_eap_peap
peap {
tls = "tls-common"
default_eap_type = "mschapv2"
copy_request_to_tunnel = no
use_tunneled_reply = no
proxy_tunneled_request_as_eap = yes
virtual_server = "inner-tunnel"
soh = no
require_client_cert = no
}
tls: Using cached TLS configuration from previous invocation
# Linked to sub-module rlm_eap_mschapv2
mschapv2 {
with_ntdomain_hack = no
send_error = no
}
# Instantiating module "pap" from file /usr/local/etc/raddb/mods-enabled/pap
# Instantiating module "cache_eap" from file /usr/local/etc/raddb/mods-enabled/cache_eap
rlm_cache (cache_eap): Driver rlm_cache_rbtree (module rlm_cache_rbtree) loaded and linked
# Instantiating module "attr_filter.post-proxy" from file /usr/local/etc/raddb/mods-enabled/attr_filter
reading pairlist file /usr/local/etc/raddb/mods-config/attr_filter/post-proxy
# Instantiating module "attr_filter.pre-proxy" from file /usr/local/etc/raddb/mods-enabled/attr_filter
reading pairlist file /usr/local/etc/raddb/mods-config/attr_filter/pre-proxy
# Instantiating module "attr_filter.access_reject" from file /usr/local/etc/raddb/mods-enabled/attr_filter
reading pairlist file /usr/local/etc/raddb/mods-config/attr_filter/access_reject
# Instantiating module "attr_filter.access_challenge" from file /usr/local/etc/raddb/mods-enabled/attr_filter
reading pairlist file /usr/local/etc/raddb/mods-config/attr_filter/access_challenge
# Instantiating module "attr_filter.accounting_response" from file /usr/local/etc/raddb/mods-enabled/attr_filter
reading pairlist file /usr/local/etc/raddb/mods-config/attr_filter/accounting_response
# Instantiating module "attr_filter.coa" from file /usr/local/etc/raddb/mods-enabled/attr_filter
reading pairlist file /usr/local/etc/raddb/mods-config/attr_filter/coa
# Instantiating module "mschap" from file /usr/local/etc/raddb/mods-enabled/mschap
rlm_mschap (mschap): using internal authentication
# Instantiating module "linelog" from file /usr/local/etc/raddb/mods-enabled/linelog
# Instantiating module "log_accounting" from file /usr/local/etc/raddb/mods-enabled/linelog
# Instantiating module "detail" from file /usr/local/etc/raddb/mods-enabled/detail
# Instantiating module "preprocess" from file /usr/local/etc/raddb/mods-enabled/preprocess
reading pairlist file /usr/local/etc/raddb/mods-config/preprocess/huntgroups
reading pairlist file /usr/local/etc/raddb/mods-config/preprocess/hints
# Instantiating module "expiration" from file /usr/local/etc/raddb/mods-enabled/expiration
# Instantiating module "logintime" from file /usr/local/etc/raddb/mods-enabled/logintime
# Instantiating module "etc_passwd" from file /usr/local/etc/raddb/mods-enabled/passwd
rlm_passwd: nfields: 3 keyfield 0(User-Name) listable: no
# Instantiating module "files" from file /usr/local/etc/raddb/mods-enabled/files
reading pairlist file /usr/local/etc/raddb/mods-config/files/authorize
reading pairlist file /usr/local/etc/raddb/mods-config/files/accounting
reading pairlist file /usr/local/etc/raddb/mods-config/files/pre-proxy
# Instantiating module "auth_log" from file /usr/local/etc/raddb/mods-enabled/detail.log
rlm_detail (auth_log): 'User-Password' suppressed, will not appear in detail output
# Instantiating module "reply_log" from file /usr/local/etc/raddb/mods-enabled/detail.log
# Instantiating module "pre_proxy_log" from file /usr/local/etc/raddb/mods-enabled/detail.log
# Instantiating module "post_proxy_log" from file /usr/local/etc/raddb/mods-enabled/detail.log
# Instantiating module "daily" from file /usr/local/etc/raddb/mods-enabled/counter
rlm_counter: Current Time: 1633104335 [2021-10-01 18:05:35], Next reset 1633125600 [2021-10-02 00:00:00]
