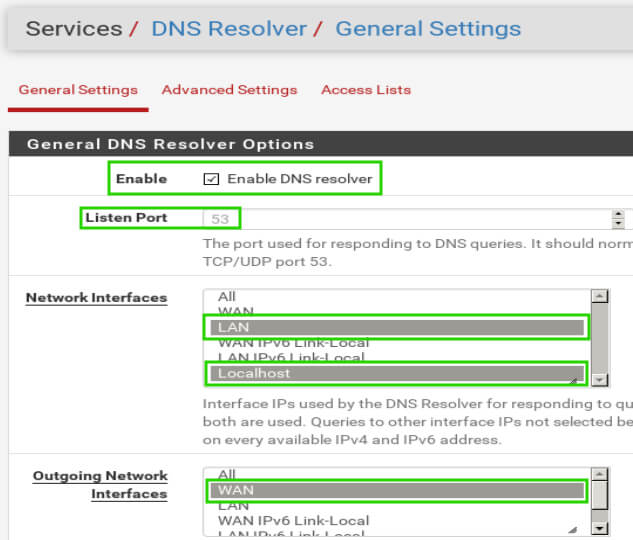
Hello,
Yes you are right,
but
Risk of DNS leacks is that your private information (browsing) is sent to someone you don't want.
That being said there is quite a different risk:
- DNS request sent directly to the WAN. The operation said before protect of that.
- DNS request intercepted on internet and sent to DNS you don't want. Some (rare) internet provider do that (https://www.dnsleaktest.com/what-is-transparent-dns-proxy.html). Only current protection i see is ....confidence I have in my DNS provider. I don't like that but i don't see other way to protect (?)
- DNS request sent to another DNS provider because of internal coding of DNS in sofware. That is what i want to prevent with the 2 new rules. Otherwise the DNS request is sent to tunnel and finaly goes to ...google DNS in this case (but could be a hacker dns or a state dns...) . one could said, ok this is right but google DNS receive your information through IP of VPN so no way to connect to your identity. That's true for IP. But due to various technics that are currently use widely on internet (fingerprint...) this add a risk to finaly have confidentiality issue. We could also take the issue in the other side : What is your benefit to use a DNS you don't want ? Nothing for me. Or at least functionnality (DNS fail over officialy ?) i don't want compare to confidentiality risk. So i block it. This is some kind of security "best practice" like when don't open ports we don't need on firewalls...
Yes you are right,
but
Risk of DNS leacks is that your private information (browsing) is sent to someone you don't want.
That being said there is quite a different risk:
- DNS request sent directly to the WAN. The operation said before protect of that.
- DNS request intercepted on internet and sent to DNS you don't want. Some (rare) internet provider do that (https://www.dnsleaktest.com/what-is-transparent-dns-proxy.html). Only current protection i see is ....confidence I have in my DNS provider. I don't like that but i don't see other way to protect (?)
- DNS request sent to another DNS provider because of internal coding of DNS in sofware. That is what i want to prevent with the 2 new rules. Otherwise the DNS request is sent to tunnel and finaly goes to ...google DNS in this case (but could be a hacker dns or a state dns...) . one could said, ok this is right but google DNS receive your information through IP of VPN so no way to connect to your identity. That's true for IP. But due to various technics that are currently use widely on internet (fingerprint...) this add a risk to finaly have confidentiality issue. We could also take the issue in the other side : What is your benefit to use a DNS you don't want ? Nothing for me. Or at least functionnality (DNS fail over officialy ?) i don't want compare to confidentiality risk. So i block it. This is some kind of security "best practice" like when don't open ports we don't need on firewalls...

 "
"