rlm_counter: add_defaults: Start
rlm_counter: DEFAULT1 set to 1633125600
rlm_counter: DEFAULT2 set to 1633104335
rlm_counter: add_defaults: End
# Instantiating module "IPASS" from file /usr/local/etc/raddb/mods-enabled/realm
# Instantiating module "suffix" from file /usr/local/etc/raddb/mods-enabled/realm
# Instantiating module "bangpath" from file /usr/local/etc/raddb/mods-enabled/realm
# Instantiating module "realmpercent" from file /usr/local/etc/raddb/mods-enabled/realm
# Instantiating module "ntdomain" from file /usr/local/etc/raddb/mods-enabled/realm
# Instantiating module "reject" from file /usr/local/etc/raddb/mods-enabled/always
# Instantiating module "fail" from file /usr/local/etc/raddb/mods-enabled/always
# Instantiating module "ok" from file /usr/local/etc/raddb/mods-enabled/always
# Instantiating module "handled" from file /usr/local/etc/raddb/mods-enabled/always
# Instantiating module "invalid" from file /usr/local/etc/raddb/mods-enabled/always
# Instantiating module "userlock" from file /usr/local/etc/raddb/mods-enabled/always
# Instantiating module "notfound" from file /usr/local/etc/raddb/mods-enabled/always
# Instantiating module "noop" from file /usr/local/etc/raddb/mods-enabled/always
# Instantiating module "updated" from file /usr/local/etc/raddb/mods-enabled/always
} # modules
radiusd: #### Loading Virtual Servers ####
server { # from file /usr/local/etc/raddb/radiusd.conf
} # server
server inner-tunnel { # from file /usr/local/etc/raddb/sites-enabled/inner-tunnel
# Loading authenticate {...}
Compiling Auth-Type PAP for attr Auth-Type
Compiling Auth-Type CHAP for attr Auth-Type
Compiling Auth-Type MS-CHAP for attr Auth-Type
# Loading authorize {...}
Ignoring "sql" (see raddb/mods-available/README.rst)
Ignoring "ldap" (see raddb/mods-available/README.rst)
# Loading session {...}
# Loading post-proxy {...}
# Loading post-auth {...}
# Skipping contents of 'if' as it is always 'false' -- /usr/local/etc/raddb/sites-enabled/inner-tunnel:330
Compiling Post-Auth-Type REJECT for attr Post-Auth-Type
} # server inner-tunnel
server default { # from file /usr/local/etc/raddb/sites-enabled/default
# Loading authenticate {...}
Compiling Auth-Type PAP for attr Auth-Type
Compiling Auth-Type CHAP for attr Auth-Type
Compiling Auth-Type MS-CHAP for attr Auth-Type
# Loading authorize {...}
# Loading preacct {...}
# Loading accounting {...}
# Loading post-proxy {...}
# Loading post-auth {...}
Compiling Post-Auth-Type REJECT for attr Post-Auth-Type
Compiling Post-Auth-Type Challenge for attr Post-Auth-Type
} # server default
server check-eap-tls { # from file /usr/local/etc/raddb/sites-enabled/check-eap-tls
# Loading authorize {...}
} # server check-eap-tls
radiusd: #### Opening IP addresses and Ports ####
listen {
type = "auth"
ipaddr = ####IP-Address####
port = 18120
}
listen {
type = "auth"
ipaddr = *
port = 0
limit {
max_connections = 16
lifetime = 0
idle_timeout = 30
}
}
listen {
type = "acct"
ipaddr = *
port = 0
limit {
max_connections = 16
lifetime = 0
idle_timeout = 30
}
}
listen {
type = "auth"
ipv6addr = ::
port = 0
limit {
max_connections = 16
lifetime = 0
idle_timeout = 30
}
}
listen {
type = "acct"
ipv6addr = ::
port = 0
limit {
max_connections = 16
lifetime = 0
idle_timeout = 30
}
}
Listening on auth address ####IP-Address#### port 18120 bound to server inner-tunnel
Listening on auth address * port 1812 bound to server default
Listening on acct address * port 1813 bound to server default
Listening on auth address :: port 1812 bound to server default
Listening on acct address :: port 1813 bound to server default
Listening on proxy address * port 59509
Listening on proxy address :: port 54627
Ready to process requests
(0) Received Access-Request Id 51 from ####IP-Address####:60698 to ####IP-Address####:1812 length 213
(0) User-Name = "####USERNAME####"
(0) NAS-Identifier = "####SSID####"
(0) Called-Station-Id = "####MAC-ADDRESS####:####SSID####"
(0) NAS-Port-Type = Wireless-802.11
(0) Service-Type = Framed-User
(0) Calling-Station-Id = "####MAC-ADDRESS####"
(0) Connect-Info = "CONNECT 0Mbps 802.11b"
(0) Acct-Session-Id = "397B490BA728083F"
(0) Acct-Multi-Session-Id = "D34F457391B9BB9B"
(0) WLAN-Pairwise-Cipher = 1027076
(0) WLAN-Group-Cipher = 1027076
(0) WLAN-AKM-Suite = 1027077
(0) WLAN-Group-Mgmt-Cipher = 1027078
(0) Framed-MTU = 1400
(0) EAP-Message = 0x02730007016a6d
(0) Message-Authenticator = ####Message-Authenticator####
(0) # Executing section authorize from file /usr/local/etc/raddb/sites-enabled/default
(0) authorize {
(0) policy filter_username {
(0) if (&User-Name) {
(0) if (&User-Name) -> TRUE
(0) if (&User-Name) {
(0) if (&User-Name =~ / /) {
(0) if (&User-Name =~ / /) -> FALSE
(0) if (&User-Name =~ /@[^@]*@/ ) {
(0) if (&User-Name =~ /@[^@]*@/ ) -> FALSE
(0) if (&User-Name =~ /\.\./ ) {
(0) if (&User-Name =~ /\.\./ ) -> FALSE
(0) if ((&User-Name =~ /@/) && (&User-Name !~ /@(.+)\.(.+)$/)) {
(0) if ((&User-Name =~ /@/) && (&User-Name !~ /@(.+)\.(.+)$/)) -> FALSE
(0) if (&User-Name =~ /\.$/) {
(0) if (&User-Name =~ /\.$/) -> FALSE
(0) if (&User-Name =~ /@\./) {
(0) if (&User-Name =~ /@\./) -> FALSE
(0) } # if (&User-Name) = notfound
(0) } # policy filter_username = notfound
(0) [preprocess] = ok
(0) [chap] = noop
(0) [mschap] = noop
(0) [digest] = noop
(0) suffix: Checking for suffix after "@"
(0) suffix: No '@' in User-Name = "####USERNAME####", looking up realm NULL
(0) suffix: No such realm "NULL"
(0) [suffix] = noop
(0) eap: Peer sent EAP Response (code 2) ID 115 length 7
(0) eap: EAP-Identity reply, returning 'ok' so we can short-circuit the rest of authorize
(0) [eap] = ok
(0) } # authorize = ok
(0) Found Auth-Type = eap
(0) # Executing group from file /usr/local/etc/raddb/sites-enabled/default
(0) authenticate {
(0) eap: Peer sent packet with method EAP Identity (1)
(0) eap: Calling submodule eap_mschapv2 to process data
(0) eap_mschapv2: Issuing Challenge
(0) eap: Sending EAP Request (code 1) ID 116 length 43
(0) eap: EAP session adding &reply:State = 0xa52dae39a559b480
(0) [eap] = handled
(0) } # authenticate = handled
(0) Using Post-Auth-Type Challenge
(0) # Executing group from file /usr/local/etc/raddb/sites-enabled/default
(0) Challenge { ... } # empty sub-section is ignored
(0) Sent Access-Challenge Id 51 from ####IP-Address####:1812 to ####IP-Address####:60698 length 0
(0) EAP-Message = 0x0174002b1a01740026104341c6857ac084c511900ba8980aeede667265657261646975732d332e302e3233
(0) Message-Authenticator = ####Message-Authenticator####
(0) State = 0xa52dae39a559b4805cfddc5abd8542c5
(0) Finished request
Waking up in 4.9 seconds.
(1) Received Access-Request Id 52 from ####IP-Address####:60698 to ####IP-Address####:1812 length 231
(1) User-Name = "####USERNAME####"
(1) NAS-Identifier = "####SSID####"
(1) Called-Station-Id = "####MAC-ADDRESS####:####SSID####"
(1) NAS-Port-Type = Wireless-802.11
(1) Service-Type = Framed-User
(1) Calling-Station-Id = "####MAC-ADDRESS####"
(1) Connect-Info = "CONNECT 0Mbps 802.11b"
(1) Acct-Session-Id = "397B490BA728083F"
(1) Acct-Multi-Session-Id = "D34F457391B9BB9B"
(1) WLAN-Pairwise-Cipher = 1027076
(1) WLAN-Group-Cipher = 1027076
(1) WLAN-AKM-Suite = 1027077
(1) WLAN-Group-Mgmt-Cipher = 1027078
(1) Framed-MTU = 1400
(1) EAP-Message = 0x02740007031915
(1) State = 0xa52dae39a559b4805cfddc5abd8542c5
(1) Message-Authenticator = ####Message-Authenticator####
(1) session-state: No cached attributes
(1) # Executing section authorize from file /usr/local/etc/raddb/sites-enabled/default
(1) authorize {
(1) policy filter_username {
(1) if (&User-Name) {
(1) if (&User-Name) -> TRUE
(1) if (&User-Name) {
(1) if (&User-Name =~ / /) {
(1) if (&User-Name =~ / /) -> FALSE
(1) if (&User-Name =~ /@[^@]*@/ ) {
(1) if (&User-Name =~ /@[^@]*@/ ) -> FALSE
(1) if (&User-Name =~ /\.\./ ) {
(1) if (&User-Name =~ /\.\./ ) -> FALSE
(1) if ((&User-Name =~ /@/) && (&User-Name !~ /@(.+)\.(.+)$/)) {
(1) if ((&User-Name =~ /@/) && (&User-Name !~ /@(.+)\.(.+)$/)) -> FALSE
(1) if (&User-Name =~ /\.$/) {
(1) if (&User-Name =~ /\.$/) -> FALSE
(1) if (&User-Name =~ /@\./) {
(1) if (&User-Name =~ /@\./) -> FALSE
(1) } # if (&User-Name) = notfound
(1) } # policy filter_username = notfound
(1) [preprocess] = ok
(1) [chap] = noop
(1) [mschap] = noop
(1) [digest] = noop
(1) suffix: Checking for suffix after "@"
(1) suffix: No '@' in User-Name = "####USERNAME####", looking up realm NULL
(1) suffix: No such realm "NULL"
(1) [suffix] = noop
(1) eap: Peer sent EAP Response (code 2) ID 116 length 7
(1) eap: No EAP Start, assuming it's an on-going EAP conversation
(1) [eap] = updated
(1) files: users: Matched entry ####USERNAME#### at line 2
(1) [files] = ok
(1) [expiration] = noop
(1) [logintime] = noop
(1) pap: WARNING: Auth-Type already set. Not setting to PAP
(1) [pap] = noop
(1) } # authorize = updated
(1) Found Auth-Type = eap
(1) # Executing group from file /usr/local/etc/raddb/sites-enabled/default
(1) authenticate {
(1) eap: Expiring EAP session with state 0xa52dae39a559b480
(1) eap: Finished EAP session with state 0xa52dae39a559b480
(1) eap: Previous EAP request found for state 0xa52dae39a559b480, released from the list
(1) eap: Peer sent packet with method EAP NAK (3)
(1) eap: Found mutually acceptable type PEAP (25)
(1) eap: Calling submodule eap_peap to process data
(1) eap_peap: (TLS) Initiating new session
(1) eap: Sending EAP Request (code 1) ID 117 length 6
(1) eap: EAP session adding &reply:State = 0xa52dae39a458b780
(1) [eap] = handled
(1) } # authenticate = handled
(1) Using Post-Auth-Type Challenge
(1) # Executing group from file /usr/local/etc/raddb/sites-enabled/default
(1) Challenge { ... } # empty sub-section is ignored
(1) session-state: Saving cached attributes
(1) Framed-MTU = 994
(1) Sent Access-Challenge Id 52 from ####IP-Address####:1812 to ####IP-Address####:60698 length 0
(1) Framed-Protocol = PPP
(1) EAP-Message = 0x017500061920
(1) Message-Authenticator = ####Message-Authenticator####
(1) State = 0xa52dae39a458b7805cfddc5abd8542c5
(1) Finished request
Waking up in 4.9 seconds.
(2) Received Access-Request Id 53 from ####IP-Address####:60698 to ####IP-Address####:1812 length 396
(2) User-Name = "####USERNAME####"
(2) NAS-Identifier = "####SSID####"
(2) Called-Station-Id = "####MAC-ADDRESS####:####SSID####"
(2) NAS-Port-Type = Wireless-802.11
(2) Service-Type = Framed-User
(2) Calling-Station-Id = "####MAC-ADDRESS####"
(2) Connect-Info = "CONNECT 0Mbps 802.11b"
(2) Acct-Session-Id = "397B490BA728083F"
(2) Acct-Multi-Session-Id = "D34F457391B9BB9B"
(2) WLAN-Pairwise-Cipher = 1027076
(2) WLAN-Group-Cipher = 1027076
(2) WLAN-AKM-Suite = 1027077
(2) WLAN-Group-Mgmt-Cipher = 1027078
(2) Framed-MTU = 1400
(2) EAP-Message = 0x027500ac1980000000a2160303009d010000990303615731da2e96b84114b4906f6757362c4de387209786dc805a8aa307d1521a6a00002ac02cc02bc030c02f009f009ec024c023c028c027c00ac009c014c013009d009c003d003c0035002f000a01000046000500050100000000000a00080006001d00170018000b00020100000d001a00180804080508060401050102010403050302030202060106030023000000170000ff01000100
(2) State = 0xa52dae39a458b7805cfddc5abd8542c5
(2) Message-Authenticator = ####Message-Authenticator####
(2) Restoring &session-state
(2) &session-state:Framed-MTU = 994
(2) # Executing section authorize from file /usr/local/etc/raddb/sites-enabled/default
(2) authorize {
(2) policy filter_username {
(2) if (&User-Name) {
(2) if (&User-Name) -> TRUE
(2) if (&User-Name) {
(2) if (&User-Name =~ / /) {
(2) if (&User-Name =~ / /) -> FALSE
(2) if (&User-Name =~ /@[^@]*@/ ) {
(2) if (&User-Name =~ /@[^@]*@/ ) -> FALSE
(2) if (&User-Name =~ /\.\./ ) {
(2) if (&User-Name =~ /\.\./ ) -> FALSE
(2) if ((&User-Name =~ /@/) && (&User-Name !~ /@(.+)\.(.+)$/)) {
(2) if ((&User-Name =~ /@/) && (&User-Name !~ /@(.+)\.(.+)$/)) -> FALSE
(2) if (&User-Name =~ /\.$/) {
(2) if (&User-Name =~ /\.$/) -> FALSE
(2) if (&User-Name =~ /@\./) {
(2) if (&User-Name =~ /@\./) -> FALSE
(2) } # if (&User-Name) = notfound
(2) } # policy filter_username = notfound
(2) [preprocess] = ok
(2) [chap] = noop
(2) [mschap] = noop
(2) [digest] = noop
(2) suffix: Checking for suffix after "@"
(2) suffix: No '@' in User-Name = "####USERNAME####", looking up realm NULL
(2) suffix: No such realm "NULL"
(2) [suffix] = noop
(2) eap: Peer sent EAP Response (code 2) ID 117 length 172
(2) eap: Continuing tunnel setup
(2) [eap] = ok
(2) } # authorize = ok
(2) Found Auth-Type = eap
(2) # Executing group from file /usr/local/etc/raddb/sites-enabled/default
(2) authenticate {
(2) eap: Expiring EAP session with state 0xa52dae39a458b780
(2) eap: Finished EAP session with state 0xa52dae39a458b780
(2) eap: Previous EAP request found for state 0xa52dae39a458b780, released from the list
(2) eap: Peer sent packet with method EAP PEAP (25)
(2) eap: Calling submodule eap_peap to process data
(2) eap_peap: (TLS) EAP Peer says that the final record size will be 162 bytes
(2) eap_peap: (TLS) EAP Got all data (162 bytes)
(2) eap_peap: (TLS) Handshake state - before SSL initialization
(2) eap_peap: (TLS) Handshake state - Server before SSL initialization
(2) eap_peap: (TLS) Handshake state - Server before SSL initialization
(2) eap_peap: (TLS) recv TLS 1.3 Handshake, ClientHello
(2) eap_peap: (TLS) send TLS 1.2 Alert, fatal handshake_failure
(2) eap_peap: ERROR: (TLS) Alert write:fatal:handshake failure
(2) eap_peap: ERROR: (TLS) Server : Error in error
(2) eap_peap: ERROR: (TLS) Failed reading from OpenSSL: error:1417A0C1:SSL routines:tls_post_process_client_hello:no shared cipher
(2) eap_peap: ERROR: (TLS) System call (I/O) error (-1)
(2) eap_peap: ERROR: (TLS) EAP Receive handshake failed during operation
(2) eap_peap: ERROR: [eaptls process] = fail
(2) eap: ERROR: Failed continuing EAP PEAP (25) session. EAP sub-module failed
(2) eap: Sending EAP Failure (code 4) ID 117 length 4
(2) eap: Failed in EAP select
(2) [eap] = invalid
(2) } # authenticate = invalid
(2) Failed to authenticate the user
(2) Using Post-Auth-Type Reject
(2) # Executing group from file /usr/local/etc/raddb/sites-enabled/default
(2) Post-Auth-Type REJECT {
(2) attr_filter.access_reject: EXPAND %{User-Name}
(2) attr_filter.access_reject: --> ####USERNAME####
(2) attr_filter.access_reject: Matched entry DEFAULT at line 11
(2) [attr_filter.access_reject] = updated
(2) [eap] = noop
(2) policy remove_reply_message_if_eap {
(2) if (&reply:EAP-Message && &reply:Reply-Message) {
(2) if (&reply:EAP-Message && &reply:Reply-Message) -> FALSE
(2) else {
(2) [noop] = noop
(2) } # else = noop
(2) } # policy remove_reply_message_if_eap = noop
(2) } # Post-Auth-Type REJECT = updated
(2) Login incorrect (eap_peap: (TLS) Alert write:fatal:handshake failure): [####USERNAME####/<via Auth-Type = eap>] (from client WLAN port 0 cli ####MAC-ADDRESS####)
(2) Delaying response for 1.000000 seconds
Waking up in 0.3 seconds.
Waking up in 0.6 seconds.
(2) Sending delayed response
(2) Sent Access-Reject Id 53 from ####IP-Address####:1812 to ####IP-Address####:60698 length 44
(2) EAP-Message = 0x04750004
(2) Message-Authenticator = ####Message-Authenticator####
Waking up in 3.9 seconds.
(0) Cleaning up request packet ID 51 with timestamp +11
(1) Cleaning up request packet ID 52 with timestamp +11
(2) Cleaning up request packet ID 53 with timestamp +11
Ready to process requests
#13
21.7 Legacy Series / Re: FreeRadius - error:14094419:SSL routines:ssl3_read_bytes:tlsv1 alert access deni
October 01, 2021, 10:05:56 AM
It worked after i've installed
But i still can not connect to wifi.
Code Select
pkg add -f https://pkg.opnsense.org/FreeBSD:12:amd64/21.1/MINT/21.1.6/OpenSSL/All/openldap-sasl-client-2.4.58.txzBut i still can not connect to wifi.
#14
21.7 Legacy Series / Re: FreeRadius - error:14094419:SSL routines:ssl3_read_bytes:tlsv1 alert access deni
September 30, 2021, 05:10:40 PM
Still the same error in debug output:
Code Select
(6) eap: Peer sent packet with method EAP PEAP (25)
(6) eap: Calling submodule eap_peap to process data
(6) eap_peap: (TLS) EAP Peer says that the final record size will be 31 bytes
(6) eap_peap: (TLS) EAP Got all data (31 bytes)
(6) eap_peap: (TLS) recv TLS 1.2 Alert, fatal access_denied
(6) eap_peap: ERROR: (TLS) Alert read:fatal:access denied
(6) eap_peap: ERROR: (TLS) Error in fragmentation logic - code 1
(6) eap_peap: ERROR: (TLS) Failed reading application data from OpenSSL: error:14094419:SSL routines:ssl3_read_bytes:tlsv1 alert access denied
(6) eap_peap: ERROR: [eaptls process] = fail
(6) eap: ERROR: Failed continuing EAP PEAP (25) session. EAP sub-module failed
#15
21.7 Legacy Series / Re: FreeRadius - error:14094419:SSL routines:ssl3_read_bytes:tlsv1 alert access deni
September 30, 2021, 04:58:56 PM
I've edited /usr/local/etc/raddb/mods-available/eap:
But the problem is still there.
Code Select
tls_min_version = "1.0"
tls_max_version = "1.2"
cipher_list = "DEFAULT@SECLEVEL=1"
But the problem is still there.

 "
"